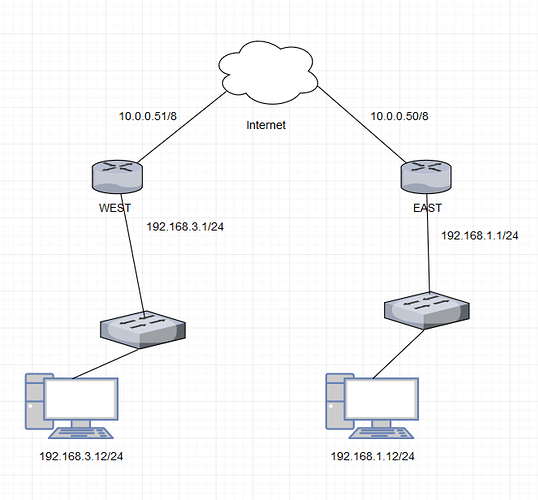
I have two routers, WEST and EAST, and want to set up a site-to-site IPsec connection between them. WEST has a WAN IP of 10.0.0.50/8, and a LAN IP of 192.168.3.1/24. EAST has a WAN IP of 10.0.0.51/8, and a LAN IP of 192.168.1.1/24. Here is a diagram that explains my setup:
I set up WEST with the basic configuration in the User Guide. Here are the relevant parts:
nat {
source {
rule 10 {
destination {
address 192.168.1.0/24
}
exclude
outbound-interface eth0
source {
address 192.168.3.0/24
}
}
rule 100 {
destination {
address 0.0.0.0/0
}
outbound-interface eth0
source {
address 192.168.3.0/24
}
translation {
address masquerade
}
}
}
}
firewall {
name OUTSIDE-LOCAL {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
rule 20 {
action accept
icmp {
type-name echo-request
}
protocol icmp
state {
new enable
}
}
rule 30 {
action drop
destination {
port 22
}
protocol tcp
recent {
count 4
time 60
}
state {
new enable
}
}
rule 31 {
action accept
destination {
port 22
}
protocol tcp
}
rule 32 {
action accept
source {
address 192.168.1.0/24
}
}
}
}
vpn {
ipsec {
esp-group ESP-1W {
compression disable
lifetime 1800
mode tunnel
pfs enable
proposal 1 {
encryption aes256
hash sha1
}
proposal 2 {
encryption 3des
hash md5
}
}
ike-group IKE-1W {
ikev2-reauth no
key-exchange ikev1
lifetime 3600
proposal 1 {
encryption aes256
hash sha1
}
proposal 2 {
encryption aes128
hash sha1
}
}
ipsec-interfaces {
interface eth0
}
site-to-site {
peer 10.0.0.50 {
authentication {
mode pre-shared-secret
pre-shared-secret ****************
}
connection-type initiate
default-esp-group ESP-1W
ike-group IKE-1W
ikev2-reauth inherit
local-address 10.0.0.51
tunnel 1 {
allow-nat-networks disable
allow-public-networks disable
local {
prefix 192.168.3.0/24
}
remote {
prefix 192.168.1.0/24
}
}
}
}
}
}
And here are the relevant parts of EAST’s configuration:
firewall {
name OUTSIDE-LOCAL {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
rule 20 {
action accept
icmp {
type-name echo-request
}
protocol icmp
state {
new enable
}
}
rule 30 {
action drop
destination {
port 22
}
protocol tcp
recent {
count 4
time 60
}
state {
new enable
}
}
rule 31 {
action accept
destination {
port 22
}
protocol tcp
state {
new enable
}
}
rule 32 {
action accept
source {
address 192.168.3.0/24
}
}
}
}
nat {
source {
rule 10 {
destination {
address 192.168.3.0/24
}
exclude
outbound-interface eth0
source {
address 192.168.1.0/24
}
}
rule 100 {
outbound-interface eth0
source {
address 192.168.1.0/24
}
translation {
address masquerade
}
}
}
}
vpn {
ipsec {
esp-group ESP-1E {
compression disable
lifetime 1800
mode tunnel
pfs enable
proposal 1 {
encryption aes256
hash sha1
}
proposal 2 {
encryption 3des
hash md5
}
}
ike-group IKE-1E {
ikev2-reauth no
key-exchange ikev1
lifetime 3600
proposal 1 {
encryption aes256
hash sha1
}
proposal 2 {
encryption aes128
hash sha1
}
}
ipsec-interfaces {
interface eth0
}
site-to-site {
peer 10.0.0.51 {
authentication {
mode pre-shared-secret
pre-shared-secret pw
}
connection-type initiate
default-esp-group ESP-1E
ike-group IKE-1E
ikev2-reauth inherit
local-address 10.0.0.50
tunnel 1 {
allow-nat-networks disable
allow-public-networks disable
local {
prefix 192.168.1.0/24
}
remote {
prefix 192.168.3.0/24
}
}
}
}
}
}
The issue
Yesterday, the IPsec connection status was “up” but I was not able to ping hosts from one network to the other (e.g. 192.168.3.1 can’t ping 192.168.1.1). Today, the connection status is “down,” but the configuration is the same. I guess my problem is two-fold: how do I get it back up, and once it is up, how can I talk to the other network?
Logs
Here is the output of sh vpn ike sa on WEST:
Peer ID / IP Local ID / IP
------------ -------------
10.0.0.50 10.0.0.51
Tunnel State Bytes Out/In Encrypt Hash NAT-T A-Time L-Time Proto
------ ----- ------------- ------- ---- ----- ------ ------ -----
1 down n/a n/a n/a no 0 1800 all
And then on EAST:
Peer ID / IP Local ID / IP
------------ -------------
10.0.0.51 10.0.0.50
Tunnel State Bytes Out/In Encrypt Hash NAT-T A-Time L-Time Proto
------ ----- ------------- ------- ---- ----- ------ ------ -----
1 down n/a n/a n/a no 0 1800 all
As for other logs, I’m not sure where they are located.
What I’ve tried
I tried setting it up following the instructions here, but had the same issue. What do you think is causing this, and how can it be fixed? Thanks!