Hello
My partner used dh-group 1 on site-to-site vti IPsec tunnel , but in Ike vyos I don’t have any dh-group 1
Is supported this group ?
How can enable this group ?
Thanks a lot
Hi @Bahram , did you try?
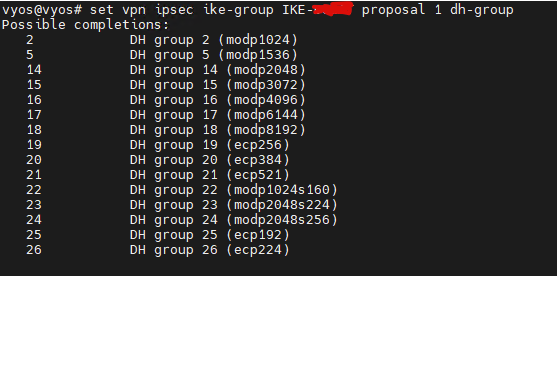
vyos@VyOS-RTR# set vpn ipsec ike-group IKE proposal 1 dh-group
Possible completions:
1 Diffie-Hellman group 1 (modp768)
...
vyos@VyOS-RTR# set vpn ipsec esp-group ESP pfs f
Possible completions:
enable Enable PFS. Use ike-group's dh-group (default)
dh-group1 Enable PFS. Use Diffie-Hellman group 1 (modp768)
You need just configure proposals properly for phase 1 and 2
i dont have any version 1
and my version
vyos@vyos# run show version
Version: VyOS 1.1.8
Description: VyOS 1.1.8 (helium)
Copyright: 2017 VyOS maintainers and contributors
Built by: maintainers@vyos.net
Built on: Sat Nov 11 13:44:36 UTC 2017
Build ID: 1711111344-b483efc
System type: x86 64-bit
Boot via: image
Hypervisor: VMware
HW model: VMware Virtual Platform
HW S/N: VMware-56 4d e2 ee 12 b0 0b f2-ec c7 11 3f 78 9e 01 2c
HW UUID: 564DE2EE-12B0-0BF2-ECC7-113F789E012C
Uptime: 12:35:17 up 1:26, 2 users, load average: 0.01, 0.02, 0.05
and ike1
thanks a lot
VyOS 1.1.x EOL, I can only propose to upgrade VyOS version on your router.
If you have a subscription, just download the new version from the support portal. If you don’t have it, you can build VyOS for yourself or use rolling images. For a production environment, you need to be very careful if you want to use rolling images.
thanks a lot my problem for dh-group solved but my new problem
![]()
other side is cisco and phase2 config is esp-3des
crypto ipsec transform-set ts esp-3des
mode tunnel
no hash algorithm is select in cisco , how can i set hash algorithm to null
my phase 1 established but phase 2 not
thanls a lot
Seems like VyOS can’t do null for hash
set vpn ipsec esp-group MyESP proposal 1 hash
Possible completions:
md5 MD5 hash
sha1 SHA1 hash (default)
sha256 SHA2-256 hash
sha384 SHA2-384 hash
sha512 SHA2-512 hash
Better use decent hash and enc protocol. 5 years ago, major vulnerability in 3DES was disclosed, making 3DES deprecated
thanks a lot
the other side must be changed