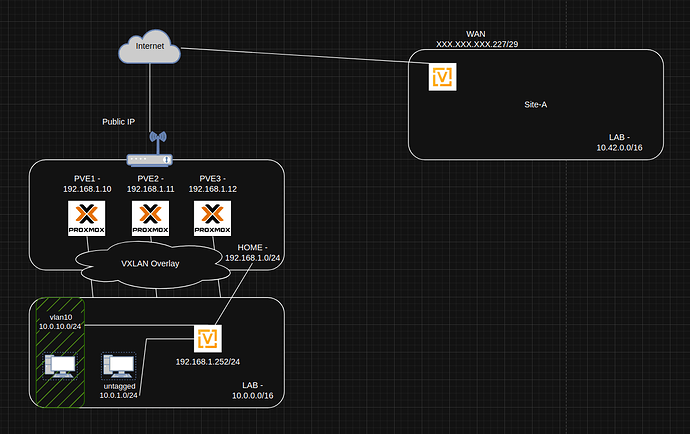
I am testing site-2-site config out and struggling to get the ipsec to come up.
- Site-A :
- public IP on bond0.4000.
- Version: VyOS 1.4.1
- Home :
- static public ip on router and port forward 500_udp 4500_udp to 192.168.1.252 (vyos)
- Version: VyOS 1.5-rolling-202501290006
SITE-A ipsec config
set vpn ipsec authentication psk sitea id ‘sitea’
set vpn ipsec authentication psk sitea id ‘home’
set vpn ipsec authentication psk sitea secret xxxxxx
set vpn ipsec esp-group ESP-DEMO lifetime ‘3600’
set vpn ipsec esp-group ESP-DEMO mode ‘tunnel’
set vpn ipsec esp-group ESP-DEMO pfs ‘dh-group19’
set vpn ipsec esp-group ESP-DEMO proposal 1 encryption ‘aes256’
set vpn ipsec esp-group ESP-DEMO proposal 1 hash ‘sha256’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection action ‘restart’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection interval ‘10’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection timeout ‘30’
set vpn ipsec ike-group IKE-DEMO key-exchange ‘ikev2’
set vpn ipsec ike-group IKE-DEMO lifetime ‘28800’
set vpn ipsec ike-group IKE-DEMO proposal 1 dh-group ‘19’
set vpn ipsec ike-group IKE-DEMO proposal 1 encryption ‘aes256’
set vpn ipsec ike-group IKE-DEMO proposal 1 hash ‘sha256’
set vpn ipsec interface ‘bond0.4000’
set vpn ipsec log level ‘2’
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer sitea authentication local-id ‘sitea’
set vpn ipsec site-to-site peer sitea authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer sitea authentication remote-id ‘home’
set vpn ipsec site-to-site peer sitea connection-type ‘respond’
set vpn ipsec site-to-site peer sitea default-esp-group ‘ESP-DEMO’
set vpn ipsec site-to-site peer sitea description ‘demo ipsec (1)’
set vpn ipsec site-to-site peer sitea force-udp-encapsulation
set vpn ipsec site-to-site peer sitea ike-group ‘IKE-DEMO’
set vpn ipsec site-to-site peer sitea ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer sitea local-address ‘10.100.0.2’
set vpn ipsec site-to-site peer sitea remote-address ‘xxx.xxx.219.34’
set vpn ipsec site-to-site peer sitea vti bind ‘vti0’
set vpn ipsec site-to-site peer sitea vti esp-group ‘ESP-DEMO’
Home
set vpn ipsec authentication psk home id ‘home’
set vpn ipsec authentication psk home id ‘sitea’
set vpn ipsec authentication psk home secret xxxxxx
set vpn ipsec esp-group ESP-DEMO lifetime ‘3600’
set vpn ipsec esp-group ESP-DEMO mode ‘tunnel’
set vpn ipsec esp-group ESP-DEMO pfs ‘dh-group19’
set vpn ipsec esp-group ESP-DEMO proposal 1 encryption ‘aes256’
set vpn ipsec esp-group ESP-DEMO proposal 1 hash ‘sha256’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection action ‘restart’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection interval ‘10’
set vpn ipsec ike-group IKE-DEMO dead-peer-detection timeout ‘30’
set vpn ipsec ike-group IKE-DEMO key-exchange ‘ikev2’
set vpn ipsec ike-group IKE-DEMO lifetime ‘28800’
set vpn ipsec ike-group IKE-DEMO proposal 1 dh-group ‘19’
set vpn ipsec ike-group IKE-DEMO proposal 1 encryption ‘aes256’
set vpn ipsec ike-group IKE-DEMO proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth1’
set vpn ipsec log level ‘2’
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer sitea authentication local-id ‘home’
set vpn ipsec site-to-site peer sitea authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer sitea authentication remote-id ‘sitea’
set vpn ipsec site-to-site peer sitea connection-type ‘initiate’
set vpn ipsec site-to-site peer sitea default-esp-group ‘ESP-DEMO’
set vpn ipsec site-to-site peer sitea description ‘demo ipsec (1)’
set vpn ipsec site-to-site peer sitea force-udp-encapsulation
set vpn ipsec site-to-site peer sitea ike-group ‘IKE-DEMO’
set vpn ipsec site-to-site peer sitea ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer sitea local-address ‘10.100.0.1’
set vpn ipsec site-to-site peer sitea remote-address ‘xxx.xxx.27.227’
set vpn ipsec site-to-site peer sitea vti bind ‘vti0’
set vpn ipsec site-to-site peer sitea vti esp-group ‘ESP-DEMO’
On Site-A side:
# run show vpn ike status
Feb 10 13:29:59 firewall-1 charon[3220210]: 06[NET] <119> received packet: from xx.xx.219.34[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:29:59 firewall-1 charon[3220210]: 06[ENC] <119> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Feb 10 13:29:59 firewall-1 charon-systemd[3220210]: received packet: from xx.xx.219.34[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:29:59 firewall-1 charon[3220210]: 06[IKE] <119> no IKE config found for xx.xx.27.227...xx.xx.219.34, sending NO_PROPOSAL_CHOSEN
Feb 10 13:29:59 firewall-1 charon-systemd[3220210]: parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
Feb 10 13:29:59 firewall-1 charon[3220210]: 06[ENC] <119> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Feb 10 13:29:59 firewall-1 charon-systemd[3220210]: no IKE config found for xx.xx.27.227...xx.xx.219.34, sending NO_PROPOSAL_CHOSEN
Feb 10 13:29:59 firewall-1 charon[3220210]: 06[NET] <119> sending packet: from xx.xx.27.227[500] to xx.xx.219.34[500] (36 bytes)
Feb 10 13:29:59 firewall-1 charon-systemd[3220210]: generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
Feb 10 13:29:59 firewall-1 charon-systemd[3220210]: sending packet: from xx.xx.27.227[500] to xx.xx.219.34[500] (36 bytes)
Home:
# run show vpn ike status
Feb 10 13:31:39 firewall charon[1054845]: 13[NET] <home|1> sending packet: from 10.100.0.1[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:31:39 firewall charon-systemd[1054845]: sending packet: from 10.100.0.1[500] to xx.98xx27.227[500] (272 bytes)
Feb 10 13:32:02 firewall charon[1054845]: 14[IKE] <home|1> retransmit 4 of request with message ID 0
Feb 10 13:32:02 firewall charon-systemd[1054845]: retransmit 4 of request with message ID 0
Feb 10 13:32:02 firewall charon[1054845]: 14[NET] <home|1> sending packet: from 10.100.0.1[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:32:02 firewall charon-systemd[1054845]: sending packet: from 10.100.0.1[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:32:44 firewall charon[1054845]: 10[IKE] <home|1> retransmit 5 of request with message ID 0
Feb 10 13:32:44 firewall charon-systemd[1054845]: retransmit 5 of request with message ID 0
Feb 10 13:32:44 firewall charon[1054845]: 10[NET] <home|1> sending packet: from 10.100.0.1[500] to xx.xx.27.227[500] (272 bytes)
Feb 10 13:32:44 firewall charon-systemd[1054845]: sending packet: from 10.100.0.1[500] to xx.xx.27.227[500] (272 bytes)
Any pointers on where start troubleshooting?