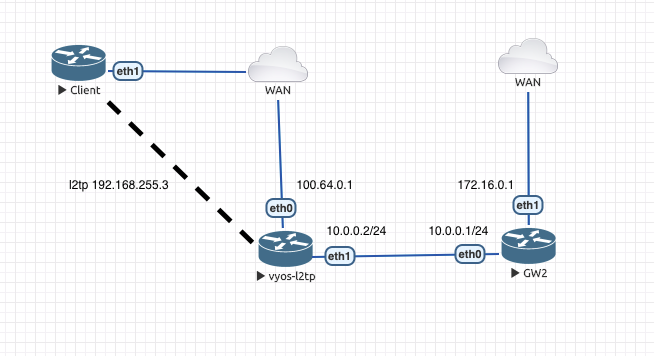
Hello @echowings, I reproduced this schema in our laboratory, and I think I have workaround.
On
GW2 needs to add static route to l2tp client
set protocols static route 192.168.255.0/24 next-hop 10.0.0.2
And in VyOS-l2tp node add ip rule (not VyOS CLI command)
sudo ip rule add from 192.168.255.0/24 table 100
#and
set protocols static table 100 route 0.0.0.0/0 next-hop 10.0.0.1
ps:// Thanks @Viacheslav for idea