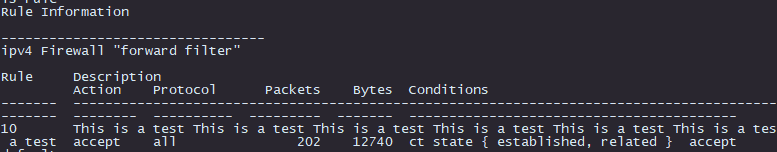
I think it would be useful to have the configured description as a column when looking at “show firewall” commands, particularly with the “show firewall statistics” command as it doesn’t indicate any details of the rule. Output would be like this:
show firewall:
Rule Description Action Protocol Packets Bytes Conditions
------- ---------------------------------------- -------- ---------- --------- ------- ------------------------------------------------------------------------------
5 Allow return traffic from inside network offload all 5369 337834 ct state { established, related } flow add @VYOS_FLOWTABLE_OT1
show firewall statistics:
Rule Description Packets Bytes Action Source Destination Inbound-Interface Outbound-interface
------- ---------------------------------------- --------- ------- -------- ------------- ------------- ------------------- --------------------
5 Allow return traffic from inside network 5421 341106 offload any any any any
I created a task to track this:
https://vyos.dev/T6188