Hi Guys
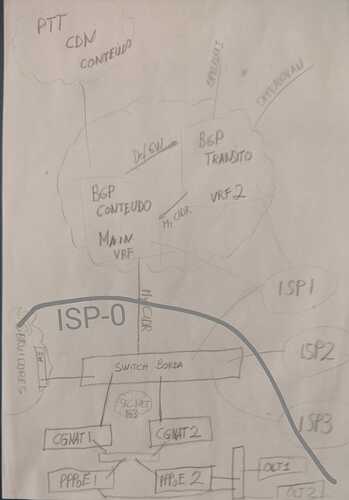
We’ve been worked with @c-po and we were able to add different new features on VYOS , I think it can be useful regarding INTRA-VRF routing with bgp ,let me show :
the scenario is that we have 3 vrf (CDN/MAIN/TRANSIT ) this case is just an example : MAIN can import all the prefixes , CDN can only import the prefix of a client 80.80.80.80/32 and TRANSIT export the DF-GW :
set vrf name CDN protocols bgp address-family ipv4-unicast export vpn
set vrf name CDN protocols bgp address-family ipv4-unicast import vpn
set vrf name CDN protocols bgp address-family ipv4-unicast network 172.16.50.0/24
set vrf name CDN protocols bgp address-family ipv4-unicast rd vpn export '65001:1050'
set vrf name CDN protocols bgp address-family ipv4-unicast redistribute connected
set vrf name CDN protocols bgp address-family ipv4-unicast redistribute static
set vrf name CDN protocols bgp address-family ipv4-unicast route-target vpn export '65001:1050'
set vrf name CDN protocols bgp address-family ipv4-unicast route-target vpn import '65001:1050'
set vrf name CDN protocols bgp local-as '65001'
set vrf name CDN protocols bgp neighbor 172.16.50.2 address-family ipv4-unicast
set vrf name CDN protocols bgp neighbor 172.16.50.2 ebgp-multihop '2'
set vrf name CDN protocols bgp neighbor 172.16.50.2 remote-as '65050'
set vrf name CDN protocols bgp parameters default no-ipv4-unicast
set vrf name MAIN protocols bgp address-family ipv4-unicast export vpn
set vrf name MAIN protocols bgp address-family ipv4-unicast import vpn
set vrf name MAIN protocols bgp address-family ipv4-unicast network 10.70.70.0/24
set vrf name MAIN protocols bgp address-family ipv4-unicast rd vpn export '65001:1011'
set vrf name MAIN protocols bgp address-family ipv4-unicast redistribute connected
set vrf name MAIN protocols bgp address-family ipv4-unicast route-map vpn export 'EXPORT-VPN'
set vrf name MAIN protocols bgp address-family ipv4-unicast route-target vpn export '65001:1011'
set vrf name MAIN protocols bgp address-family ipv4-unicast route-target vpn import '65001:1011 65001:1050 65001:1080'
set vrf name MAIN protocols bgp local-as '65001'
set vrf name MAIN protocols bgp neighbor 10.70.70.2 address-family ipv4-unicast
set vrf name MAIN protocols bgp neighbor 10.70.70.2 ebgp-multihop '2'
set vrf name MAIN protocols bgp neighbor 10.70.70.2 remote-as '65035'
set vrf name MAIN protocols bgp parameters default no-ipv4-unicast
set vrf name TRANSIT protocols bgp address-family ipv4-unicast export vpn
set vrf name TRANSIT protocols bgp address-family ipv4-unicast import vpn
set vrf name TRANSIT protocols bgp address-family ipv4-unicast network 192.168.80.0/24
set vrf name TRANSIT protocols bgp address-family ipv4-unicast rd vpn export '65001:1080'
set vrf name TRANSIT protocols bgp address-family ipv4-unicast redistribute connected
set vrf name TRANSIT protocols bgp address-family ipv4-unicast redistribute static
set vrf name TRANSIT protocols bgp address-family ipv4-unicast route-target vpn export '65001:1080'
set vrf name TRANSIT protocols bgp address-family ipv4-unicast route-target vpn import '65001:1080'
set vrf name TRANSIT protocols bgp local-as '65001'
set vrf name TRANSIT protocols bgp neighbor 192.168.80.2 address-family ipv4-unicast
set vrf name TRANSIT protocols bgp neighbor 192.168.80.2 ebgp-multihop '2'
set vrf name TRANSIT protocols bgp neighbor 192.168.80.2 remote-as '65040'
set vrf name TRANSIT protocols bgp parameters default no-ipv4-unicast
if we can see the tables , the MAIN vrf has all the prefixes :
[edit] run show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
VRF CDN:
K>* 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 01:40:52
S>* 8.8.8.0/24 [1/0] is directly connected, eth2, weight 1, 00:34:58
B>* 20.20.20.0/24 [20/0] via 172.16.50.2, eth2, weight 1, 01:00:12
B>* 80.80.80.0/24 [200/0] via 10.70.70.2, eth0 (vrf MAIN), weight 1, 00:16:40
C>* 172.16.50.0/24 is directly connected, eth2, 01:40:41
VRF MAIN:
B>* 0.0.0.0/0 [200/0] is directly connected, eth1 (vrf TRANSIT), weight 1, 00:19:26
K * 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 01:40:52
B>* 8.8.8.0/24 [200/0] is directly connected, eth2 (vrf CDN), weight 1, 00:16:42
C>* 10.70.70.0/24 is directly connected, eth0, 01:40:43
B>* 20.20.20.0/24 [200/0] via 172.16.50.2, eth2 (vrf CDN), weight 1, 00:16:42
B>* 80.80.80.0/24 [20/0] via 10.70.70.2, eth0, weight 1, 01:00:26
B 172.16.50.0/24 [200/0] is directly connected, unknown (vrf CDN) inactive, weight 1, 00:19:26
B 192.168.80.0/24 [200/0] is directly connected, unknown (vrf TRANSIT) inactive, weight 1, 00:19:26
VRF TRANSIT:
S>* 0.0.0.0/0 [1/0] is directly connected, eth1, weight 1, 00:32:30
K * 0.0.0.0/0 [255/8192] unreachable (ICMP unreachable), 01:40:51
C>* 192.168.80.0/24 is directly connected, eth1, 00:35:46
we applied a route-map that only allows exporting theprefix 80.80.80.80/32 , but you can set any rules(community/prefix/as-path):
set policy prefix-list IPV4-EXPORT rule 10 action 'permit'
set policy prefix-list IPV4-EXPORT rule 10 le '32'
set policy prefix-list IPV4-EXPORT rule 10 prefix '80.80.80.0/24'
set policy route-map EXPORT-VPN rule 10 action 'permit'
set policy route-map EXPORT-VPN rule 10 match ip address prefix-list 'IPV4-EXPORT'
set policy route-map EXPORT-VPN rule 20 action 'deny'
we are able to communicate between MAIN/CDN
$ ping 20.20.20.20 interface 80.80.80.80
PING 20.20.20.20 (20.20.20.20) from 80.80.80.80 : 56(84) bytes of data.
64 bytes from 20.20.20.20: icmp_seq=1 ttl=63 time=5.72 ms
64 bytes from 20.20.20.20: icmp_seq=2 ttl=63 time=4.60 ms
^C
--- 20.20.20.20 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 4.597/5.158/5.720/0.561 ms