Hello there.
Need help with L2TP “authentication mode radius”
local user authentication mode works fine.
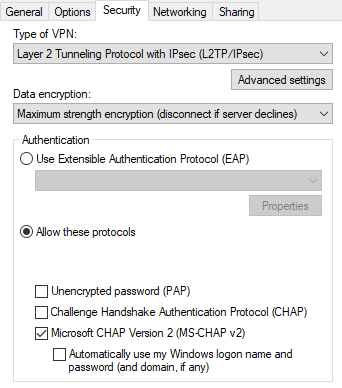
adding the RADIUS authentication gives the problem with Win10 clients.
vyos is recent rolling release
RADIUS server is WINDOWS SERVER 2019 with AD
Linux (UBUNTU 20.20) and IOS worked very fine.
But for Windows 10 connection being established after authentication log filled by
Jun 06 13:45:35 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=226 <00fd>]
Jun 06 13:45:35 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=237 <00fd>]
...
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=3 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=4 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=5 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=6 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=7 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=8 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=9 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=10 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=11 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=12 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=13 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=14 <00fd>]
Jun 06 13:45:37 vyos-router.local accel-l2tp[6881]: l2tp0:DOMAIN\USER: send [LCP ProtoRej id=15 <00fd>]and channel just falls down
Configuration very simple
l2tp {
remote-access {
authentication {
mode radius
mppe prefer
radius {
server 192.168.1.50 {
key <radius-key>
port 1812
}
source-address 192.168.1.13
}
require chap
require mschap
require mschap-v2
}
client-ip-pool {
start 192.168.1.126
stop 192.168.1.135
}
gateway-address 192.168.1.13
/* gateway-address 192.168.1.7 */
idle 3600
ipsec-settings {
authentication {
mode pre-shared-secret
pre-shared-secret <preshared-secret-key>
}
ike-lifetime 3600
lifetime 120
}
name-server 192.168.1.50
outside-address xxx.xxx.xxx.222
}
}Any idea and/or help will be highly appreciated.
what message [LCP ProtoRej id=8 <00fd>] really meant?
Thanks