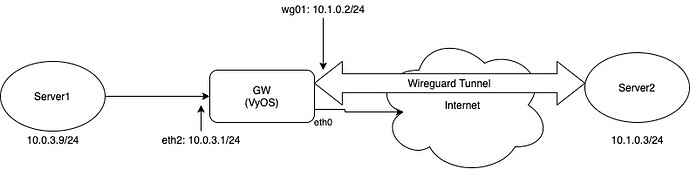
Dump is from GW, any interface, only ICMP. Server2 know about network
Routes from s2:
10.1.0.0/24 dev wg1 proto kernel scope link src 10.1.0.3
10.0.3.0/24 dev wg1 scope link
Routes from GW:
vyos@gw# ip route list
default nhid 32 via xxxxxxx dev eth0 proto static metric 20
xxxxxx dev eth0 proto kernel scope link src xxxxx
10.0.3.0/24 dev eth2 proto kernel scope link src 10.0.3.1
10.1.0.0/24 dev wg02 proto kernel scope link src 10.1.0.2
From both servers ping arrive to GW
WG config on s2:
[Interface]
Address = 10.1.0.3/24
ListenPort = 51821
PrivateKey = xxxxx
[Peer]
Endpoint = xxxxxx:51821
PublicKey = xxxx
AllowedIPs = 10.1.0.2/32, 10.0.3.0/24
PersistentKeepalive = 5
WG config on GW:
set interfaces wireguard wg02 address '10.1.0.2/24'
set interfaces wireguard wg02 description 'VPN wg02'
set interfaces wireguard wg02 peer s2 address 'xxxxxx'
set interfaces wireguard wg02 peer s2 allowed-ips '10.1.0.3/32'
set interfaces wireguard wg02 peer s2 port '51821'
set interfaces wireguard wg02 peer s2 pubkey 'xxxxx'
set interfaces wireguard wg02 port '51821'
set interfaces wireguard wg02 private-key 'wg02'
Ping from s1 (on eth2):
vyos@gw# sudo tcpdump -i eth2 icmp -vv
tcpdump: listening on eth2, link-type EN10MB (Ethernet), capture size 262144 bytes
13:23:38.923351 IP (tos 0x0, ttl 64, id 47410, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.3.9 > 10.1.0.3: ICMP echo request, id 31, seq 1, length 64
13:23:39.928243 IP (tos 0x0, ttl 64, id 47426, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.3.9 > 10.1.0.3: ICMP echo request, id 31, seq 2, length 64
Ping from s2 (internet on eth0, wg02):
vyos@gw# sudo tcpdump -i eth0 icmp -vv
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:23:49.477406 IP (tos 0x0, ttl 63, id 7786, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.0.3 > 10.0.3.9: ICMP echo request, id 94, seq 1, length 64
13:23:50.505948 IP (tos 0x0, ttl 63, id 7797, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.0.3 > 10.0.3.9: ICMP echo request, id 94, seq 2, length 64
vyos@gw# sudo tcpdump -i wg02 icmp -vv
tcpdump: listening on wg02, link-type RAW (Raw IP), capture size 262144 bytes
13:24:03.788424 IP (tos 0x0, ttl 64, id 9916, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.0.3 > 10.0.3.9: ICMP echo request, id 95, seq 1, length 64
13:24:04.809904 IP (tos 0x0, ttl 64, id 9973, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.0.3 > 10.0.3.9: ICMP echo request, id 95, seq 2, length 64