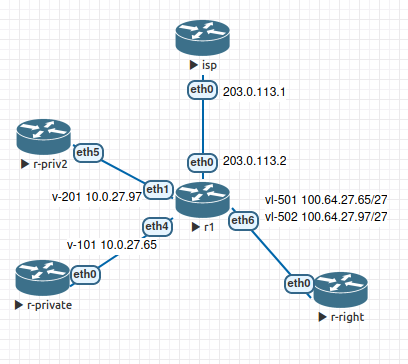
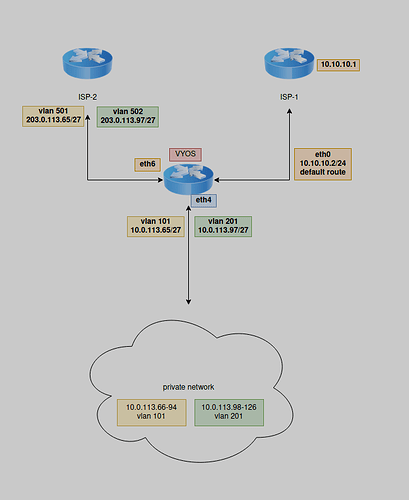
Try such configuration (in the example only pool 66–70)
set interfaces ethernet eth4 vif 101 address '10.0.27.65/27'
set interfaces ethernet eth4 vif 101 ip proxy-arp-pvlan
set interfaces ethernet eth6 vif 501 address '203.0.113.94/27'
set interfaces ethernet eth6 vif 501 description 'FOO'
set interfaces ethernet eth6 vif 501 ip proxy-arp-pvlan
set interfaces loopback lo
set nat destination rule 66 description 'DNAT-66'
set nat destination rule 66 destination address '203.0.113.66'
set nat destination rule 66 inbound-interface 'eth6.501'
set nat destination rule 66 translation address '10.0.27.66'
set nat destination rule 67 description 'DNAT-67'
set nat destination rule 67 destination address '203.0.113.67'
set nat destination rule 67 inbound-interface 'eth6.501'
set nat destination rule 67 translation address '10.0.27.67'
set nat destination rule 68 description 'DNAT-68'
set nat destination rule 68 destination address '203.0.113.68'
set nat destination rule 68 inbound-interface 'eth6.501'
set nat destination rule 68 translation address '10.0.27.68'
set nat destination rule 69 description 'DNAT-69'
set nat destination rule 69 destination address '203.0.113.69'
set nat destination rule 69 inbound-interface 'eth6.501'
set nat destination rule 69 translation address '10.0.27.69'
set nat destination rule 70 description 'DNAT-70'
set nat destination rule 70 destination address '203.0.113.70'
set nat destination rule 70 inbound-interface 'eth6.501'
set nat destination rule 70 translation address '10.0.27.70'
set nat source rule 66 description 'SNAT-66'
set nat source rule 66 outbound-interface 'eth6.501'
set nat source rule 66 source address '10.0.27.66'
set nat source rule 66 translation address '203.0.113.66'
set nat source rule 67 description 'SNAT-67'
set nat source rule 67 outbound-interface 'eth6.501'
set nat source rule 67 source address '10.0.27.67'
set nat source rule 67 translation address '203.0.113.67'
set nat source rule 68 description 'SNAT-68'
set nat source rule 68 outbound-interface 'eth6.501'
set nat source rule 68 source address '10.0.27.68'
set nat source rule 68 translation address '203.0.113.68'
set nat source rule 69 description 'SNAT-69'
set nat source rule 69 outbound-interface 'eth6.501'
set nat source rule 69 source address '10.0.27.69'
set nat source rule 69 translation address '203.0.113.69'
set nat source rule 70 description 'SNAT-70'
set nat source rule 70 outbound-interface 'eth6.501'
set nat source rule 70 source address '10.0.27.70'
set nat source rule 70 translation address '203.0.113.70'
Ping from ISP2
vyos@isp2:~$ ping 203.0.113.67 count 2
PING 203.0.113.67 (203.0.113.67) 56(84) bytes of data.
64 bytes from 203.0.113.67: icmp_seq=1 ttl=63 time=2.06 ms
64 bytes from 203.0.113.67: icmp_seq=2 ttl=63 time=1.81 ms
--- 203.0.113.67 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 3ms
rtt min/avg/max/mdev = 1.812/1.934/2.056/0.122 ms
vyos@isp2:~$
vyos@isp2:~$ ping 203.0.113.68 count 2
PING 203.0.113.68 (203.0.113.68) 56(84) bytes of data.
64 bytes from 203.0.113.68: icmp_seq=1 ttl=63 time=597 ms
64 bytes from 203.0.113.68: icmp_seq=2 ttl=63 time=1.37 ms
--- 203.0.113.68 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 2ms
rtt min/avg/max/mdev = 1.365/299.381/597.397/298.016 ms
vyos@isp2:~$
vyos@isp2:~$ ping 203.0.113.69 count 2
PING 203.0.113.69 (203.0.113.69) 56(84) bytes of data.
64 bytes from 203.0.113.69: icmp_seq=1 ttl=63 time=506 ms
64 bytes from 203.0.113.69: icmp_seq=2 ttl=63 time=1.33 ms
--- 203.0.113.69 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 2ms
rtt min/avg/max/mdev = 1.330/253.849/506.368/252.519 ms
vyos@isp2:~$
The dump from “private”
vyos@vyos:~$ sudo tcpdump -nti eth0.101
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0.101, link-type EN10MB (Ethernet), capture size 262144 bytes
IP 203.0.113.65 > 10.0.27.67: ICMP echo request, id 2584, seq 1, length 64
IP 10.0.27.67 > 203.0.113.65: ICMP echo reply, id 2584, seq 1, length 64
ARP, Request who-has 10.0.27.67 tell 10.0.27.65, length 28
ARP, Reply 10.0.27.67 is-at 50:00:00:01:00:00, length 28
IP 203.0.113.65 > 10.0.27.67: ICMP echo request, id 2607, seq 1, length 64
IP 10.0.27.67 > 203.0.113.65: ICMP echo reply, id 2607, seq 1, length 64
IP 203.0.113.65 > 10.0.27.67: ICMP echo request, id 2607, seq 2, length 64
IP 10.0.27.67 > 203.0.113.65: ICMP echo reply, id 2607, seq 2, length 64
ARP, Request who-has 10.0.27.68 tell 10.0.27.65, length 28
ARP, Reply 10.0.27.68 is-at 50:00:00:01:00:00, length 28
IP 203.0.113.65 > 10.0.27.68: ICMP echo request, id 2630, seq 1, length 64
IP 10.0.27.68 > 203.0.113.65: ICMP echo reply, id 2630, seq 1, length 64
IP 203.0.113.65 > 10.0.27.68: ICMP echo request, id 2630, seq 2, length 64
IP 10.0.27.68 > 203.0.113.65: ICMP echo reply, id 2630, seq 2, length 64