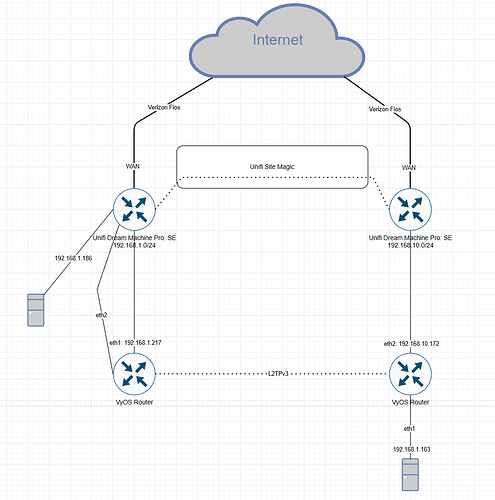
I am looking for assistance creating an L2TPv3 connection between two locations. Each location has a Unifi UDMP: SE as the primary router that are connected together using Unifi’s L3 SD-WAN “like” solution called Site Magic. Under the hood, this uses wireguard I believe to create individual connections to each site in the site magic group. This will act as my encrypted L3 tunnel. Behind each UDMP I have a VyOS instance running bare metal on intel Mini PC’s. The intent is to create a pseudo-wire connection using L2TPv3 so that a device connected to the VyOS instance at Site B can receive an IP address via Site A’s UDMP DHCP and for all intents and purposes “think” it is physically on the same LAN as Site A. The reason for this is the device at Site B is an IoT device that needs to receive L2 traffic (Broadcast and Multicast) from another host device at Site A .
Each VyOS isntance is “vyos-1.5-rolling-202405101513-amd64”.
I had this solution working about two years ago and I am returning to the project and having issues now. Below is my configurations for each site. Any assistance would be greatly appreciated as networking is not my expertise. Additionally, I am aware of third party software solutions such as ZeroTier that have the ability to create L2 tunnels but I am not interested in running unsupported software on the UDMP’s.
I have no problem with regular L3 traffic between the two sites, and access regular services across the site magic connection. I have a feeling it’s something simple like I need to do a port forwarding rule on the UDMP or something but I don’t know enough to figure it out.
Network Diagram:
Site A:
interfaces {
bridge br0 {
address dhcp
description "L2 Bridge"
member {
interface eth2 {
}
interface l2tpeth0 {
}
}
}
ethernet eth1 {
address dhcp
hw-id 60:be:b4:07:81:cb
}
ethernet eth2 {
hw-id 60:be:b4:07:81:cc
}
ethernet eth3 {
hw-id 60:be:b4:07:81:cd
offload {
gro
gso
sg
tso
}
}
ethernet eth4 {
hw-id 60:be:b4:07:81:ce
offload {
gro
gso
sg
tso
}
}
l2tpv3 l2tpeth0 {
description "L2 VPN Tunnel"
destination-port 5000
encapsulation ip
mtu 1500
peer-session-id 10
peer-tunnel-id 10
remote 192.168.10.172
session-id 10
source-address 192.168.1.217
source-port 5000
tunnel-id 10
}
loopback lo {
}
wireless wlan0 {
hw-id f4:7b:09:c9:7a:8e
physical-device phy0
}
}
service {
ntp {
allow-client {
address 127.0.0.0/8
address 169.254.0.0/16
address 10.0.0.0/8
address 172.16.0.0/12
address 192.168.0.0/16
address ::1/128
address fe80::/10
address fc00::/7
}
server time1.vyos.net {
}
server time2.vyos.net {
}
server time3.vyos.net {
}
}
ssh {
}
}
system {
config-management {
commit-revisions 100
}
console {
device ttyS0 {
speed 115200
}
}
host-name vyos
login {
user vyos {
authentication {
encrypted-password ****************
plaintext-password ****************
}
}
}
syslog {
global {
facility all {
level info
}
facility local7 {
level debug
}
}
}
}
Site A “show interfaces”:
vyos@vyos:~$ show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address MAC VRF MTU S/L Description
----------- ---------------- ----------------- ------- ----- ----- -------------
br0 192.168.1.211/24 d2:cb:1a:41:4b:b0 default 1500 u/uL2 Bridge
eth1 192.168.1.217/24 60:be:b4:07:81:cb default 1500 u/u
eth2 - 60:be:b4:07:81:cc default 1500 u/u
eth3 - 60:be:b4:07:81:cd default 1500 u/D
eth4 - 60:be:b4:07:81:ce default 1500 u/D
l2tpeth0 - a2:49:32:11:ea:01 default 1500 u/uL2 VPN Tunnel
lo 127.0.0.1/800:00:00:00:00:00 default 65536 u/u
::1/128
wlan0 - f6:7b:09:c9:7a:80 default 1500 u/D
Site B:
interfaces {
bridge br0 {
address dhcp
description "L2 Bridge"
member {
interface eth1 {
}
interface l2tpeth0 {
}
}
}
ethernet eth1 {
description "Onboard Ethernet - Bridge Interface"
hw-id 54:b2:03:fd:24:db
}
ethernet eth2 {
address dhcp
description "Thunderbolot Ethernet - WAN Interface"
hw-id d8:ec:5e:74:3c:fe
}
l2tpv3 l2tpeth0 {
description "L2 VPN Tunnel"
destination-port 5000
encapsulation ip
mtu 1500
peer-session-id 10
peer-tunnel-id 10
remote 192.168.1.217
session-id 10
source-address 192.168.10.172
source-port 5000
tunnel-id 10
}
loopback lo {
}
wireless wlan0 {
hw-id 64:79:f0:3b:33:c3
physical-device phy0
}
}
service {
ntp {
allow-client {
address 127.0.0.0/8
address 169.254.0.0/16
address 10.0.0.0/8
address 172.16.0.0/12
address 192.168.0.0/16
address ::1/128
address fe80::/10
address fc00::/7
}
server time1.vyos.net {
}
server time2.vyos.net {
}
server time3.vyos.net {
}
}
ssh {
}
}
system {
config-management {
commit-revisions 100
}
console {
device ttyS0 {
speed 115200
}
}
host-name vyos
login {
user vyos {
authentication {
encrypted-password ****************
plaintext-password ****************
}
}
}
syslog {
global {
facility all {
level info
}
facility local7 {
level debug
}
}
}
}
Site B “show interfaces”:
vyos@vyos:~$ show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address MAC VRF MTU S/L Description
----------- ----------------- ----------------- ------- ----- ----- -------------------------------------
br0 192.168.1.110/24 ae:a4:6f:23:5d:c5 default 1500 u/uL2 Bridge
eth1 - 54:b2:03:fd:24:db default 1500 u/DOnboard Ethernet - Bridge Interface
eth2 192.168.10.172/24 d8:ec:5e:74:3c:fe default 1500 u/uThunderbolot Ethernet - WAN Interface
l2tpeth0 - ba:5e:2c:93:42:cb default 1500 u/uL2 VPN Tunnel
lo 127.0.0.1/800:00:00:00:00:00 default 65536 u/u
::1/128
wlan0 - 66:79:f0:3b:33:c0 default 1500 u/D
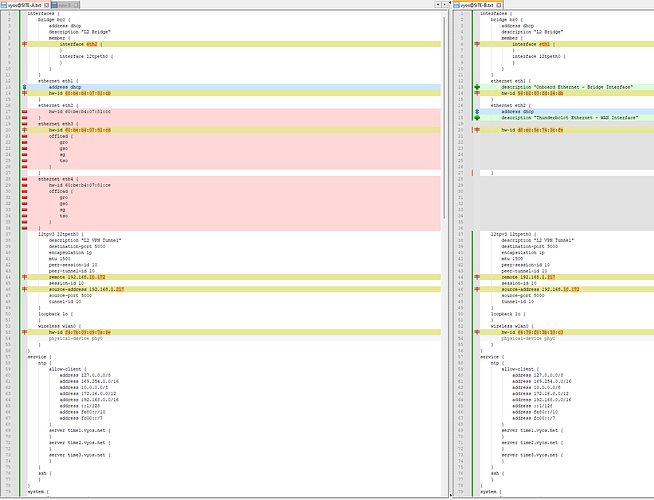
Config Compare: