It seems like country code filtering is not working for me. I have setup a rule to block traffic to specific country codes. Here are my rules:
# show firewall ipv4 forward
filter {
default-action drop
default-log
description "FORWARD is traffic bound from one interface to another"
rule 10 {
action jump
jump-target CONN_FILTER
}
rule 11 {
action jump
description "Block TO China, Venezuela, Russia"
destination {
geoip {
country-code cn
country-code ru
country-code ve
}
}
jump-target BLOCKED_COUNTRIES
}
rule 12 {
action jump
description "Block from China, Venezuela, Russia"
jump-target BLOCKED_COUNTRIES
source {
geoip {
country-code cn
country-code ru
country-code ve
}
}
}
Here you can see I send all TO and FROM these countries to a rule called BLOCKED_COUNTRIES.
# show firewall ipv4 name BLOCKED_COUNTRIES
default-action drop
default-log
description "Block traffic from the assigned country codes"
However, when monitoring DNS traffic, I see traffic specifically going to China unimpeded. I can in fact ping these Chinese IP’s successfully from a client on this network.
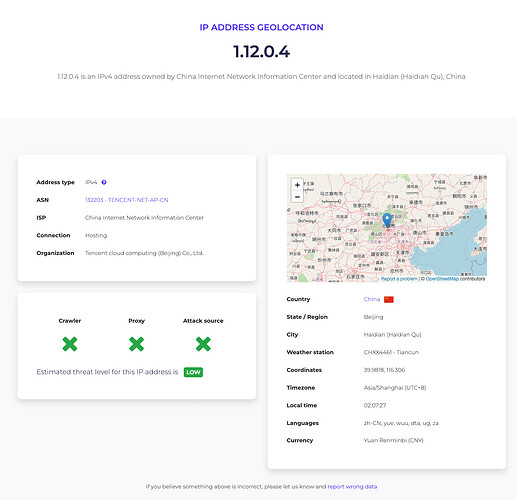
The IP’s:
1.12.0.4
1.12.0.1
1.12.0.29
1.12.0.71
Any ideas why it’s not blocked?