Hello Guys,
I am new with both vyos and sonicwall and I just wanted to ask for your help to establish the site-to-site vpn for both.
Thanks in advance.
More power to you all
The config for vyos is
set firewall name Accept default-action ‘accept’
set firewall name OutsideIn default-action ‘accept’
set firewall name OutsideIn rule 10 action ‘accept’
set firewall name OutsideIn rule 10 destination address ‘172.24.0.0/16’
set firewall name OutsideIn rule 10 source address ‘10.8.5.0/24’
set firewall name OutsideIn rule 20 action ‘accept’
set firewall name OutsideIn rule 20 destination address ‘10.8.5.0/24’
set firewall name OutsideIn rule 20 source address ‘172.24.0.0/16’
set nat source rule 110 description ‘Internal to Expeditors’
set nat source rule 110 destination address ‘10.254.72.0/24’
set nat source rule 110 outbound-interface ‘any’
set nat source rule 110 source address ‘172.24.0.16/28’
set nat source rule 110 translation address ‘52.11.46.101’
set nat source rule 120 destination address ‘10.0.0.0/8’
set nat source rule 120 outbound-interface ‘eth0’
set nat source rule 120 source address ‘172.24.0.16/28’
set nat source rule 120 translation address ‘172.24.0.16/28’
set nat source rule 122 destination address ‘172.16.0.0/12’
set nat source rule 122 outbound-interface ‘eth0’
set nat source rule 122 source address ‘172.24.0.16/28’
set nat source rule 122 translation address ‘172.24.0.16/28’
set nat source rule 124 destination address ‘192.168.0.0/16’
set nat source rule 124 outbound-interface ‘eth0’
set nat source rule 124 source address ‘172.24.0.16/28’
set nat source rule 124 translation address ‘172.24.0.16/28’
set nat source rule 130 destination address ‘72.44.234.120’
set nat source rule 130 outbound-interface ‘eth0’
set nat source rule 130 source address ‘172.24.0.28/32’
set nat source rule 130 translation address ‘masquerade’
set nat source rule 132 destination address ‘0.0.0.0/0’
set nat source rule 132 outbound-interface ‘eth0’
set nat source rule 132 source address ‘172.24.0.16/28’
set nat source rule 132 translation address ‘masquerade’
set protocols static route 0.0.0.0/0 next-hop 172.24.0.17 distance ‘250’
set vpn ipsec esp-group toVgScdEsp compression ‘disable’
set vpn ipsec esp-group toVgScdEsp lifetime ‘28800’
set vpn ipsec esp-group toVgScdEsp mode ‘tunnel’
set vpn ipsec esp-group toVgScdEsp pfs ‘disable’
set vpn ipsec esp-group toVgScdEsp proposal 1 encryption ‘aes256’
set vpn ipsec esp-group toVgScdEsp proposal 1 hash ‘sha1’
set vpn ipsec ike-group toVgScdIke key-exchange ‘ikev1’
set vpn ipsec ike-group toVgScdIke lifetime ‘86400’
set vpn ipsec ike-group toVgScdIke proposal 1 dh-group ‘2’
set vpn ipsec ike-group toVgScdIke proposal 1 encryption ‘aes256’
set vpn ipsec ike-group toVgScdIke proposal 1 hash ‘sha1’
set vpn ipsec ike-group toVgScdIke proposal 2 encryption ‘3des’
set vpn ipsec ike-group toVgScdIke proposal 2 hash ‘md5’
set vpn ipsec ipsec-interfaces interface ‘eth0’
set vpn ipsec ipsec-interfaces interface ‘eth1’
set vpn ipsec site-to-site peer X.X.X.X authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer X.X.X.X authentication pre-shared-secret ‘PRESHARED_SAMPLE’
set vpn ipsec site-to-site peer X.X.X.X connection-type ‘initiate’
set vpn ipsec site-to-site peer X.X.X.X description ‘Company_Nurse’
set vpn ipsec site-to-site peer X.X.X.X ike-group ‘toVgScdIke’
set vpn ipsec site-to-site peer X.X.X.X local-address ‘172.24.0.4’
set vpn ipsec site-to-site peer X.X.X.X tunnel 0 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer X.X.X.X tunnel 0 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer X.X.X.X tunnel 0 esp-group ‘toVgScdEsp’
set vpn ipsec site-to-site peer X.X.X.X tunnel 0 local prefix ‘172.24.0.16/28’
set vpn ipsec site-to-site peer X.X.X.X tunnel 0 remote prefix ‘10.127.31.0/24’
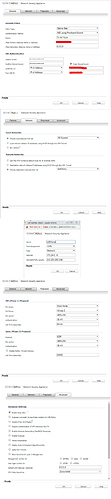
and settings in Sonicwall is
The logs I see in vyos is
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19955: max number of retransmissions (2) reached STATE_MAIN_I3. Possible authentication failure: no acceptable response to our first encrypted message
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19955: starting keying attempt 10 of an unlimited number
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: initiating Main Mode to replace #19955
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: ignoring Vendor ID payload [5b362bc820f60007]
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: ignoring Vendor ID payload [404bf439522ca3f6]
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: received Vendor ID payload [XAUTH]
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: received Vendor ID payload [Dead Peer Detection]
Mar 15 01:36:16 VyOS-AMI pluto[2848]: “peer-X.X.X.X-tunnel-0” #19957: ignoring informational payload, type INVALID_ID_INFORMATION