Hi Team,
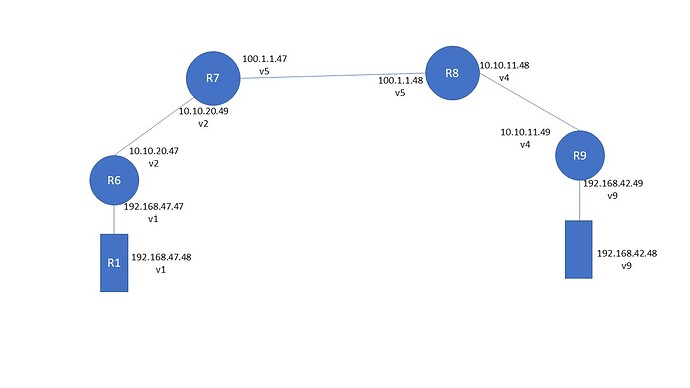
I am facing the below issue with 1.2.6 and keen to know if I am missing anything? I am setting up simple site-to-site ipsec vpn between R7 and R8.
My prefixes are 192.168.47.0/24 from R7 end and 192.168.42.0/24 from R8 end
I have default gateway added on R6 and R9 pointing to R7 and R8 respectively.
vyos@**R6**:~$ show ip route static
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
S>* 0.0.0.0/0 [1/0] via 10.10.20.49, eth1, 00:47:29
Now my tunnels at R7 and R8 are up
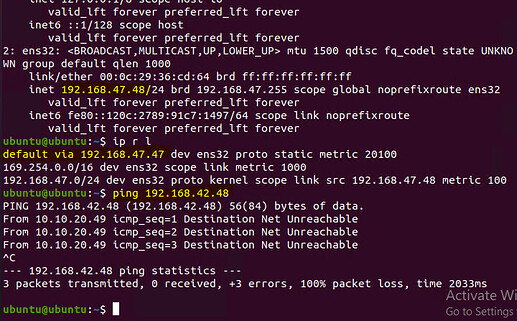
However when I try to ping from 192.168.47.48 to 192.168.42.48 my R7 says destination net un rechable.
Am I missing anything here? if local-prefixes are not directly attached to ipsec routers do we need to add any routes?
Here is my R7 config
set vpn ipsec esp-group ESPG compression 'disable'
set vpn ipsec esp-group ESPG lifetime '3600'
set vpn ipsec esp-group ESPG mode 'tunnel'
set vpn ipsec esp-group ESPG pfs 'enable'
set vpn ipsec esp-group ESPG proposal 1 encryption 'aes256'
set vpn ipsec esp-group ESPG proposal 1 hash 'sha256'
set vpn ipsec ike-group IKEG ikev2-reauth 'no'
set vpn ipsec ike-group IKEG key-exchange 'ikev1'
set vpn ipsec ike-group IKEG lifetime '28800'
set vpn ipsec ike-group IKEG proposal 1 dh-group '2'
set vpn ipsec ike-group IKEG proposal 1 encryption 'aes256'
set vpn ipsec ike-group IKEG proposal 1 hash 'sha256'
set vpn ipsec ipsec-interfaces interface 'eth1'
set vpn ipsec site-to-site peer 100.1.1.48 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 100.1.1.48 authentication pre-shared-secret 'admin@123'
set vpn ipsec site-to-site peer 100.1.1.48 ike-group 'IKEG'
set vpn ipsec site-to-site peer 100.1.1.48 local-address '100.1.1.47'
set vpn ipsec site-to-site peer 100.1.1.48 tunnel 1 allow-nat-networks 'disable'
set vpn ipsec site-to-site peer 100.1.1.48 tunnel 1 allow-public-networks 'disable'
set vpn ipsec site-to-site peer 100.1.1.48 tunnel 1 esp-group 'ESPG'
set vpn ipsec site-to-site peer 100.1.1.48 tunnel 1 local prefix '192.168.47.0/24'
set vpn ipsec site-to-site peer 100.1.1.48 tunnel 1 remote prefix '192.168.42.0/24'
set interfaces ethernet eth0 address '10.10.20.49/24'
set interfaces ethernet eth0 hw-id '00:0c:29:05:59:42'
set interfaces ethernet eth1 address '100.1.1.47/24'
set interfaces ethernet eth1 hw-id '00:0c:29:05:59:4c'
set interfaces loopback lo
set protocols static interface-route 192.168.42.0/24 next-hop-interface tun1
set protocols static route 192.168.47.0/24 next-hop 10.10.20.47
And my R8 config
set vpn ipsec esp-group ESPG compression 'disable'
set vpn ipsec esp-group ESPG lifetime '3600'
set vpn ipsec esp-group ESPG mode 'tunnel'
set vpn ipsec esp-group ESPG pfs 'enable'
set vpn ipsec esp-group ESPG proposal 1 encryption 'aes256'
set vpn ipsec esp-group ESPG proposal 1 hash 'sha256'
set vpn ipsec ike-group IKEG ikev2-reauth 'no'
set vpn ipsec ike-group IKEG key-exchange 'ikev1'
set vpn ipsec ike-group IKEG lifetime '28800'
set vpn ipsec ike-group IKEG proposal 1 dh-group '2'
set vpn ipsec ike-group IKEG proposal 1 encryption 'aes256'
set vpn ipsec ike-group IKEG proposal 1 hash 'sha256'
set vpn ipsec ipsec-interfaces interface 'eth0'
set vpn ipsec site-to-site peer 100.1.1.47 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 100.1.1.47 authentication pre-shared-secret 'admin@123'
set vpn ipsec site-to-site peer 100.1.1.47 ike-group 'IKEG'
set vpn ipsec site-to-site peer 100.1.1.47 local-address '100.1.1.48'
set vpn ipsec site-to-site peer 100.1.1.47 tunnel 1 allow-nat-networks 'disable'
set vpn ipsec site-to-site peer 100.1.1.47 tunnel 1 allow-public-networks 'disable'
set vpn ipsec site-to-site peer 100.1.1.47 tunnel 1 esp-group 'ESPG'
set vpn ipsec site-to-site peer 100.1.1.47 tunnel 1 local prefix '192.168.42.0/24'
set vpn ipsec site-to-site peer 100.1.1.47 tunnel 1 remote prefix '192.168.47.0/24'
set interfaces ethernet eth0 address '100.1.1.48/24'
set interfaces ethernet eth0 hw-id '00:0c:29:b0:b6:27'
set interfaces ethernet eth1 address '10.10.11.48/24'
set interfaces ethernet eth1 hw-id '00:0c:29:b0:b6:31'
set interfaces loopback lo
set protocols static interface-route 192.168.47.0/24 next-hop-interface tun1
set protocols static route 192.168.42.0/24 next-hop 10.10.11.49
Do I need to add any routes on R7 and R8? however my tunnels are up
vyos@**R7**# run show vpn ipsec sa
Connection State Up Bytes In/Out Remote address Remote ID Proposal
------------------------ ------- ---------- -------------- ---------------- ----------- ---------------------------------------------------------
peer-100.1.1.48-tunnel-1 up 15 minutes 0B/0B 100.1.1.48 N/A AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
on R8
vyos@**R8**# run show vpn ipsec sa
Connection State Up Bytes In/Out Remote address Remote ID Proposal
------------------------ ------- ---------- -------------- ---------------- ----------- ---------------------------------------------------------
peer-100.1.1.47-tunnel-1 up 15 minutes 0B/0B 100.1.1.47 N/A AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024
[edit]