Hi everyone,
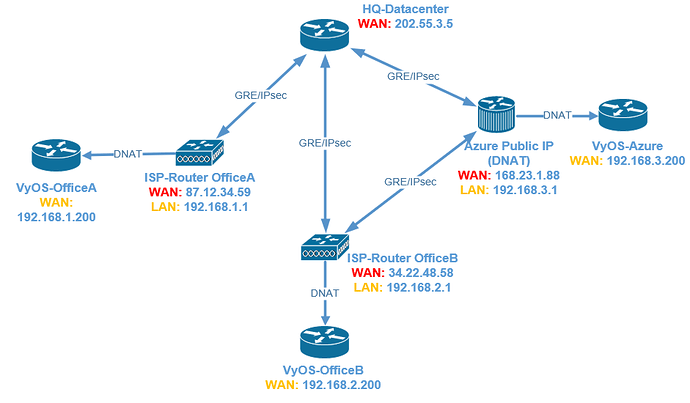
Currently I have a problem / or bug? with GRE / IPSec tunnels, in one location (OfficeB) the IPSec packets (D-port 4500) are temporarily blocked by the INVALID policy of the VyOS firewall.
After a reset of Conntrack or a restart of the router, it usually works again. Has anyone possibly an idea what is the trigger of the problem?
OfficeB builds two IPSec tunnels to different locations for redundancy, and all corporate networks can be reached via both locations (routing via OSPF)
Most of the time, the redundant configuration helps ensure that the site is not completely isolated, but sometimes tunnels are blocked by the VyOS firewall / Invalid State Policy.
The IP, which is blocked by an invalid rule, no longer appears in the conntrack database
I suspect no rough configuration error, because the connection works in principle. The failures then happen between 5 minutes and an hour or more. Some days there are no problems at all.
Office A has no Problems, which has the same VyOS-Configuration.
Firewalling-Method: ZBF
Software Versions:
AZ: VyOS 1.2.0
BranchB: VyOS 1.2
BranchA: VyOS 1.2.1
HQ: VyOS 1.2
vyos@GW-BranchB:~$ sudo journalctl -f | grep -i invalid
Oct 13 16:00:02 GW-BranchB kernel: [FW-STATE_POL-INVALID-D]IN=eth0 OUT= MAC=00:50:56:ae:f4:a7:44:fe:3b:6e:e9:84:08:00 SRC=202.55.3.5 DST=192.168.2.200 LEN=164 TOS=0x00 PREC=0x00 TTL=57 ID=0 DF PROTO=UDP SPT=4500 DPT=4500 LEN=144
Oct 13 16:00:06 GW-BranchB kernel: [FW-STATE_POL-INVALID-D]IN=eth0 OUT= MAC=00:50:56:ae:f4:a7:44:fe:3b:6e:e9:84:08:00 SRC=168.23.1.88 DST=192.168.2.200 LEN=180 TOS=0x00 PREC=0x00 TTL=50 ID=0 DF PROTO=UDP SPT=4500 DPT=4500 LEN=160
Oct 13 16:00:10 GW-BranchB kernel: [FW-STATE_POL-INVALID-D]IN=eth0 OUT= MAC=00:50:56:ae:f4:a7:44:fe:3b:6e:e9:84:08:00 SRC=168.23.1.88 DST=192.168.2.200 LEN=164 TOS=0x00 PREC=0x00 TTL=50 ID=0 DF PROTO=UDP SPT=4500 DPT=4500 LEN=144
Oct 13 16:00:12 GW-BranchB kernel: [FW-STATE_POL-INVALID-D]IN=eth0 OUT= MAC=00:50:56:ae:f4:a7:44:fe:3b:6e:e9:84:08:00 SRC=202.55.3.5 DST=192.168.2.200 LEN=164 TOS=0x00 PREC=0x00 TTL=57 ID=0 DF PROTO=UDP SPT=4500 DPT=4500 LEN=144
Oct 13 16:00:16 GW-BranchB kernel: [FW-STATE_POL-INVALID-D]IN=eth0 OUT= MAC=00:50:56:ae:f4:a7:44:fe:3b:6e:e9:84:08:00 SRC=168.23.1.88 DST=192.168.2.200 LEN=180 TOS=0x00 PREC=0x00 TTL=50 ID=0 DF PROTO=UDP SPT=4500 DPT=4500 LEN=160
vyos@GW-BranchB# sh firewall name anyexternal-local
default-action drop
rule 100 {
action accept
description "Enable ICMP on WAN-Zone"
icmp {
type 8
}
log enable
protocol icmp
}
rule 110 {
action drop
destination {
port 22
}
log enable
protocol tcp
recent {
count 2
time 30
}
}
rule 120 {
action accept
destination {
port 22
}
log enable
protocol tcp
}
rule 130 {
action accept
description "Allow loopback IP-Range"
log enable
source {
address 172.20.1.0/24
}
}
rule 200 {
action accept
description "Allow UDP 500 and 4500 for IPSec and NAT-T"
destination {
port 500,4500
}
log enable
protocol udp
source {
group {
address-group agr_trusted-s2s-sourceips
}
}
}
[edit]
vyos@GW-BranchB# sh nat
source {
rule 10 {
outbound-interface eth0
source {
address 172.26.20.0/24
}
translation {
address masquerade
}
}
}
[edit]
vyos@GW-BranchB# run show vpn ipse sa
Connection State Uptime Bytes In/Out Packets In/Out Remote address Remote ID Proposal
------------------------------------ ------- -------- -------------- ---------------- ---------------- ---------------------- -----------------------------
peer-hq.example.com-tunnel-0 up 1h21m6s 0B/12K 0/141 202.55.3.5 hq.example.com AES_CBC_256/HMAC_SHA2_256_128
peer-az.example.com-tunnel-4 up 1h21m35s 0B/13K 0/160 168.23.1.88 az.example.com AES_CBC_256/HMAC_SHA2_256_128
vyos@GW-branchB# sh vpn
ipsec {
esp-group esp_az-example-com {
compression disable
lifetime 3600
mode tunnel
pfs disable
proposal 1 {
encryption aes256
hash sha256
}
}
esp-group esp_hq-example-com {
compression disable
lifetime 3600
mode tunnel
pfs disable
proposal 1 {
encryption aes256
hash sha256
}
}
ike-group ike_az-example-com {
dead-peer-detection {
action restart
interval 15
timeout 60
}
ikev2-reauth no
key-exchange ikev1
lifetime 7800
proposal 1 {
dh-group 2
encryption aes256
hash sha256
}
}
ike-group ike_hq-example-com {
dead-peer-detection {
action restart
interval 15
timeout 60
}
ikev2-reauth no
key-exchange ikev2
lifetime 7800
proposal 1 {
dh-group 2
encryption aes256
hash sha256
}
}
ipsec-interfaces {
interface eth0
}
nat-networks {
allowed-network 10.0.0.0/24 {
}
allowed-network 172.16.0.0/20 {
}
allowed-network 192.168.0.0/16 {
}
}
nat-traversal enable
site-to-site {
peer az.example.com {
authentication {
id branchb.example.com
mode rsa
remote-id az.example.com
rsa-key-name az.example.com
}
connection-type initiate
default-esp-group esp_az-example-com
ike-group ike_az-example-com
ikev2-reauth inherit
local-address any
tunnel 4 {
allow-nat-networks disable
allow-public-networks disable
local {
prefix 172.20.1.26/32
}
remote {
prefix 172.20.1.27/32
}
}
}
peer hq.example.com {
authentication {
id branchb.example.com
mode rsa
remote-id hq.example.com
rsa-key-name hq.example.com
}
connection-type initiate
default-esp-group esp_hq-example-com
ike-group ike_hq-example-com
ikev2-reauth inherit
local-address any
tunnel 0 {
allow-nat-networks disable
allow-public-networks disable
local {
prefix 172.20.1.26/32
}
remote {
prefix 172.20.1.24/32
}
}
}
}
}
General Firewall Rules
all-ping enable
broadcast-ping disable
config-trap disable
group {
address-group agr_trusted-s2s-sourceips {
address 202.55.3.5
address 168.23.1.88
}
}
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
receive-redirects disable
send-redirects enable
source-validation disable
state-policy {
established {
action accept
}
invalid {
action drop
log {
enable
}
}
related {
action accept
}
}
syn-cookies enable
twa-hazards-protection disable