I can’t get below config to work…
Anyone with ideas on what I’m made wrong or missed?
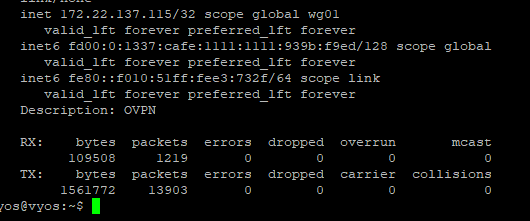
When running “show interfaces wireguard wg01” it seems as if I’m connected and indicating that the tunnel is open and ready for usage.
{
"interfaces": {
"ethernet": {
"eth0": {
"address": [
"192.168.10.1/24"
],
"description": "INSIDE",
"hw-id": "80:ee:73:77:de:f0"
},
"eth1": {
"address": [
"dhcp"
],
"description": "OUTSIDE",
"hw-id": "80:ee:73:77:de:f1"
}
},
"loopback": {
"lo": {}
},
"wireguard": {
"wg01": {
"address": [
"172.22.137.115/32",
"fd00:0000:1337:cafe:1111:1111:939b:f9ed/128"
],
"description": "OVPN",
"peer": {
"OVPN": {
"address": "193.187.91.195",
"allowed-ips": [
"0.0.0.0/0",
"::/0"
],
"persistent-keepalive": "15",
"port": "9929",
"public-key": "MY_PUBLIC_KEY"
}
},
"port": "9929",
"private-key": "MY_PRIVATE_KEY"
}
},
"wireless": {
"wlan0": {
"hw-id": "64:5a:04:aa:f0:fa",
"physical-device": "phy0"
}
}
},
"nat": {
"source": {
"rule": {
"50": {
"outbound-interface": "wg01",
"source": {
"address": "192.168.10.0/24"
},
"translation": {
"address": "masquerade"
}
}
}
}
},
"protocols": {
"static": {
"route": {
"0.0.0.0/0": {},
"192.168.0.0/16": {
"interface": {
"wg01": {}
}
}
}
}
},
"service": {
"dhcp-server": {
"shared-network-name": {
"LAN": {
"subnet": {
"192.168.10.0/24": {
"default-router": "192.168.10.1",
"domain-name": "MY_DOMAIN_NAME",
"lease": "86400",
"name-server": [
"192.168.10.1"
],
"range": {
"0": {
"start": "192.168.10.30",
"stop": "192.168.10.254"
}
}
}
}
}
}
},
"dns": {
"forwarding": {
"allow-from": [
"192.168.10.0/24"
],
"cache-size": "0",
"listen-address": [
"192.168.10.1"
]
}
},
"ssh": {
"port": [
"22"
]
}
},
"system": {
"config-management": {
"commit-revisions": "100"
},
"conntrack": {
"modules": {
"ftp": {},
"h323": {},
"nfs": {},
"pptp": {},
"sip": {},
"sqlnet": {},
"tftp": {}
}
},
"console": {
"device": {
"ttyS0": {
"speed": "115200"
}
}
},
"host-name": "vyos",
"login": {
"user": {
"MY_USER_NAME": {
"authentication": {
"encrypted-password"MY_USER_PASSWORD",
"plaintext-password": ""
}
}
}
},
"syslog": {
"global": {
"facility": {
"all": {
"level": "info"
},
"protocols": {
"level": "debug"
}
}
}
},
"time-zone": "UTC"
}
}
![]()