Hello Guys,
I hope you are all safe. I would like to pick your mind on a little issue. I have a VyOS instance in AWS and I have been able to establish tunnels with the other side. However all my tunnels in the show vpn ipsec sa show tunnel1. That’s my first time seeing this behavior . Maybe that’s what changed in 1.2 as I have only been using 1.1 till now. Below are how I set the vpn up.
set vpn ipsec ipsec-interfaces interface eth0
set vpn ipsec nat-traversal enable
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 proposal 1 dh-group 2
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 proposal 1 hash sha1
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 proposal 1 encryption aes256
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 key-exchange ikev1
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 lifetime 28800
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 dead-peer-detection action restart
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 dead-peer-detection interval 15
set vpn ipsec ike-group IKE-AES256-SHA1-LT2800 dead-peer-detection timeout 30
set vpn ipsec esp-group ESP-AES256-SHA1-LT86400 proposal 1 encryption aes256
set vpn ipsec esp-group ESP-AES256-SHA1-LT86400 proposal 1 hash sha1
set vpn ipsec esp-group ESP-AES256-SHA1-LT86400 lifetime 86400
set vpn ipsec esp-group ESP-AES256-SHA1-LT86400 mode tunnel
set vpn ipsec site-to-site peer xxx.xxx.232.113 authentication mode pre-shared-secret
set vpn ipsec site-to-site peer xxx.xxx.232.113 authentication pre-shared-secret xxxxxxxxxxxxx
set vpn ipsec site-to-site peer xxx.xxx.232.113 default-esp-group ESP-AES256-SHA1-LT86400
set vpn ipsec site-to-site peer xxx.xxx.232.113 ike-group IKE-AES256-SHA1-LT2800
set vpn ipsec site-to-site peer xxx.xxx.232.113 description 'PBL CLOUD-PREMISE Ireland'
set vpn ipsec site-to-site peer xxx.xxx.232.113 local-address 10.30.5.134
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 1 local prefix 10.30.15.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 1 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 2 local prefix 10.30.16.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 2 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 3 local prefix 10.30.17.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 3 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 4 local prefix 10.30.5.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 4 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 5 local prefix 10.30.6.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 5 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 6 local prefix 10.30.7.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 6 remote prefix 10.170.2.136/29
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 7 local prefix 10.30.5.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 7 remote prefix 10.170.133.60/32
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 8 local prefix 10.30.6.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 8 remote prefix 10.170.133.60/32
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 9 local prefix 10.30.7.0/24
set vpn ipsec site-to-site peer xxx.xxx.232.113 tunnel 9 remote prefix 10.170.133.60/32
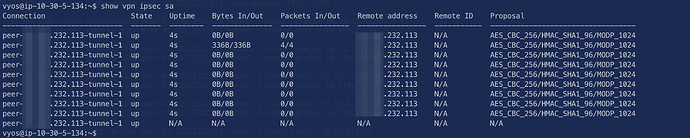
I am expecting to see in ipsec sa tunnels 1 to 9 but instead, I have the following
Here is the exact version I am using:
Version: VyOS 1.2.1-2019-06-04-05-21
Built by: [email protected]
Built on: Tue 04 Jun 2019 05:21 UTC
Build UUID: c625425b-276c-4aab-90b2-8fd4572ae9ab
Build Commit ID: e91ac330b78025-dirty
Architecture: x86_64
Boot via: installed image
System type: Xen HVM guest
Hardware vendor: Xen
Hardware model: HVM domU
Hardware S/N: Unknown
Hardware UUID: Unknown
Copyright: VyOS maintainers and contributors
Is there anything I am doing wrong?
I am also not able to see the ipsec log with the command “monitor log”
Grateful if you can share some pointers on things that are wrong.