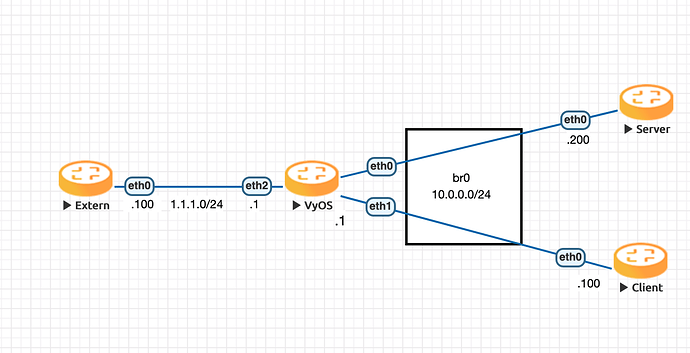
Example here:
MacBook = 10.0.100.150 (8c:85:90:24:a0:4d)
Router = 10.0.100.1 (40:62:31:13:eb:8f)
Internal server = 10.0.100.6 (32:19:63:dd:f2:5f)
WAN is connected via pppoe0
Bridge config:
address 10.0.100.1/24
member {
interface eth0.100 {
}
interface eth1.100 {
}
interface eth2.100 {
}
}
NAT config:
destination {
rule 1 {
destination {
port 8443
}
inbound-interface pppoe0
protocol tcp
translation {
address 10.0.100.6
}
}
rule 100 {
destination {
address <MY-WAN-IP-HERE>
port 8443
}
inbound-interface br100
protocol tcp
translation {
address 10.0.100.6
}
}
}
source {
rule 100 {
destination {
address 10.0.100.0/24
}
outbound-interface br100
protocol tcp
source {
address 10.0.100.0/24
}
translation {
address masquerade
}
}
rule 9000 {
description "Internet out"
outbound-interface pppoe0
protocol all
translation {
address masquerade
}
}
}
Without br100 in promiscuous mode
Connecting from MacBook (10.0.100.150) to server (10.0.100.6) port tcp/8443: succes.
Connecting from MacBook (10.0.100.150) to WAN IP port tcp/8443: nothing.
On my mac: tcpdump -nei en0
09:50:44.369899 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56225 > <MY-WAN-IP>.8443: Flags [S], seq 53325316, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210952979 ecr 0,sackOK,eol], length 0
09:50:45.373179 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56225 > <MY-WAN-IP>.8443: Flags [S], seq 53325316, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210953979 ecr 0,sackOK,eol], length 0
09:50:46.373287 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56225 > <MY-WAN-IP>.8443: Flags [S], seq 53325316, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210954979 ecr 0,sackOK,eol], length 0
09:50:47.374485 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56225 > <MY-WAN-IP>.8443: Flags [S], seq 53325316, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210955979 ecr 0,sackOK,eol], length 0
09:50:48.379480 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56225 > <MY-WAN-IP>.8443: Flags [S], seq 53325316, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210956979 ecr 0,sackOK,eol], length 0
With br100 in promiscuous mode (with tcpdump)
Starting up tcpdump -nei br100 on router.
Connecting from MacBook (10.0.100.150) to WAN IP port tcp/8443: succes.
On my mac: tcpdump -nei en0 port 8443
09:49:10.565962 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56216 > <MY-WAN-IP>.8443: Flags [S], seq 3025485842, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210859482 ecr 0,sackOK,eol], length 0
09:49:10.568875 40:62:31:13:eb:8f > 8c:85:90:24:a0:4d, ethertype IPv4 (0x0800), length 74: <MY-WAN-IP>.8443 > 10.0.100.150.56216: Flags [S.], seq 1432450948, ack 3025485843, win 65160, options [mss 1460,sackOK,TS val 4165071171 ecr 1210859482,nop,wscale 7], length 0
09:49:10.568980 8c:85:90:24:a0:4d > 40:62:31:13:eb:8f, ethertype IPv4 (0x0800), length 66: 10.0.100.150.56216 > <MY-WAN-IP>.8443: Flags [.], ack 1, win 2058, options [nop,nop,TS val 1210859485 ecr 4165071171], length 0
On router: tcpdump -nei br100 port 8443
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on br100, link-type EN10MB (Ethernet), capture size 262144 bytes
09:39:23.361789 8c:85:90:24:a0:4d > 32:19:63:dd:f2:5f, ethertype IPv4 (0x0800), length 78: 10.0.100.150.56188 > 10.0.100.6.8443: Flags [S], seq 657712525, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210266758 ecr 0,sackOK,eol], length 0
09:39:23.361831 40:62:31:13:eb:8f > 32:19:63:dd:f2:5f, ethertype IPv4 (0x0800), length 78: 10.0.100.1.56188 > 10.0.100.6.8443: Flags [S], seq 657712525, win 65535, options [mss 1460,nop,wscale 6,nop,nop,TS val 1210266758 ecr 0,sackOK,eol], length 0
09:39:23.362110 32:19:63:dd:f2:5f > 8c:85:90:24:a0:4d, ethertype IPv4 (0x0800), length 74: 10.0.100.6.8443 > 10.0.100.150.56188: Flags [S.], seq 1987005752, ack 657712526, win 65160, options [mss 1460,sackOK,TS val 4164476466 ecr 1210266758,nop,wscale 7], length 0
09:39:23.362133 40:62:31:13:eb:8f > 8c:85:90:24:a0:4d, ethertype IPv4 (0x0800), length 74: <MY-WAN-IP>.8443 > 10.0.100.150.56188: Flags [S.], seq 1987005752, ack 657712526, win 65160, options [mss 1460,sackOK,TS val 4164476466 ecr 1210266758,nop,wscale 7], length 0
09:39:23.364711 8c:85:90:24:a0:4d > 32:19:63:dd:f2:5f, ethertype IPv4 (0x0800), length 66: 10.0.100.150.56188 > 10.0.100.6.8443: Flags [.], ack 1, win 2058, options [nop,nop,TS val 1210266761 ecr 4164476466], length 0
09:39:23.364750 40:62:31:13:eb:8f > 32:19:63:dd:f2:5f, ethertype IPv4 (0x0800), length 66: 10.0.100.1.56188 > 10.0.100.6.8443: Flags [.], ack 1987005753, win 2058, options [nop,nop,TS val 1210266761 ecr 4164476466], length 0
As mentioned: using this exact same NAT config, but removing the bridge and putting the IP etc. on eth0.100 only this setup works just fine.