Hi RyVolodya
my apology to send previous config without site-to-site vpn
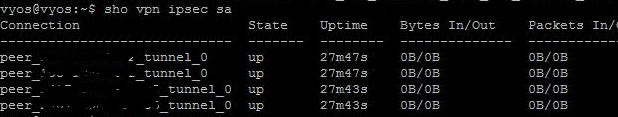
Kindly now find my blow my new config and ipv6 route table for both vyos now site-to-site vpn is there and we try to use ::/0 instead of 0::0/0 but again its not working
Vyos-1
vyos@vyos:~$ sh configuration commands
set firewall ipv6-name FIREWALL_IN_IPV6 default-action ‘drop’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 action ‘accept’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 description ‘Established Connections’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 state established ‘enable’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 state related ‘enable’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 action ‘accept’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 description ‘PING Incoming’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 protocol ‘icmpv6’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 source address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 default-action ‘drop’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 description ‘Established Connections’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 state established ‘enable’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 state related ‘enable’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 description ‘DNS Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 destination port ‘53’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 protocol ‘udp’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 description ‘PING Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 protocol ‘icmpv6’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 source address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 description ‘TCP Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 protocol ‘tcp’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 source address ‘0::0/0’
set firewall ipv6-src-route ‘enable’
set firewall name FIREWALL_IN default-action ‘drop’
set firewall name FIREWALL_IN rule 1 action ‘accept’
set firewall name FIREWALL_IN rule 1 description ‘Established Connections’
set firewall name FIREWALL_IN rule 1 state established ‘enable’
set firewall name FIREWALL_IN rule 1 state related ‘enable’
set firewall name FIREWALL_IN rule 2 action ‘accept’
set firewall name FIREWALL_IN rule 2 description ‘PING Incoming’
set firewall name FIREWALL_IN rule 2 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_IN rule 2 protocol ‘icmp’
set firewall name FIREWALL_IN rule 2 source address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT default-action ‘drop’
set firewall name FIREWALL_OUT rule 1 action ‘accept’
set firewall name FIREWALL_OUT rule 1 description ‘Established Connections’
set firewall name FIREWALL_OUT rule 1 state established ‘enable’
set firewall name FIREWALL_OUT rule 1 state related ‘enable’
set firewall name FIREWALL_OUT rule 2 action ‘accept’
set firewall name FIREWALL_OUT rule 2 description ‘DNS Outgoing’
set firewall name FIREWALL_OUT rule 2 destination port ‘53’
set firewall name FIREWALL_OUT rule 2 protocol ‘udp’
set firewall name FIREWALL_OUT rule 3 action ‘accept’
set firewall name FIREWALL_OUT rule 3 description ‘PING Outgoing’
set firewall name FIREWALL_OUT rule 3 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 3 protocol ‘icmp’
set firewall name FIREWALL_OUT rule 3 source address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 4 action ‘accept’
set firewall name FIREWALL_OUT rule 4 description ‘TCP Outgoing’
set firewall name FIREWALL_OUT rule 4 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 4 protocol ‘tcp’
set firewall name FIREWALL_OUT rule 4 source address ‘0.0.0.0/0’
set interfaces ethernet eth0 address ‘172.17.21.171/16’
set interfaces ethernet eth0 description ‘BLUE-MGMT’
set interfaces ethernet eth1 address ‘xxx:yyy.136.50/24’
set interfaces ethernet eth1 description ‘RED-IPV4’
set interfaces ethernet eth1 firewall in name ‘FIREWALL_IN’
set interfaces ethernet eth2 address ‘10.10.0.1/16’
set interfaces ethernet eth2 description ‘LAN-IPV4’
set interfaces ethernet eth2 firewall out name ‘FIREWALL_OUT’
set interfaces ethernet eth3 address ‘xxxx:yyyy:1::85/48’
set interfaces ethernet eth3 description ‘RED-IPV6’
set interfaces ethernet eth3 firewall in ipv6-name ‘FIREWALL_IN_IPV6’
set interfaces ethernet eth4 address ‘fdeb:b39a:29f8:bfd5::1/64’
set interfaces ethernet eth4 description ‘LAN-IPV6’
set interfaces ethernet eth4 firewall out ipv6-name ‘FIREWALL_OUT_IPV6’
set interfaces loopback lo
set nat source rule 9999 outbound-interface ‘eth1’
set nat source rule 9999 source address ‘10.10.0.0/16’
set nat source rule 9999 translation address ‘masquerade’
set nat66 source rule 9999 outbound-interface ‘eth3’
set nat66 source rule 9999 source prefix ‘fdeb:b39a:29f8:bfd5::/64’
set nat66 source rule 9999 translation address ‘masquerade’
set protocols static route 0.0.0.0/0 next-hop xxx:yyy.136.1
set protocols static route6 ::/0 next-hop xxxx:yyyy:1::1
set service ssh listen-address ‘172.17.21.171’
set service ssh port ‘1024’
set system config-management commit-revisions ‘100’
set system conntrack modules ftp
set system conntrack modules h323
set system conntrack modules nfs
set system conntrack modules pptp
set system conntrack modules sip
set system conntrack modules sqlnet
set system conntrack modules tftp
set system console device ttyS0 speed ‘115200’
set system host-name ‘vyos’
set system login user vyos authentication encrypted-password ‘$6$Vf2wE8loVFa9jFcL$z3.1B.bkQjgHRwPg2lfUpJ2ZQQrT4qJbhvAWC7nYXfBttFDuzQYasNYdRvM72itC7EA0NHFD80/46665hYoMd/’
set system login user vyos authentication plaintext-password ‘’
set system name-server ‘8.8.8.8’
set system name-server ‘8.8.4.4’
set system name-server ‘2001:4860:4860::8888’
set system name-server ‘2001:4860:4860::8844’
set system ntp server time1.vyos.net
set system ntp server time2.vyos.net
set system ntp server time3.vyos.net
set system syslog global facility all level ‘info’
set system syslog global facility protocols level ‘debug’
set system time-zone ‘Asia/Kolkata’
set vpn ipsec esp-group i2k2_ESP compression ‘disable’
set vpn ipsec esp-group i2k2_ESP lifetime ‘3600’
set vpn ipsec esp-group i2k2_ESP mode ‘tunnel’
set vpn ipsec esp-group i2k2_ESP pfs ‘dh-group21’
set vpn ipsec esp-group i2k2_ESP proposal 1 encryption ‘aes256’
set vpn ipsec esp-group i2k2_ESP proposal 1 hash ‘sha512’
set vpn ipsec ike-group i2k2_IKE close-action ‘none’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection action ‘clear’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection interval ‘30’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection timeout ‘90’
set vpn ipsec ike-group i2k2_IKE ikev2-reauth ‘no’
set vpn ipsec ike-group i2k2_IKE key-exchange ‘ikev2’
set vpn ipsec ike-group i2k2_IKE lifetime ‘86400’
set vpn ipsec ike-group i2k2_IKE proposal 1 dh-group ‘21’
set vpn ipsec ike-group i2k2_IKE proposal 1 encryption ‘aes256’
set vpn ipsec ike-group i2k2_IKE proposal 1 hash ‘sha512’
set vpn ipsec interface ‘eth3’
set vpn ipsec log level ‘1’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 authentication id ‘xxxx:yyyy:1::85’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 authentication pre-shared-secret ‘12345678’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 default-esp-group ‘i2k2_ESP’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 ike-group ‘i2k2_IKE’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 local-address ‘xxxx:yyyy:1::85’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 tunnel 0 local prefix ‘fdeb:b39a:29f8:bfd5::/64’
set vpn ipsec site-to-site peer xxxx:yyyy:2::201 tunnel 0 remote prefix ‘fd3f:4f0f:8fce:d02a::/64’
vyos@vyos:~$ show ipv6 route table all
Codes: K - kernel route, C - connected, S - static, R - RIPng,
O - OSPFv3, I - IS-IS, B - BGP, N - NHRP, T - Table,
v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
VRF default table 220:
K>* fd3f:4f0f:8fce:d02a::/64 [0/1024] via xxxx:yyyy:1::1, eth3, src fdeb:b39a:29f8:bfd5::1, 00:01:22
VRF default table 254:
S>* ::/0 [1/0] via xxxx:yyyy:1::1, eth3, weight 1, 3d23h19m
C>* xxxx:yyyy:1::/48 is directly connected, eth3, 4d02h34m
C>* fdeb:b39a:29f8:bfd5::/64 is directly connected, eth4, 4d02h34m
C * fe80::/64 is directly connected, eth3, 4d02h34m
C * fe80::/64 is directly connected, eth4, 4d02h34m
C * fe80::/64 is directly connected, eth1, 4d02h34m
C * fe80::/64 is directly connected, eth0, 4d02h34m
C * fe80::/64 is directly connected, eth2, 4d02h34m
C>* fe80::/64 is directly connected, lo, 4d02h34m
Vyos-2
vyos@vyos:~$ sh configuration commands
set firewall ipv6-name FIREWALL_IN_IPV6 default-action ‘drop’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 action ‘accept’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 description ‘Established Connections’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 state established ‘enable’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 1 state related ‘enable’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 action ‘accept’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 description ‘PING Incoming’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 protocol ‘icmpv6’
set firewall ipv6-name FIREWALL_IN_IPV6 rule 2 source address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 default-action ‘drop’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 description ‘Established Connections’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 state established ‘enable’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 1 state related ‘enable’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 description ‘DNS Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 destination port ‘53’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 2 protocol ‘udp’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 description ‘PING Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 protocol ‘icmpv6’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 3 source address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 action ‘accept’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 description ‘TCP Outgoing’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 destination address ‘0::0/0’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 protocol ‘tcp’
set firewall ipv6-name FIREWALL_OUT_IPV6 rule 4 source address ‘0::0/0’
set firewall ipv6-src-route ‘enable’
set firewall name FIREWALL_IN default-action ‘drop’
set firewall name FIREWALL_IN rule 1 action ‘accept’
set firewall name FIREWALL_IN rule 1 description ‘Established Connections’
set firewall name FIREWALL_IN rule 1 state established ‘enable’
set firewall name FIREWALL_IN rule 1 state related ‘enable’
set firewall name FIREWALL_IN rule 2 action ‘accept’
set firewall name FIREWALL_IN rule 2 description ‘PING Incoming’
set firewall name FIREWALL_IN rule 2 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_IN rule 2 protocol ‘icmp’
set firewall name FIREWALL_IN rule 2 source address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT default-action ‘drop’
set firewall name FIREWALL_OUT rule 1 action ‘accept’
set firewall name FIREWALL_OUT rule 1 description ‘Established Connections’
set firewall name FIREWALL_OUT rule 1 state established ‘enable’
set firewall name FIREWALL_OUT rule 1 state related ‘enable’
set firewall name FIREWALL_OUT rule 2 action ‘accept’
set firewall name FIREWALL_OUT rule 2 description ‘DNS Outgoing’
set firewall name FIREWALL_OUT rule 2 destination port ‘53’
set firewall name FIREWALL_OUT rule 2 protocol ‘udp’
set firewall name FIREWALL_OUT rule 3 action ‘accept’
set firewall name FIREWALL_OUT rule 3 description ‘PING Outgoing’
set firewall name FIREWALL_OUT rule 3 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 3 protocol ‘icmp’
set firewall name FIREWALL_OUT rule 3 source address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 4 action ‘accept’
set firewall name FIREWALL_OUT rule 4 description ‘TCP Outgoing’
set firewall name FIREWALL_OUT rule 4 destination address ‘0.0.0.0/0’
set firewall name FIREWALL_OUT rule 4 protocol ‘tcp’
set firewall name FIREWALL_OUT rule 4 source address ‘0.0.0.0/0’
set interfaces ethernet eth0 address ‘172.17.21.172/16’
set interfaces ethernet eth0 description ‘BLUE-MGMT’
set interfaces ethernet eth1 address ‘xxx:yyy.136.201/24’
set interfaces ethernet eth1 description ‘RED-IPV4’
set interfaces ethernet eth1 firewall in name ‘FIREWALL_IN’
set interfaces ethernet eth2 address ‘10.20.0.1/16’
set interfaces ethernet eth2 description ‘LAN-IPV4’
set interfaces ethernet eth2 firewall out name ‘FIREWALL_OUT’
set interfaces ethernet eth3 address ‘xxxx:yyyy:2::201/48’
set interfaces ethernet eth3 description ‘RED-IPV6’
set interfaces ethernet eth3 firewall in ipv6-name ‘FIREWALL_IN_IPV6’
set interfaces ethernet eth4 address ‘fd3f:4f0f:8fce02a::1/64’
set interfaces ethernet eth4 description ‘LAN-IPV6’
set interfaces ethernet eth4 firewall out ipv6-name ‘FIREWALL_OUT_IPV6’
set interfaces loopback lo
set nat source rule 9999 outbound-interface ‘eth1’
set nat source rule 9999 protocol ‘all’
set nat source rule 9999 source address ‘10.20.0.0/16’
set nat source rule 9999 translation address ‘masquerade’
set nat66 source rule 9999 outbound-interface ‘eth3’
set nat66 source rule 9999 source prefix ‘fd3f:4f0f:8fce02a::/64’
set nat66 source rule 9999 translation address ‘masquerade’
set protocols static route 0.0.0.0/0 next-hop xxx:yyy.136.1
set protocols static route6 ::/0 next-hop xxxx:yyyy:2::1
set service ssh listen-address ‘172.17.21.172’
set service ssh port ‘1024’
set system config-management commit-revisions ‘100’
set system conntrack modules ftp
set system conntrack modules h323
set system conntrack modules nfs
set system conntrack modules pptp
set system conntrack modules sip
set system conntrack modules sqlnet
set system conntrack modules tftp
set system console device ttyS0 speed ‘115200’
set system host-name ‘vyos’
set system login user vyos authentication encrypted-password ‘$6$ikR3GMS/n12713cU$E3M.ngUORr99cHR0/Sz4XFvkjEzgZlqqsglewG7RWzOmvV4txMkk3MiwmJmFDhsQi8nUOh.SmoltDRrKiUMvP/’
set system login user vyos authentication plaintext-password ‘’
set system name-server ‘8.8.8.8’
set system name-server ‘8.8.4.4’
set system name-server ‘2001:4860:4860::8888’
set system name-server ‘2001:4860:4860::8844’
set system ntp server time1.vyos.net
set system ntp server time2.vyos.net
set system ntp server time3.vyos.net
set system syslog global facility all level ‘info’
set system syslog global facility protocols level ‘debug’
set vpn ipsec esp-group i2k2_ESP compression ‘disable’
set vpn ipsec esp-group i2k2_ESP lifetime ‘3600’
set vpn ipsec esp-group i2k2_ESP mode ‘tunnel’
set vpn ipsec esp-group i2k2_ESP pfs ‘dh-group21’
set vpn ipsec esp-group i2k2_ESP proposal 1 encryption ‘aes256’
set vpn ipsec esp-group i2k2_ESP proposal 1 hash ‘sha512’
set vpn ipsec ike-group i2k2_IKE close-action ‘none’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection action ‘clear’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection interval ‘30’
set vpn ipsec ike-group i2k2_IKE dead-peer-detection timeout ‘90’
set vpn ipsec ike-group i2k2_IKE ikev2-reauth ‘no’
set vpn ipsec ike-group i2k2_IKE key-exchange ‘ikev2’
set vpn ipsec ike-group i2k2_IKE lifetime ‘86400’
set vpn ipsec ike-group i2k2_IKE proposal 1 dh-group ‘21’
set vpn ipsec ike-group i2k2_IKE proposal 1 encryption ‘aes256’
set vpn ipsec ike-group i2k2_IKE proposal 1 hash ‘sha512’
set vpn ipsec interface ‘eth3’
set vpn ipsec log level ‘1’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 authentication id ‘xxxx:yyyy:2::201’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 authentication pre-shared-secret ‘12345678’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 default-esp-group ‘i2k2_ESP’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 ike-group ‘i2k2_IKE’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 local-address ‘xxxx:yyyy:2::201’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 tunnel 0 local prefix ‘fd3f:4f0f:8fce:d02a::/64’
set vpn ipsec site-to-site peer xxxx:yyyy:1::85 tunnel 0 remote prefix ‘fdeb:b39a:29f8:bfd5::/64’
vyos@vyos:~$ show ipv6 route table all
Codes: K - kernel route, C - connected, S - static, R - RIPng,
O - OSPFv3, I - IS-IS, B - BGP, N - NHRP, T - Table,
v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
VRF default table 220:
K>* fdeb:b39a:29f8:bfd5::/64 [0/1024] via xxxx:yyyy:2::1, eth3, src fd3f:4f0f:8fce:d02a::1, 00:03:00
VRF default table 254:
S>* ::/0 [1/0] via xxxx:yyyy:2::1, eth3, weight 1, 4d02h36m
C>* xxxx:yyyy:2::/48 is directly connected, eth3, 4d02h36m
C>* fd3f:4f0f:8fce:d02a::/64 is directly connected, eth4, 4d02h36m
C * fe80::/64 is directly connected, eth3, 4d02h36m
C * fe80::/64 is directly connected, eth1, 4d02h36m
C * fe80::/64 is directly connected, eth4, 4d02h36m
C * fe80::/64 is directly connected, eth2, 4d02h36m
C * fe80::/64 is directly connected, eth0, 4d02h36m
C>* fe80::/64 is directly connected, lo, 4d02h36m