So, let me see if I got this,
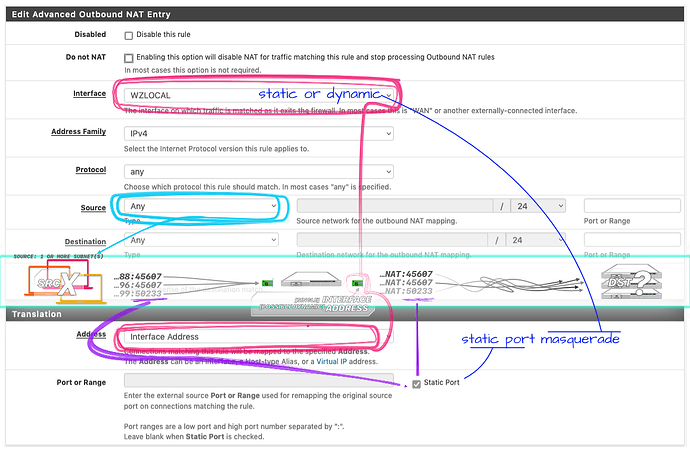
And thanks for answering BTW. Those three lines are actually the same amount of information required in the setup above (pfSense):
- Outbound interface
- Source equivalent to any
- “
masquerade” or another placeholder/macro for a dynamic address
- In pfSense is Interface Address or VIP in the Address drop down menu
And I’m just reading in the screenshot that ports should not be specified with static port translation. That’s odd, since since the filed is cleared and grayed out by the marking the checkbox next. I digress, though not to much since it’s actually related to what follows.
“it’s possible to assign a static range port” — so many questions this raises, I’ve rewritten this four-five times already, I hope it’s clear enough;
When you throw in range (of) port(s), source, assign and define/ing, in that single sentence, does it mean as a filter/match to NAT the traffic or for the public impersonation, if you will, of the source once it’s natted? i.e+e.g;
1st case the former / as filter
Traffic would be natted only if it comes from high ports YX to YZ. This is also an option above, it’s blank though an asterisk is accepted as well meaning the rule will match if the traffic comes sourced from the specified ports in the box. Note that this rule above as it is NATs beyond just port-based protocols, GRE, ESP, ICMP, etc covered too, the more fields left blank the wider the scope of the rule to match traffic.
2nd case the latter / impersonation
Regardless of what’s the original port the client host used to connect, publicly, connections will always originate from ports 30002 to 30004.
Also, if the port range is omitted, does it mean it it won’t be randomized (i.e. stays static) or the opposite? And if I do set the port range and it’s used as in the 2nd case, wouldn’t that just be symmetric NAT but with extra steps?
If those three lines are all that’s needed though, you’re going to make my day week, Full-cone is the last thing I need to sort out to adopt VyOS. Yesterday, I think, I found out that VyOS can reverse-proxy as well and I’m more determined that ever. Thanks again!