Hello Team,
I am a noob in VyOS platform, but got up in a P1 requirement in my organisation where we want to preserve the source client ip.
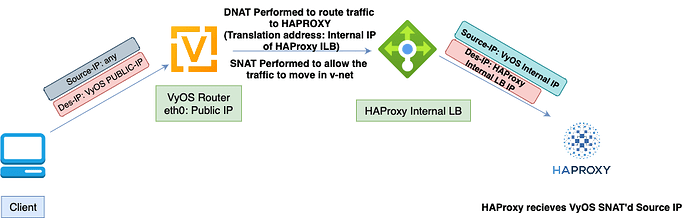
Here we are using VyOS as NAT router or the main frontend appliance holding a public IP.
This VyOS server accepts all INTERNET Traffic and performs DNAT to send this to INTERNAL HAPRoxy LoadBalancer sitting in a Private Kubernetes cluster.
The issue is HAPRoxy always gets VyOS outbound interface internal IP as source IP (as we perform SNAT to pass the request to private local network sitting behind VyOS)
My NAT configuration -
nat {
destination {
rule 100 {
description "route 80,443 to haproxy Internal loadbalancer"
destination {
address 0.0.0.0/0
port 80,443
}
inbound-interface eth0
protocol tcp_udp
translation {
address 10.XXX.XX.XX
}
}
}
source {
rule 100 {
outbound-interface eth1
source {
address !10.0.0.0/8
}
translation {
address masquerade
}
}
}
}
if I remove the Source NAT section then the request gets Timed OUT
Can you please review this scenario and suggest the best way to overcome this blocker?
please suggest any different approach within VyOS?