Hi!
i’m using VyOS 1.4-rolling-202204300743
ive setup an ipsec tunnel with an external host, using an ip as local prefix on the vyos side that doesnt exist/isnt attached to a machine.
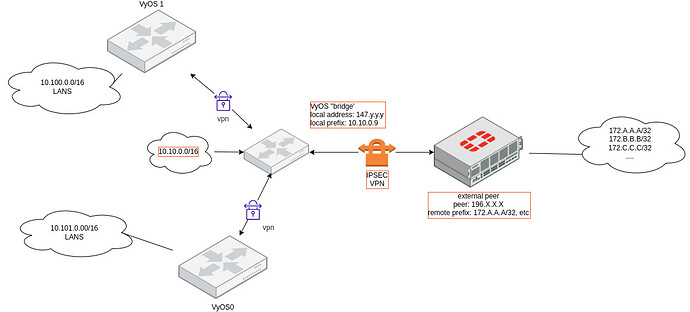
the vyos is a ‘bridge’ that is used allow other vti-connected devices/networks, to connect to some remote destinations, through the ipsec tunnel that the vyos ‘bridge’ forms with external remote peers.
the vyos ‘bridge’ itself has currently no active lan devices connected to it, but it has configuration for such (it used to have).
the vyos ‘bridge’ external ip is 147.y.y.y, internal subnet is 10.10.0.0/16, of which local prefix is selected to be 10.10.0.9. (note 10.10.0.9 does not exist/is not attached to anything.)
the vpn external peer is 196.x.x.x and has a number of /32 remote prefixes which are grouped under 172.24.96.0/20 for ease of SNATing. the rule i have landed upon after lots of attempts to SNAT, is
set nat source rule 10 destination address '172.24.96.0/20'
set nat source rule 10 outbound-interface 'eth0'
set nat source rule 10 source address '147.y.y.y'
set nat source rule 10 translation address '10.10.0.9'
tunnel is up, i can see what looks like traffic going through the tunnel, but no response from the other side (attempting nc to one of the remote prefixes):
peer_196-x-x-x_tunnel_0 up 38m9s 0B/1K 0B/22B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
peer_196-x-x-x_tunnel_1 up 38m8s 0B/ 0B/0B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
peer_196-x-x-x_tunnel_2 up 38m8s 0B/0B 0B/0B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
peer_196-x-x-x_tunnel_3 up 38m8s 0B/0B 0B/0B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
peer_196-x-x-x_tunnel_4 up 38m8s 0B/0B 0B/0B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
peer_196-x-x-x_tunnel_5 up 38m8s 0B/0B 0B/0B 196.x.x.x 196.x.x.x AES_CBC_256/HMAC_SHA1_96
and tcpdump on eth0 does not show SNAT for traffic coming from sources, to the destination ips subnet (172.24.96.0/20), it still shows the vyos ‘bridge’ external address:
# tcpdump -nn -i eth0 net 172.24.96.0/20 or host 10.10.0.9
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
09:13:33.492522 IP 147.y.y.y.42436 > 172.24.98.155.10500: Flags [S], seq 302933062, win 29200, options [mss 1460,sackOK,TS val 1017169204 ecr 0,nop,wscale 7], length 0
09:13:34.511727 IP 147.y.y.y.42436 > 172.24.98.155.10500: Flags [S], seq 302933062, win 29200, options [mss 1460,sackOK,TS val 1017170223 ecr 0,nop,wscale 7], length 0
09:13:36.559555 IP 147.y.y.y.42436 > 172.24.98.155.10500: Flags [S], seq 302933062, win 29200, options [mss 1460,sackOK,TS val 1017172271 ecr 0,nop,wscale 7], length 0
09:13:40.591799 IP 147.y.y.y.42436 > 172.24.98.155.10500: Flags [S], seq 302933062, win 29200, options [mss 1460,sackOK,TS val 1017176303 ecr 0,nop,wscale 7], length 0
09:13:48.847607 IP 147.y.y.y.42436 > 172.24.98.155.10500: Flags [S], seq 302933062, win 29200, options [mss 1460,sackOK,TS val 1017184558 ecr 0,nop,wscale 7], length 0
how can i be sure that traffic is correctly being SNATed to 10.10.0.9? is my source rule sufficient? am i doing anything wrong?