I’m like three days old to VyOS. Searching for other tunneling options, I’m attempting to switch to it from other more less daunting — let’s say — software like (pf|OPN)Sense/MikrotikCHR.
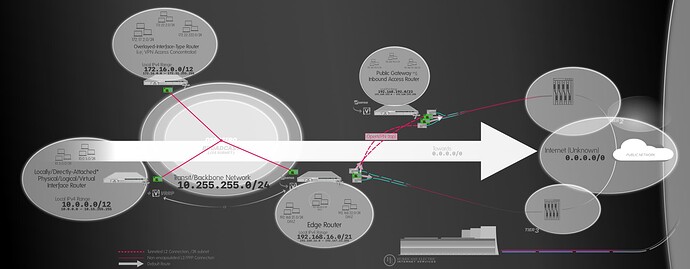
The topology is more or less like this:
I recycled a previous diagram/drawing, please ignore what seems out of place.
It’s a very small network, with a single dynamic IPv4 address. To get around that I rent a server with static addresses and from it*ª , all traffic is forwarded** to the edge where there is much more power available for complex multi-layer filtering. For a time it was even running over an unencrypted OpenVPN link since on the edge, that link is considered a public network (WAN) or worse because it’s attached to FQDNs making it easier to find, but when I learned this is a way used to discover tunnels by companies that report proxies and the like, I set encryption back on of data and control channels.
+ℹ︎
OSPF, virtual IP addresses, and more NAT is used to help targeting the tunneled public IP addresses from all the way down the intranet without logging and having to create rules on every single firewall each time. I think VRF would be a much better way of doing this, but pfSense doesn’t support it on its own.
My plan is to hopefully replace the remote gateway with VyOS and to add another VyOS instance locally to handle the other end of whatever tunnel type I end up using that’s missing from pfSense. While deciding that though I noticed that more than one have some IPsec component on them so I’d like to know if port forwarding would work with these.
On pfSense, it doesn’t without giving up RemoteAccess/RoadWarriod IPsec,
+ℹ︎
personally I used an OpenVPN tap tunnel which performs triple function on the local side;
-
- it’s set as a client on the tunnel network where traffic is forwarded to — 1:1/fullcone NAT to avoid double-natting issues,
-
- it functions as a gateway looking from upstream down, so intranet clients can be reached without NAT,
-
- it’s bridged to a local dark VLAN so if need be, there’s the option for direct L2 to the remote site.
It’s a very flexible protocol but maybe there are better ones, L2TPv3 for instance.
Does NAT (port forwarding) work with IKEv2/VTI/DMVPN//etc-type tunnels or is it like it’s on pfSense?
If not, what other protocols (except for WireGuard—not a fan) can I use for this setup? If OSPF is no compatible with them so be it. I’m on my third day doing this, way too deep to go back and already had to learn the VyOS CLI, the OpenStack CLI, not long ago the FRR CLI and one of my switches’*º. It’d be nice if I get to use this knowledge more than once. It’s taken a while but I’ve coped (very slowly) with the steep learning curve so farºº, but I haven’t been that lucky finding more about this NAT restrictions thing.
Any advice, suggestion, tip, anything really is welcome. Thanks!
*ª, **, *º
*ª: with the exception for the tunnel endpoints used to connect to it.
**: including traffic for the web GUI, then it’s bounced back and forth a couple of times for redirects and all that using NAT on both side and reverse proxying.
*º: surprisingly it was OpenStack the hard part. It’s docu is so dense—it’s like reading in Cyrillic when you only speak English. But, very few cloud providers have unmetered services in the region, so have to bear with it.
ºº: …and then another’s, though that one I didn’t need to, I was just being nosy. ![]()