Hello everyone,
I need some assistance with a setup that I am trying as a proof of concept. In GNS3, I have a setup where there is a Cisco router, a VyOS router, a switch, and 3 network endpoints: a PC, a phone, and a network appliance.
Networks in use are the following:
Default VLAN1 for the PCs - 192.168.8.0/22
VLAN 100 for the network appliances - 10.100.8.0/29
VLAN 700 for the phones - 172.16.8.0/23
The Cisco router and VyOS router are setup in a VRRP configuration.
There is an acl-list defined on the Cisco router to prevent the network appliances from communicating with other devices on the network. The relevant parts of the config are as follows:
interface FastEthernet0/0.100
description Restricted_Devices_Network
encapsulation dot1Q 100
ip address 10.100.8.5 255.255.255.248
ip access-group Filter_Restricted_Devices in
vrrp 60 description Restricted_Devices_Network
vrrp 60 ip 10.100.8.1
vrrp 60 priority 110
interface FastEthernet0/0.700
encapsulation dot1Q 700
ip address 172.16.8.2 255.255.255.0
vrrp 20 description VoIP
vrrp 20 ip 172.16.8.1
vrrp 20 priority 110
!
interface FastEthernet0/1
ip address 192.168.8.2 255.255.248.0
duplex auto
speed auto
vrrp 30 description Branch LAN
vrrp 30 ip 192.168.10.16
vrrp 30 priority 110
ip access-list extended Filter_Restricted_Devices
deny ip 10.100.8.0 0.0.0.7 192.168.0.0 0.0.255.255
deny ip 10.100.8.0 0.0.0.7 172.16.0.0 0.0.255.255
permit ip any any
On the VyOS router, the relevant parts of the config are as follows:
set firewall all-ping ‘enable’
set firewall broadcast-ping ‘disable’
set firewall config-trap ‘disable’
set firewall group network-group Internal_Networks network ‘192.168.0.0/16’
set firewall group network-group Internal_Networks network ‘172.16.0.0/16’
set firewall ipv6-receive-redirects ‘disable’
set firewall ipv6-src-route ‘disable’
set firewall ip-src-route ‘disable’
set firewall log-martians ‘enable’
set firewall name Prevented_Networks default-action ‘accept’
set firewall name Prevented_Networks enable-default-log
set firewall name Prevented_Networks rule 5 action ‘reject’
set firewall name Prevented_Networks rule 5 destination group network-group ‘Internal_Networks’
set firewall name Prevented_Networks rule 5 log ‘enable’
set firewall receive-redirects ‘disable’
set firewall send-redirects ‘enable’
set firewall source-validation ‘disable’
set firewall syn-cookies ‘enable’
set firewall twa-hazards-protection ‘disable’
set high-availability vrrp group BranchLAN interface ‘eth2’
set high-availability vrrp group BranchLAN priority ‘50’
set high-availability vrrp group BranchLAN rfc3768-compatibility
set high-availability vrrp group BranchLAN virtual-address ‘192.168.10.16/22’
set high-availability vrrp group BranchLAN vrid ‘30’
set high-availability vrrp group Network_Appliances interface ‘eth3’
set high-availability vrrp group Network_Appliances priority ‘50’
set high-availability vrrp group Network_Appliances rfc3768-compatibility
set high-availability vrrp group Network_Appliances virtual-address ‘10.100.8.1/29’
set high-availability vrrp group Network_Appliances vrid ‘60’
set high-availability vrrp group VoIP interface ‘eth1’
set high-availability vrrp group VoIP priority ‘50’
set high-availability vrrp group VoIP rfc3768-compatibility
set high-availability vrrp group VoIP virtual-address ‘172.16.8.1/23’
set high-availability vrrp group VoIP vrid ‘20’
set high-availability vrrp sync-group Main member ‘Firewall’
set high-availability vrrp sync-group Main member ‘BranchLAN’
set high-availability vrrp sync-group Main member ‘VoIP’
set high-availability vrrp sync-group Main member ‘Network_Appliances’
set interfaces ethernet eth1 address ‘172.16.8.3/24’
set interfaces ethernet eth1 hw-id ‘0c:83:ad:78:5a:01’
set interfaces ethernet eth2 address ‘192.168.8.3/22’
set interfaces ethernet eth2 hw-id ‘0c:83:ad:78:5a:02’
set interfaces ethernet eth3 address ‘10.100.8.6/29’
set interfaces ethernet eth3 firewall local name ‘Prevented_Networks’
set interfaces ethernet eth3 hw-id ‘0c:83:ad:78:5a:03’
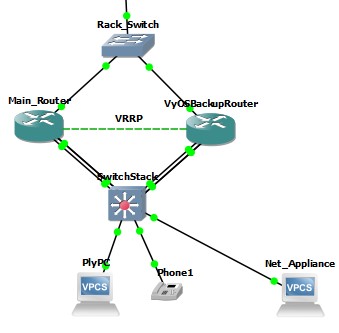
With the Cisco router on and the active VRRP router, pinging from the net_appliance to an IP address in the default VLAN and the phone VLAN, the pings are administratively prohibited by the access-list.
VPCS> sh ip
NAME : VPCS[1]
IP/MASK : 10.100.8.2/29
GATEWAY : 10.100.8.1
DNS :
MAC : 00:50:79:66:68:0b
LPORT : 20250
RHOST:PORT : 127.0.0.1:20251
MTU: : 1500
VPCS> ping 192.168.10.16
*10.100.8.5 icmp_seq=1 ttl=255 time=5.937 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=2 ttl=255 time=7.071 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=3 ttl=255 time=6.357 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=4 ttl=255 time=6.901 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=5 ttl=255 time=7.913 ms (ICMP type:3, code:13, Communication administratively prohibited)
VPCS> ping 172.16.8.1
*10.100.8.5 icmp_seq=1 ttl=255 time=6.050 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=2 ttl=255 time=7.989 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=3 ttl=255 time=7.953 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=4 ttl=255 time=9.409 ms (ICMP type:3, code:13, Communication administratively prohibited)
*10.100.8.5 icmp_seq=5 ttl=255 time=8.936 ms (ICMP type:3, code:13, Communication administratively prohibited)
VPCS>
Now, when I turn off the Cisco router, the VyOS router becomes the active one, and a ping is done again as before, and this time the pings are allowed through.
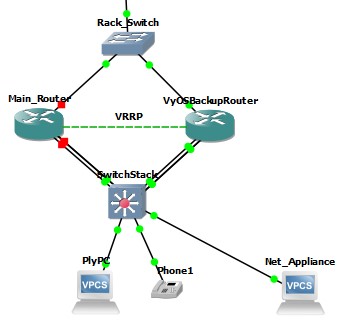
VPCS> sh ip
NAME : VPCS[1]
IP/MASK : 10.100.8.2/29
GATEWAY : 10.100.8.1
DNS :
MAC : 00:50:79:66:68:14
LPORT : 20266
RHOST:PORT : 127.0.0.1:20267
MTU: : 1500
VPCS> ping 192.168.10.16
84 bytes from 192.168.10.16 icmp_seq=1 ttl=64 time=1.532 ms
84 bytes from 192.168.10.16 icmp_seq=2 ttl=64 time=1.271 ms
84 bytes from 192.168.10.16 icmp_seq=3 ttl=64 time=1.454 ms
84 bytes from 192.168.10.16 icmp_seq=4 ttl=64 time=1.315 ms
84 bytes from 192.168.10.16 icmp_seq=5 ttl=64 time=1.258 ms
VPCS> ping 172.16.8.1
84 bytes from 172.16.8.1 icmp_seq=1 ttl=64 time=2.693 ms
84 bytes from 172.16.8.1 icmp_seq=2 ttl=64 time=1.473 ms
84 bytes from 172.16.8.1 icmp_seq=3 ttl=64 time=1.393 ms
84 bytes from 172.16.8.1 icmp_seq=4 ttl=64 time=1.464 ms
84 bytes from 172.16.8.1 icmp_seq=5 ttl=64 time=1.325 ms
VPCS>
vyos@vyos:~$ sh firewall name Prevented_Networks
Rulesets Information
IPv4 Firewall “Prevented_Networks”:
Active on (eth3,LOCAL)
rule action proto packets bytes
5 reject all 0 0
condition - saddr 0.0.0.0/0 daddr 0.0.0.0/0 /* Prevented_Networks-5 */ reject-
with icmp-port-unreachableLOG enabled
10000 accept all 0 0
condition - saddr 0.0.0.0/0 daddr 0.0.0.0/0 LOG enabled
vyos@vyos:~$
Can someone help me out in understanding why the firewall rules in VyOS are not getting triggered/not used?
Thank you!