Hi everyone!
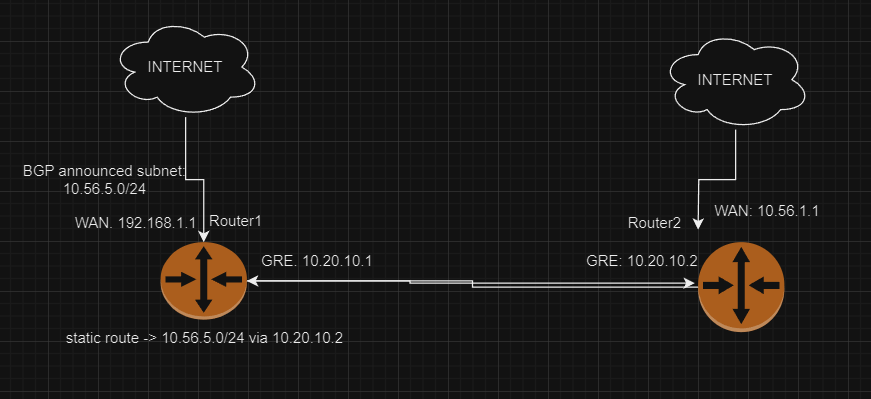
I’m running VyOS on two routers, router1 and router2. See diagram.
My router1 is announcing a public subnet space, in this example called 10.56.5.0/24 to my upstream. This setup works perfectly fine.
I then do a static route via the GRE to router2, so 10.56.5.0/24 via 10.20.10.2
On router2, I assign 10.56.5.1/24 to eth1. Both router 1 and 2 can ping 10.56.5.1 perfect!
From outside, I cannot. I think it is because my upstream at router2 does not allow traffic from a source IP that is not whitelisted in their system (would assume to prevent spoofing).
Ok! So doing this on router2:
set protocols static route x.x.x.x(HOMEIP)/32 next-hop 10.20.10.1 → Gives me full access to the subnet at home, public over the internet. Great!
However, I want to make a 0.0.0.0/0 via 10.20.10.1 once traffic is comming from source subnet 10.56.5.0/24. I’ve been fiddling around with policy based routing with VyOS 1.3.3, but I cant seem to get it working like I want. These are the steps I’ve been working with:
Create a firewall group for the source network
set firewall group network-group SOURCE-NETWORK network 10.56.5.0/24
Create a policy route to match traffic from the source network
set policy route POLICY-ROUTE rule 10 source group network-group SOURCE-NETWORK
Set the next-hop for the matched traffic to 10.20.10.1
set policy route POLICY-ROUTE rule 10 set table 100
Create a static route in table 100 to send the traffic via 10.20.10.1
set protocols static table 100 route 0.0.0.0/0 next-hop 10.20.10.1
If I ping from my home IP /PC again, I cannot get through. It only works when doing the static route.
If I do a whole 0.0.0.0/0 via 10.20.10.1, the router will loose its connection to the internet. Ok! I can then simply do a static route that says reach router1 via router2 upstream gateway, but even that wont let me ping in.
There’s no firewall rules or anything alike. I’m simply trying to pull over a /24 to a different router.
Can anyone point me in the right direction? Running VyOS 1.3.3 LTS
When doing a tcpdump, I see the ping request comming in via TUN70 (My GRE), and the router answers to it with a reply and sents that reply out via default gateway. So I assume when I do my static route with my own home IP and it works for me, is because it overrules this. So what I am actually asking for is how I can make all traffic incomming for subnet 10.56.5.0/24 go OUT again via 10.20.10.1
Would I have to on my router1 to do anything else that allows traffic from 10.20.10.2 via 0.0.0.0?