Hello,
this is my first post (and this my first approach with VyOS on a cloud instance).
I have two cloud instance on same private subnet (10.50.0.0/24) :
- VyOS : 10.50.0.1
- Debian Machine: 10.50.0.2
Both clean install. After a Quick Start, VyOS can ping Debian and vice-versa.
Step 2:
VPN IPSEC
-
EdgeOS (ER-X):
Subnet 192.168.10.0/24
eth0: WAN (router IP - Dynamic Public NATed IP)
switch0 [eth1,eth2, eth3, eth4] (192.168.10.1)
initiator
-
VyOS (Cloud):
Subnet 10.50.0.0/24
eth0: WAN (Public Static Transparent IP)
eth1: 10.50.0.1
For both solution I’ve used a domain name (DDNS for ER-X, DNS for VyOS)
VPN goes UP
…and here comes the fun part.
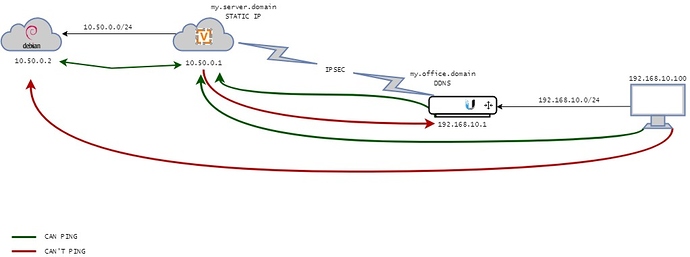
Ping from 10.50.0.1 (VyOS) to 10.50.0.2 (Debian) OK
Ping from 192.168.10.0/24 (ER-X) to 10.50.0.1 (VyOS) OK
Ping from 192.168.10.0/24 (ER-X) to 10.50.0.2 (Debian) KO
Ping from 10.50.0.1 (VyOS) to 192.168.10.1 (ER-X) KO
Traceroute from 10.50.0.1 to 192.168.10.1 routes traffic direcly on WAN eth0 instead to use tunnel
Here’s my conf:
firewall {
all-ping enable
broadcast-ping disable
config-trap disable
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name WAN_IN {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
}
name WAN_LOCAL {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
rule 20 {
action accept
icmp {
type-name echo-request
}
protocol icmp
state {
new enable
}
}
rule 30 {
action drop
destination {
port 22
}
protocol tcp
recent {
count 4
time 60
}
state {
new enable
}
}
rule 31 {
action accept
destination {
port 22
}
protocol tcp
state {
new enable
}
}
rule 32 {
action accept
source {
address 192.168.10.0/24
}
}
rule 40 {
action accept
protocol esp
}
rule 41 {
action accept
destination {
port 500
}
protocol udp
}
rule 42 {
action accept
destination {
port 4500
}
protocol udp
}
rule 43 {
action accept
destination {
port 1701
}
ipsec {
match-ipsec
}
protocol udp
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
twa-hazards-protection disable
}
interfaces {
ethernet eth0 {
address dhcp
description Internet
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
}
hw-id 00:50:56:35:46:8e
}
ethernet eth1 {
address 10.50.0.1/24
description Local
hw-id 00:50:56:33:98:99
}
loopback lo {
}
}
nat {
source {
rule 10 {
destination {
address 192.168.10.0/24
}
exclude
outbound-interface eth0
source {
address 10.50.0.0/24
}
}
rule 100 {
outbound-interface eth0
source {
address 10.50.0.0/24
}
translation {
address masquerade
}
}
}
}
service {
dns {
forwarding {
allow-from 10.50.0.0/24
cache-size 0
listen-address 10.50.0.1
}
}
ssh {
port 22
}
}
vpn {
ipsec {
esp-group office-srv-esp {
compression disable
lifetime 1800
mode tunnel
pfs enable
proposal 1 {
encryption aes256
hash sha1
}
}
ike-group office-srv-ike {
close-action none
ikev2-reauth no
key-exchange ikev1
lifetime 3600
proposal 1 {
dh-group 2
encryption aes256
hash sha1
}
}
site-to-site {
peer my.office.domain {
authentication {
id my.server.domain
mode pre-shared-secret
pre-shared-secret mysecret
remote-id my.office.domain
}
connection-type respond
ike-group office-srv-ike
ikev2-reauth inherit
local-address any
tunnel 0 {
allow-nat-networks disable
allow-public-networks disable
esp-group office-srv-esp
local {
prefix 10.50.0.0/24
}
remote {
prefix 192.168.10.0/24
}
}
}
}
}
}
Here’s a diagram to explain my issue:
My goal:
Simple. Make subnets reach each other
Thanks for your support