Hi all,
I tried to deploy the VPN IKEv2 Remote Access follow as this article PKI and IPSec IKEv2 remote-access VPN
The VPN works well, however, after a lifetime expired, VPN rekeying of IKE_SA failed.
I tried to upgrade to the latest OS version, but it is still not fixed.
For debug purpose, I reduce lifetime and setting like this for ike and esp set vpn ipsec esp-group ESP-RW lifetime '300', set vpn ipsec ike-group IKE-RW lifetime '600'
Can anyone help resolve this issue?
> ESP/0x253ce0b0/113.161.114.150
Feb 2 18:33:54 vpn-stg charon: 09[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 36 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:33:54 vpn-stg charon: 09[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:33:54 vpn-stg charon: 08[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:33:54 vpn-stg charon: 08[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 36 [ SA No TSi TSr KE ]
Feb 2 18:33:54 vpn-stg charon: 08[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:33:54 vpn-stg charon: 08[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{22} established with SPIs ca82a3af_i 1b27189e_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:33:54 vpn-stg charon: 08[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{22} established with SPIs ca82a3af_i 1b27189e_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:33:54 vpn-stg charon: 08[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{21} with SPIs c9b6f917_i (60 bytes) 253ce0b0_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:33:54 vpn-stg charon: 08[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c9b6f917
Feb 2 18:33:54 vpn-stg charon: 08[ENC] <ra-rw|3> generating INFORMATIONAL request 37 [ D ]
Feb 2 18:33:54 vpn-stg charon: 08[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:33:54 vpn-stg charon: 12[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:33:54 vpn-stg charon: 12[ENC] <ra-rw|3> parsed INFORMATIONAL response 37 [ D ]
Feb 2 18:33:54 vpn-stg charon: 12[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 253ce0b0
Feb 2 18:33:54 vpn-stg charon: 12[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:35:36 vpn-stg charon: 16[KNL] creating rekey job for CHILD_SA ESP/0x1b27189e/113.161.114.150
Feb 2 18:35:36 vpn-stg charon: 16[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{23} reqid 1
Feb 2 18:35:36 vpn-stg charon: 16[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 38 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:35:36 vpn-stg charon: 16[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:35:36 vpn-stg charon: 07[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:35:36 vpn-stg charon: 07[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 38 [ SA No TSi TSr KE ]
Feb 2 18:35:36 vpn-stg charon: 07[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:35:36 vpn-stg charon: 07[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{23} established with SPIs cb329cc3_i d80009ac_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:36 vpn-stg charon: 07[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{23} established with SPIs cb329cc3_i d80009ac_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:36 vpn-stg charon: 07[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{22} with SPIs ca82a3af_i (6060 bytes) 1b27189e_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:36 vpn-stg charon: 07[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI ca82a3af
Feb 2 18:35:36 vpn-stg charon: 07[ENC] <ra-rw|3> generating INFORMATIONAL request 39 [ D ]
Feb 2 18:35:36 vpn-stg charon: 07[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:35:36 vpn-stg charon: 08[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:35:36 vpn-stg charon: 08[ENC] <ra-rw|3> parsed INFORMATIONAL response 39 [ D ]
Feb 2 18:35:36 vpn-stg charon: 08[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 1b27189e
Feb 2 18:35:36 vpn-stg charon: 08[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:35:37 vpn-stg charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xcb329cc3/192.168.200.2
Feb 2 18:35:37 vpn-stg charon: 12[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{24} reqid 1
Feb 2 18:35:37 vpn-stg charon: 12[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 40 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:35:37 vpn-stg charon: 12[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:35:37 vpn-stg charon: 13[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:35:37 vpn-stg charon: 13[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 40 [ SA No TSi TSr KE ]
Feb 2 18:35:37 vpn-stg charon: 13[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:35:37 vpn-stg charon: 13[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{24} established with SPIs cb18ad62_i 4e420842_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:37 vpn-stg charon: 13[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{24} established with SPIs cb18ad62_i 4e420842_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:37 vpn-stg charon: 13[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{23} with SPIs cb329cc3_i (60 bytes) d80009ac_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:37 vpn-stg charon: 13[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI cb329cc3
Feb 2 18:35:37 vpn-stg charon: 13[ENC] <ra-rw|3> generating INFORMATIONAL request 41 [ D ]
Feb 2 18:35:37 vpn-stg charon: 13[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:35:37 vpn-stg charon: 11[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:35:37 vpn-stg charon: 11[ENC] <ra-rw|3> parsed INFORMATIONAL response 41 [ D ]
Feb 2 18:35:37 vpn-stg charon: 11[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI d80009ac
Feb 2 18:35:37 vpn-stg charon: 11[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:35:38 vpn-stg charon: 05[KNL] creating rekey job for CHILD_SA ESP/0x4e420842/113.161.114.150
Feb 2 18:35:38 vpn-stg charon: 05[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{25} reqid 1
Feb 2 18:35:38 vpn-stg charon: 05[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 42 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:35:38 vpn-stg charon: 05[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:35:38 vpn-stg charon: 15[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:35:38 vpn-stg charon: 15[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 42 [ SA No TSi TSr KE ]
Feb 2 18:35:38 vpn-stg charon: 15[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:35:38 vpn-stg charon: 15[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{25} established with SPIs c12144d8_i 91317486_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:38 vpn-stg charon: 15[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{25} established with SPIs c12144d8_i 91317486_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:38 vpn-stg charon: 15[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{24} with SPIs cb18ad62_i (60 bytes) 4e420842_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:38 vpn-stg charon: 15[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI cb18ad62
Feb 2 18:35:38 vpn-stg charon: 15[ENC] <ra-rw|3> generating INFORMATIONAL request 43 [ D ]
Feb 2 18:35:38 vpn-stg charon: 15[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:35:38 vpn-stg charon: 06[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:35:38 vpn-stg charon: 06[ENC] <ra-rw|3> parsed INFORMATIONAL response 43 [ D ]
Feb 2 18:35:38 vpn-stg charon: 06[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 4e420842
Feb 2 18:35:38 vpn-stg charon: 06[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:35:39 vpn-stg charon: 09[KNL] creating rekey job for CHILD_SA ESP/0xc12144d8/192.168.200.2
Feb 2 18:35:39 vpn-stg charon: 09[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{26} reqid 1
Feb 2 18:35:39 vpn-stg charon: 07[KNL] creating rekey job for CHILD_SA ESP/0x91317486/113.161.114.150
Feb 2 18:35:39 vpn-stg charon: 09[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 44 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:35:39 vpn-stg charon: 09[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:35:39 vpn-stg charon: 10[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:35:39 vpn-stg charon: 10[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 44 [ SA No TSi TSr KE ]
Feb 2 18:35:39 vpn-stg charon: 10[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:35:39 vpn-stg charon: 10[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{26} established with SPIs c7b021c9_i ec2a4426_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:39 vpn-stg charon: 10[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{26} established with SPIs c7b021c9_i ec2a4426_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:39 vpn-stg charon: 10[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{25} with SPIs c12144d8_i (60 bytes) 91317486_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:39 vpn-stg charon: 10[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c12144d8
Feb 2 18:35:39 vpn-stg charon: 10[ENC] <ra-rw|3> generating INFORMATIONAL request 45 [ D ]
Feb 2 18:35:39 vpn-stg charon: 10[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:35:39 vpn-stg charon: 12[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:35:39 vpn-stg charon: 12[ENC] <ra-rw|3> parsed INFORMATIONAL response 45 [ D ]
Feb 2 18:35:39 vpn-stg charon: 12[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 91317486
Feb 2 18:35:39 vpn-stg charon: 12[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:35:40 vpn-stg charon: 14[KNL] creating rekey job for CHILD_SA ESP/0xc7b021c9/192.168.200.2
Feb 2 18:35:40 vpn-stg charon: 14[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{27} reqid 1
Feb 2 18:35:40 vpn-stg charon: 14[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 46 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:35:40 vpn-stg charon: 14[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:35:40 vpn-stg charon: 15[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:35:40 vpn-stg charon: 15[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 46 [ SA No TSi TSr KE ]
Feb 2 18:35:40 vpn-stg charon: 15[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:35:40 vpn-stg charon: 15[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{27} established with SPIs ce9183fd_i 8c71e0d6_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:40 vpn-stg charon: 15[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{27} established with SPIs ce9183fd_i 8c71e0d6_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:40 vpn-stg charon: 15[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{26} with SPIs c7b021c9_i (60 bytes) ec2a4426_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:35:40 vpn-stg charon: 15[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c7b021c9
Feb 2 18:35:40 vpn-stg charon: 15[ENC] <ra-rw|3> generating INFORMATIONAL request 47 [ D ]
Feb 2 18:35:40 vpn-stg charon: 15[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:35:40 vpn-stg charon: 06[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:35:40 vpn-stg charon: 06[ENC] <ra-rw|3> parsed INFORMATIONAL response 47 [ D ]
Feb 2 18:35:40 vpn-stg charon: 06[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI ec2a4426
Feb 2 18:35:40 vpn-stg charon: 06[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:36:57 vpn-stg charon: 12[KNL] creating rekey job for CHILD_SA ESP/0xce9183fd/192.168.200.2
Feb 2 18:36:57 vpn-stg charon: 12[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{28} reqid 1
Feb 2 18:36:57 vpn-stg charon: 12[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 48 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:36:57 vpn-stg charon: 12[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:36:57 vpn-stg charon: 11[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:36:57 vpn-stg charon: 11[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 48 [ SA No TSi TSr KE ]
Feb 2 18:36:57 vpn-stg charon: 11[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:36:57 vpn-stg charon: 11[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{28} established with SPIs c2955b5d_i e87e0f62_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:57 vpn-stg charon: 11[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{28} established with SPIs c2955b5d_i e87e0f62_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:57 vpn-stg charon: 11[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{27} with SPIs ce9183fd_i (4560 bytes) 8c71e0d6_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:57 vpn-stg charon: 11[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI ce9183fd
Feb 2 18:36:57 vpn-stg charon: 11[ENC] <ra-rw|3> generating INFORMATIONAL request 49 [ D ]
Feb 2 18:36:57 vpn-stg charon: 11[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:36:57 vpn-stg charon: 05[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:36:57 vpn-stg charon: 05[ENC] <ra-rw|3> parsed INFORMATIONAL response 49 [ D ]
Feb 2 18:36:57 vpn-stg charon: 05[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 8c71e0d6
Feb 2 18:36:57 vpn-stg charon: 05[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:36:58 vpn-stg charon: 14[KNL] creating rekey job for CHILD_SA ESP/0xc2955b5d/192.168.200.2
Feb 2 18:36:58 vpn-stg charon: 14[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{29} reqid 1
Feb 2 18:36:58 vpn-stg charon: 14[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 50 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:36:58 vpn-stg charon: 14[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:36:58 vpn-stg charon: 06[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:36:58 vpn-stg charon: 06[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 50 [ SA No TSi TSr KE ]
Feb 2 18:36:58 vpn-stg charon: 06[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:36:58 vpn-stg charon: 06[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{29} established with SPIs ccfee335_i 3190579c_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:58 vpn-stg charon: 06[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{29} established with SPIs ccfee335_i 3190579c_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:58 vpn-stg charon: 06[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{28} with SPIs c2955b5d_i (60 bytes) e87e0f62_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:36:58 vpn-stg charon: 06[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c2955b5d
Feb 2 18:36:58 vpn-stg charon: 06[ENC] <ra-rw|3> generating INFORMATIONAL request 51 [ D ]
Feb 2 18:36:58 vpn-stg charon: 06[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:36:58 vpn-stg charon: 16[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:36:58 vpn-stg charon: 16[ENC] <ra-rw|3> parsed INFORMATIONAL response 51 [ D ]
Feb 2 18:36:58 vpn-stg charon: 16[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI e87e0f62
Feb 2 18:36:58 vpn-stg charon: 16[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:37:35 vpn-stg charon: 15[KNL] creating rekey job for CHILD_SA ESP/0x3190579c/113.161.114.150
Feb 2 18:37:35 vpn-stg charon: 15[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{30} reqid 1
Feb 2 18:37:35 vpn-stg charon: 15[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 52 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:37:35 vpn-stg charon: 15[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:37:35 vpn-stg charon: 06[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:37:35 vpn-stg charon: 06[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 52 [ SA No TSi TSr KE ]
Feb 2 18:37:35 vpn-stg charon: 06[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:37:35 vpn-stg charon: 06[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{30} established with SPIs c2a20387_i 2955c5de_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:35 vpn-stg charon: 06[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{30} established with SPIs c2a20387_i 2955c5de_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:35 vpn-stg charon: 06[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{29} with SPIs ccfee335_i (2160 bytes) 3190579c_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:35 vpn-stg charon: 06[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI ccfee335
Feb 2 18:37:35 vpn-stg charon: 06[ENC] <ra-rw|3> generating INFORMATIONAL request 53 [ D ]
Feb 2 18:37:35 vpn-stg charon: 06[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:37:35 vpn-stg charon: 16[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:37:35 vpn-stg charon: 16[ENC] <ra-rw|3> parsed INFORMATIONAL response 53 [ D ]
Feb 2 18:37:35 vpn-stg charon: 16[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 3190579c
Feb 2 18:37:35 vpn-stg charon: 16[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:37:36 vpn-stg charon: 08[KNL] creating rekey job for CHILD_SA ESP/0xc2a20387/192.168.200.2
Feb 2 18:37:36 vpn-stg charon: 08[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{31} reqid 1
Feb 2 18:37:36 vpn-stg charon: 07[KNL] creating rekey job for CHILD_SA ESP/0x2955c5de/113.161.114.150
Feb 2 18:37:36 vpn-stg charon: 08[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 54 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:37:36 vpn-stg charon: 08[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:37:36 vpn-stg charon: 13[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:37:36 vpn-stg charon: 13[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 54 [ SA No TSi TSr KE ]
Feb 2 18:37:36 vpn-stg charon: 13[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:37:36 vpn-stg charon: 13[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{31} established with SPIs ca86c175_i d56224a0_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:36 vpn-stg charon: 13[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{31} established with SPIs ca86c175_i d56224a0_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:36 vpn-stg charon: 13[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{30} with SPIs c2a20387_i (60 bytes) 2955c5de_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:36 vpn-stg charon: 13[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c2a20387
Feb 2 18:37:36 vpn-stg charon: 13[ENC] <ra-rw|3> generating INFORMATIONAL request 55 [ D ]
Feb 2 18:37:36 vpn-stg charon: 13[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:37:36 vpn-stg charon: 12[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:37:36 vpn-stg charon: 12[ENC] <ra-rw|3> parsed INFORMATIONAL response 55 [ D ]
Feb 2 18:37:36 vpn-stg charon: 12[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 2955c5de
Feb 2 18:37:36 vpn-stg charon: 12[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:37:37 vpn-stg charon: 05[KNL] creating rekey job for CHILD_SA ESP/0xca86c175/192.168.200.2
Feb 2 18:37:37 vpn-stg charon: 05[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{32} reqid 1
Feb 2 18:37:37 vpn-stg charon: 15[KNL] creating rekey job for CHILD_SA ESP/0xd56224a0/113.161.114.150
Feb 2 18:37:37 vpn-stg charon: 05[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 56 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:37:37 vpn-stg charon: 05[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:37:37 vpn-stg charon: 16[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:37:37 vpn-stg charon: 16[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 56 [ SA No TSi TSr KE ]
Feb 2 18:37:37 vpn-stg charon: 16[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:37:37 vpn-stg charon: 16[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{32} established with SPIs c7497d71_i 2fdcb24c_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:37 vpn-stg charon: 16[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{32} established with SPIs c7497d71_i 2fdcb24c_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:37 vpn-stg charon: 16[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{31} with SPIs ca86c175_i (60 bytes) d56224a0_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:37 vpn-stg charon: 16[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI ca86c175
Feb 2 18:37:37 vpn-stg charon: 16[ENC] <ra-rw|3> generating INFORMATIONAL request 57 [ D ]
Feb 2 18:37:37 vpn-stg charon: 16[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:37:37 vpn-stg charon: 09[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:37:37 vpn-stg charon: 09[ENC] <ra-rw|3> parsed INFORMATIONAL response 57 [ D ]
Feb 2 18:37:37 vpn-stg charon: 09[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI d56224a0
Feb 2 18:37:37 vpn-stg charon: 09[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:37:38 vpn-stg charon: 10[KNL] creating rekey job for CHILD_SA ESP/0x2fdcb24c/113.161.114.150
Feb 2 18:37:38 vpn-stg charon: 10[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{33} reqid 1
Feb 2 18:37:38 vpn-stg charon: 10[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 58 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:37:38 vpn-stg charon: 10[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:37:38 vpn-stg charon: 07[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:37:38 vpn-stg charon: 07[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 58 [ SA No TSi TSr KE ]
Feb 2 18:37:38 vpn-stg charon: 07[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:37:38 vpn-stg charon: 07[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{33} established with SPIs c30d2813_i 15b5a338_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:38 vpn-stg charon: 07[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{33} established with SPIs c30d2813_i 15b5a338_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:38 vpn-stg charon: 07[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{32} with SPIs c7497d71_i (60 bytes) 2fdcb24c_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:38 vpn-stg charon: 07[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c7497d71
Feb 2 18:37:38 vpn-stg charon: 07[ENC] <ra-rw|3> generating INFORMATIONAL request 59 [ D ]
Feb 2 18:37:38 vpn-stg charon: 07[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:37:38 vpn-stg charon: 13[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:37:38 vpn-stg charon: 13[ENC] <ra-rw|3> parsed INFORMATIONAL response 59 [ D ]
Feb 2 18:37:38 vpn-stg charon: 13[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 2fdcb24c
Feb 2 18:37:38 vpn-stg charon: 13[IKE] <ra-rw|3> CHILD_SA closed
Feb 2 18:37:39 vpn-stg charon: 06[KNL] creating rekey job for CHILD_SA ESP/0x15b5a338/113.161.114.150
Feb 2 18:37:39 vpn-stg charon: 06[IKE] <ra-rw|3> establishing CHILD_SA ikev2-vpn{34} reqid 1
Feb 2 18:37:39 vpn-stg charon: 06[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 60 [ N(REKEY_SA) SA No KE TSi TSr ]
Feb 2 18:37:39 vpn-stg charon: 06[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (501 bytes)
Feb 2 18:37:39 vpn-stg charon: 15[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (520 bytes)
Feb 2 18:37:39 vpn-stg charon: 15[ENC] <ra-rw|3> parsed CREATE_CHILD_SA response 60 [ SA No TSi TSr KE ]
Feb 2 18:37:39 vpn-stg charon: 15[CFG] <ra-rw|3> selected proposal: ESP:AES_GCM_16_128/MODP_2048/NO_EXT_SEQ
Feb 2 18:37:39 vpn-stg charon: 15[IKE] <ra-rw|3> inbound CHILD_SA ikev2-vpn{34} established with SPIs c1e2ff76_i e1363df0_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:39 vpn-stg charon: 15[IKE] <ra-rw|3> outbound CHILD_SA ikev2-vpn{34} established with SPIs c1e2ff76_i e1363df0_o and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:39 vpn-stg charon: 15[IKE] <ra-rw|3> closing CHILD_SA ikev2-vpn{33} with SPIs c30d2813_i (60 bytes) 15b5a338_o (0 bytes) and TS 0.0.0.0/0 ::/0 === 10.10.10.1/32
Feb 2 18:37:39 vpn-stg charon: 15[IKE] <ra-rw|3> sending DELETE for ESP CHILD_SA with SPI c30d2813
Feb 2 18:37:39 vpn-stg charon: 15[ENC] <ra-rw|3> generating INFORMATIONAL request 61 [ D ]
Feb 2 18:37:39 vpn-stg charon: 15[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (69 bytes)
Feb 2 18:37:39 vpn-stg charon: 16[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (72 bytes)
Feb 2 18:37:39 vpn-stg charon: 16[ENC] <ra-rw|3> parsed INFORMATIONAL response 61 [ D ]
Feb 2 18:37:39 vpn-stg charon: 16[IKE] <ra-rw|3> received DELETE for ESP CHILD_SA with SPI 15b5a338
Feb 2 18:37:39 vpn-stg charon: 16[IKE] <ra-rw|3> CHILD_SA closed
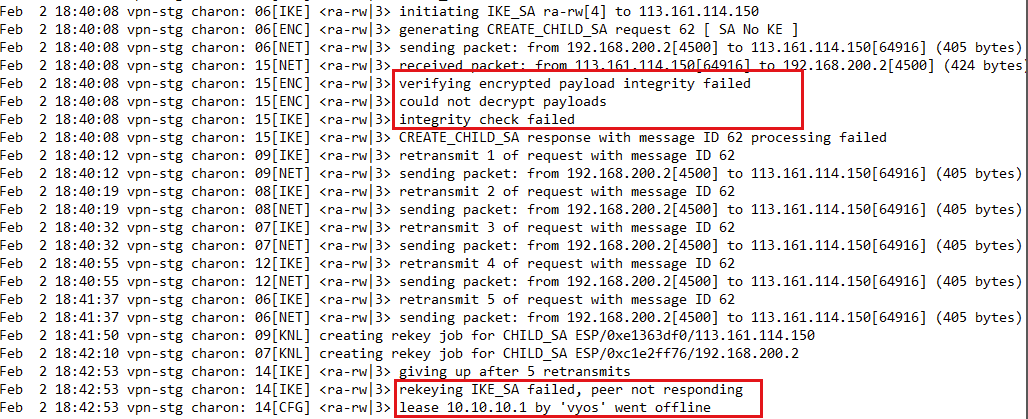
Feb 2 18:40:08 vpn-stg charon: 06[IKE] <ra-rw|3> initiating IKE_SA ra-rw[4] to 113.161.114.150
Feb 2 18:40:08 vpn-stg charon: 06[ENC] <ra-rw|3> generating CREATE_CHILD_SA request 62 [ SA No KE ]
Feb 2 18:40:08 vpn-stg charon: 06[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:40:08 vpn-stg charon: 15[NET] <ra-rw|3> received packet: from 113.161.114.150[64916] to 192.168.200.2[4500] (424 bytes)
Feb 2 18:40:08 vpn-stg charon: 15[ENC] <ra-rw|3> verifying encrypted payload integrity failed
Feb 2 18:40:08 vpn-stg charon: 15[ENC] <ra-rw|3> could not decrypt payloads
Feb 2 18:40:08 vpn-stg charon: 15[IKE] <ra-rw|3> integrity check failed
Feb 2 18:40:08 vpn-stg charon: 15[IKE] <ra-rw|3> CREATE_CHILD_SA response with message ID 62 processing failed
Feb 2 18:40:12 vpn-stg charon: 09[IKE] <ra-rw|3> retransmit 1 of request with message ID 62
Feb 2 18:40:12 vpn-stg charon: 09[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:40:19 vpn-stg charon: 08[IKE] <ra-rw|3> retransmit 2 of request with message ID 62
Feb 2 18:40:19 vpn-stg charon: 08[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:40:32 vpn-stg charon: 07[IKE] <ra-rw|3> retransmit 3 of request with message ID 62
Feb 2 18:40:32 vpn-stg charon: 07[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:40:55 vpn-stg charon: 12[IKE] <ra-rw|3> retransmit 4 of request with message ID 62
Feb 2 18:40:55 vpn-stg charon: 12[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:41:37 vpn-stg charon: 06[IKE] <ra-rw|3> retransmit 5 of request with message ID 62
Feb 2 18:41:37 vpn-stg charon: 06[NET] <ra-rw|3> sending packet: from 192.168.200.2[4500] to 113.161.114.150[64916] (405 bytes)
Feb 2 18:41:50 vpn-stg charon: 09[KNL] creating rekey job for CHILD_SA ESP/0xe1363df0/113.161.114.150
Feb 2 18:42:10 vpn-stg charon: 07[KNL] creating rekey job for CHILD_SA ESP/0xc1e2ff76/192.168.200.2
Feb 2 18:42:53 vpn-stg charon: 14[IKE] <ra-rw|3> giving up after 5 retransmits
Feb 2 18:42:53 vpn-stg charon: 14[IKE] <ra-rw|3> rekeying IKE_SA failed, peer not responding
Feb 2 18:42:53 vpn-stg charon: 14[CFG] <ra-rw|3> lease 10.10.10.1 by 'vyos' went offline
logs rekeying failed.txt (60.4 KB)