I noticed odd behavior of some systems not immediately obtaining DNS servers after reboot/wakeup from sleep. After looking at what RAs are actually being sent I noticed that VyOS is sending RAs that only contain the prefixes every 10 seconds, even though my config does not contain any custom interval and the default is 0.33*600 - 600 according to the radvd docs. (And also according to the actual written /run/radvd/radvd.conf)
# show service router-advert | strip-private
interface bond0.100 {
dnssl xxx.xxx
link-mtu 1492
name-server xxxx:xxxx:xxxx::53:1
name-server xxxx:xxxx:xxxx::53:2
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
[...]
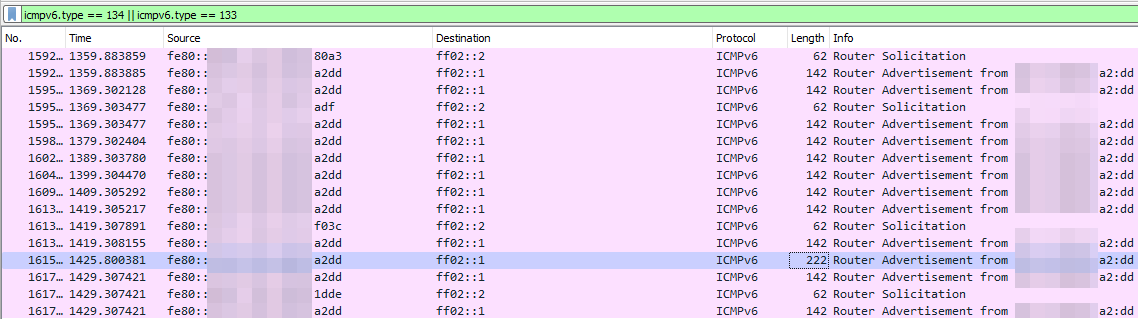
Matching the actual interval of radvd (every ~250-500s), I get RAs that contain not only the prefix but also the DNSSL, MTU and RDNSS. I also noticed that Router Solicitations are also answered with short RAs, lacking all options except the prefixes.
Any clue where the RAs every 10s come from and why Solicitation also get short answers?
VyOS Version: 1.4-rolling-202205200217
1 Like
This is still happening on 1.4-rolling-202210090955 and since no one replied here I took another look:
It seems like the invalid RAs are coming from zebra and not radvd like I assumed before. I looked what processes have sockets for ICMPv6 open and it listed both radvd and zebra (sudo ss -6w0pt | grep icmp). To confirm it I stopped the radvd service and then only the invalid RAs kept coming.
Now the next question is, why is zebra sending RAs too?
Here is almost my full config (removed parts are marked):
Config
firewall {
[... removed ...]
}
interfaces {
bonding bond0 {
ipv6 {
address {
no-default-link-local
}
}
member {
interface eth1
interface eth0
}
mode 802.3ad
vif 100 {
address xxx.xxx.0.1/24
address xxxx:xxxx::1/64
}
vif 101 {
address xxx.xxx.1.1/24
}
vif 102 {
address xxx.xxx.2.1/24
address xxxx:xxxx::1/64
}
vif 103 {
address xxx.xxx.3.1/24
address xxxx:xxxx::1/64
}
vif 130 {
address xxx.xxx.30.1/24
address xxxx:xxxx::1/64
}
vif 201 {
address xxx.xxx.42.1/24
}
}
ethernet eth0 {
hw-id xx:xx:xx:xx:xx:dc
}
ethernet eth1 {
hw-id xx:xx:xx:xx:xx:dd
}
ethernet eth2 {
hw-id xx:xx:xx:xx:xx:de
}
ethernet eth3 {
hw-id xx:xx:xx:xx:xx:df
}
ethernet eth4 {
hw-id xx:xx:xx:xx:xx:f6
}
loopback lo {
}
pppoe pppoe0 {
authentication {
password xxxxxx
user xxxxxx
}
dhcpv6-options {
pd 0 {
interface bond0.100 {
address 1
sla-id 0
}
interface bond0.101 {
address 1
sla-id 1
}
interface bond0.102 {
address 1
sla-id 2
}
interface bond0.103 {
address 1
sla-id 3
}
interface bond0.201 {
address 1
sla-id 101
}
length 56
}
}
ip {
adjust-mss 1452
}
ipv6 {
address {
autoconf
}
}
no-peer-dns
source-interface bond0.130
}
}
nat {
[... removed ...]
}
pki {
[... removed ...]
}
protocols {
bgp {
neighbor xxx.xxx.0.33 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxx.xxx.0.34 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxx.xxx.0.44 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxx.xxx.0.45 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxxx:xxxx:e36a {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxxx:xxxx:80a3 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxxx:xxxx:c061 {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
neighbor xxxx:xxxx:f03c {
description xxx.xxx.xx
interface {
source-interface bond0.100
}
peer-group xxx
}
parameters {
router-id xxx.xxx.0.1
}
peer-group xxx {
address-family {
ipv4-unicast {
}
ipv6-unicast {
}
}
capability {
dynamic
extended-nexthop
}
remote-as internal
update-source bond0.100
}
system-as 64512
}
static {
route xxx.xxx.0.0/0 {
next-hop xxx.xxx.0.1 {
}
}
route6 xxxx:xxxx::/96 {
next-hop xxxx:xxxx::64 {
}
}
}
}
service {
dhcp-server {
shared-network-name xxxxxx {
authoritative
subnet xxx.xxx.0.0/24 {
default-router xxx.xxx.0.1
range 0 {
start xxx.xxx.0.10
stop xxx.xxx.0.254
}
[... removed static mappings ...]
}
}
shared-network-name xxxxxx {
authoritative
domain-search xxxxxx
name-server xxx.xxx.0.53
name-server xxx.xxx.0.54
subnet xxx.xxx.1.0/24 {
default-router xxx.xxx.1.1
range 0 {
start xxx.xxx.1.10
stop xxx.xxx.1.254
}
}
}
shared-network-name xxxxxx {
authoritative
subnet xxx.xxx.2.0/24 {
default-router xxx.xxx.2.1
range 0 {
start xxx.xxx.2.10
stop xxx.xxx.2.254
}
}
}
shared-network-name xxxxxx {
authoritative
domain-search xxxxxx
name-server xxx.xxx.0.53
name-server xxx.xxx.0.54
subnet xxx.xxx.3.0/24 {
default-router xxx.xxx.3.1
range 0 {
start xxx.xxx.3.10
stop xxx.xxx.3.200
}
[... removed static mappings ...]
}
}
shared-network-name xxxxxx {
authoritative
name-server xxx.xxx.1.1
name-server xxx.xxx.0.1
subnet xxx.xxx.42.0/24 {
default-router xxx.xxx.42.1
range 0 {
start xxx.xxx.42.10
stop xxx.xxx.42.254
}
}
}
}
dns {
dynamic {
interface pppoe0 {
rfc2136 ns1 {
key xxxxxx
record xxx.xxx.xx
server xxxxx.tld
ttl 120
zone xxx.xx
}
}
}
}
https {
api {
keys {
id xxx {
key xxxxxx
}
}
}
certificates {
certificate self-signed
}
}
router-advert {
interface bond0.100 {
dnssl xxx.xx
interval {
max 20
min 10
}
link-mtu 1492
name-server xxxx:xxxx:4c6::53:1
name-server xxxx:xxxx:4c6::53:2
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
interface bond0.101 {
dnssl xxx.xx
link-mtu 1492
name-server xxxx:xxxx:4c6::53:1
name-server xxxx:xxxx:4c6::53:2
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
interface bond0.102 {
dnssl xxx.xx
link-mtu 1492
name-server xxxx:xxxx:4c6::53:2
name-server xxxx:xxxx:4c6::53:1
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
interface bond0.103 {
dnssl xxx.xx
link-mtu 1492
name-server xxxx:xxxx:4c6::53:1
name-server xxxx:xxxx:4c6::53:2
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
interface bond0.130 {
link-mtu 1492
}
interface bond0.201 {
link-mtu 1492
name-server xxxx:xxxx:4700::1111
name-server xxxx:xxxx:4700::1001
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
interface vti0 {
name-server xxxx:xxxx:4c6::53:1
name-server xxxx:xxxx:4c6::53:2
prefix ::/64 {
preferred-lifetime 7200
valid-lifetime 86400
}
}
}
ssh {
disable-password-authentication
}
}
system {
config-management {
commit-revisions 1000
}
conntrack {
modules {
ftp
h323
nfs
pptp
sip
sqlnet
tftp
}
}
console {
device ttyS0 {
speed 115200
}
}
host-name xxxxxx
login {
banner {
post-login ""
}
user xxxxxx {
authentication {
encrypted-password xxxxxx
plaintext-password xxxxxx
public-keys xxxx@xxx.xxx {
key xxxxxx
type ssh-ed25519
}
}
}
}
name-server xxxx:xxxx:4c6::53:1
name-server xxxx:xxxx:4c6::53:2
ntp {
server xxxxx.tld {
}
server xxxxx.tld {
}
server xxxxx.tld {
}
}
syslog {
global {
facility all {
level info
}
facility protocols {
level debug
}
}
}
}
vpn {
ipsec {
esp-group esp-ra {
lifetime 3600
pfs disable
proposal 10 {
encryption aes128gcm128
hash sha256
}
}
ike-group ike-ra {
key-exchange ikev2
lifetime 7200
proposal 10 {
dh-group 14
encryption aes128gcm128
hash sha256
}
}
log {
level 2
subsystem cfg
}
options {
virtual-ip
}
remote-access {
connection ra {
authentication {
client-mode eap-mschapv2
local-id xxx.xxx.xx
local-users {
username xxxxxx {
password xxxxxx
}
username xxxxxx {
password xxxxxx
}
}
server-mode x509
x509 {
ca-certificate ipsec
certificate ipsec
}
}
esp-group esp-ra
ike-group ike-ra
local {
}
pool ra-ra-ipv4
pool ra-ra-ipv6
}
pool ra-ra-ipv4 {
prefix xxx.xxx.4.0/24
}
pool ra-ra-ipv6 {
name-server xxxx:xxxx::53:1
name-server xxxx:xxxx::53:2
prefix xxxx:xxxx:xxxx::/64
}
}
}
}
1 Like