There is my main configuration to traffic shape PPPoE WAN
set traffic-policy shaper UPLOAD bandwidth '500mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '21mbit'
set traffic-policy shaper UPLOAD class 10 bandwidth '10mbit'
set traffic-policy shaper UPLOAD class 10 match VLAN10 ip source address '192.168.10.0/24'
set traffic-policy shaper UPLOAD default bandwidth '490mbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
set traffic-policy shaper DOWNLOAD bandwidth '600mbit'
set traffic-policy shaper DOWNLOAD class 10 bandwidth '10mbit'
set traffic-policy shaper DOWNLOAD class 10 ceiling '21mbit'
set traffic-policy shaper DOWNLOAD class 10 match VLAN10 ip destination address '192.168.10.0/24'
set traffic-policy shaper DOWNLOAD default bandwidth '590mbit'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set interfaces input ifb1 traffic-policy out 'UPLOAD'
set interfaces pppoe pppoe0 redirect 'ifb1'
set interfaces pppoe pppoe0 traffic-policy out 'DOWNLOAD'
Absolutely nothing is shaped…
Your UPLOAD policy does not work because of the mentioned bug.
And your DOWNLOAD policy does not work because you are trying to match as destination addresses your private addresses on the outbound traffic.
So What is the best way actually to limit only WAN speed and not LAN speed? I think that what i’ve done above limit LAN network too.
Can you give me a good example of traffic shaping WAN interface with bandwidth and ceiling for a specific LAN ?
Take this example, being WAN interface eth1:
set traffic-policy shaper UPLOAD class 12 bandwidth '12%'
set traffic-policy shaper UPLOAD class 12 ceiling '10mbit'
set traffic-policy shaper UPLOAD class 12 match VLAN12 ip source address '192.168.12.0/24'
set traffic-policy shaper UPLOAD default bandwidth '1kbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
set traffic-policy shaper UPLOAD default priority '7'
set interfaces ethernet eth1 traffic-policy out UPLOAD
set traffic-policy shaper DOWNLOAD bandwidth '400mbit'
set traffic-policy shaper DOWNLOAD class 12 bandwidth '12%'
set traffic-policy shaper DOWNLOAD class 12 ceiling '60mbit'
set traffic-policy shaper DOWNLOAD class 12 match VLAN12 ip destination address '192.168.12.0/24'
set traffic-policy shaper DOWNLOAD default bandwidth '1kbit'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set traffic-policy shaper DOWNLOAD default priority '7'
set interfaces ethernet eth1 redirect 'ifb1'
set interfaces input ifb1 traffic-policy out 'DOWNLOAD'
You can forget last command on priority. It is just saying that the ceiling for default is the last one it has to fill.
Well even with this config applied to the PPPoE WAN Interface. Nothing happens…
This config seems to limit UPLOAD speed well!
set traffic-policy shaper UPLOAD bandwidth '500mbit'
set traffic-policy shaper UPLOAD class 10 bandwidth '50mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '61mbit'
set traffic-policy shaper UPLOAD class 10 match VLAN10 interface eth4.10
set traffic-policy shaper UPLOAD default bandwidth '400mbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
set interfaces pppoe pppoe0 traffic-policy out 'UPLOAD'
set traffic-policy shaper UPLOAD class 10 match VLAN10 interface eth4.10
Do you know if this line is a good match? For me it seems to be a good one. ip destination or ip source didn’t work.
I’m still trying to get it work for the download. If you have idea…
I can confirm that no redirection is done with redirect on pppoe interface.
I get a setup with a DHCP WAN instead of PPPoE and nothing is working…
This is my interfaces
vyos@vyos:~$ show interfaces
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address S/L Description
--------- ---------- --- -----------
eth0 147.253.160.191/25 u/u WAN
eth1 192.168.1.1/24 u/u LAN
eth2 - A/D
eth3 - A/D
lo 127.0.0.1/8 u/u
::1/128
This is my traffic shaping config
set traffic-policy shaper UPLOAD bandwidth '10mbit'
set traffic-policy shaper UPLOAD class 12 bandwidth '5mbit'
set traffic-policy shaper UPLOAD class 12 ceiling '5mbit'
set traffic-policy shaper UPLOAD class 12 match LAN ip source address '192.168.1.0/24'
set traffic-policy shaper UPLOAD default bandwidth '1kbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
set interfaces ethernet eth0 traffic-policy out UPLOAD
set traffic-policy shaper DOWNLOAD bandwidth '15mbit'
set traffic-policy shaper DOWNLOAD class 12 bandwidth '5mbit'
set traffic-policy shaper DOWNLOAD class 12 ceiling '5mbit'
set traffic-policy shaper DOWNLOAD class 12 match LAN ip destination address '192.168.1.0/24'
set traffic-policy shaper DOWNLOAD default bandwidth '1kbit'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set interfaces ethernet eth0 redirect 'ifb1'
set interfaces input ifb1 traffic-policy out 'DOWNLOAD'
This is my whole configuration
set firewall all-ping 'enable'
set firewall broadcast-ping 'disable'
set firewall config-trap 'disable'
set firewall ipv6-receive-redirects 'disable'
set firewall ipv6-src-route 'disable'
set firewall ip-src-route 'disable'
set firewall log-martians 'enable'
set firewall name LAN_IN default-action 'accept'
set firewall name LAN_IN rule 10 action 'drop'
set firewall name LAN_IN rule 10 destination address '192.168.0.0/16'
set firewall name LAN_IN rule 10 source address '192.168.0.0/16'
set firewall name WAN_IN default-action 'drop'
set firewall name WAN_IN rule 10 action 'accept'
set firewall name WAN_IN rule 10 state established 'enable'
set firewall name WAN_IN rule 10 state related 'enable'
set firewall name WAN_LOCAL default-action 'drop'
set firewall name WAN_LOCAL rule 10 action 'accept'
set firewall name WAN_LOCAL rule 10 state established 'enable'
set firewall name WAN_LOCAL rule 10 state related 'enable'
set firewall name WAN_LOCAL rule 20 action 'accept'
set firewall name WAN_LOCAL rule 20 icmp type-name 'echo-request'
set firewall name WAN_LOCAL rule 20 protocol 'icmp'
set firewall name WAN_LOCAL rule 20 state new 'enable'
set firewall name WAN_LOCAL rule 30 action 'drop'
set firewall name WAN_LOCAL rule 30 destination port '22'
set firewall name WAN_LOCAL rule 30 protocol 'tcp'
set firewall name WAN_LOCAL rule 30 recent count '4'
set firewall name WAN_LOCAL rule 30 recent time '60'
set firewall name WAN_LOCAL rule 30 state new 'enable'
set firewall name WAN_LOCAL rule 31 action 'accept'
set firewall name WAN_LOCAL rule 31 destination port '22'
set firewall name WAN_LOCAL rule 31 protocol 'tcp'
set firewall name WAN_LOCAL rule 31 state new 'enable'
set firewall receive-redirects 'disable'
set firewall send-redirects 'enable'
set firewall source-validation 'disable'
set firewall syn-cookies 'enable'
set firewall twa-hazards-protection 'disable'
set interfaces ethernet eth0 address 'dhcp'
set interfaces ethernet eth0 description 'WAN'
set interfaces ethernet eth0 firewall in name 'WAN_IN'
set interfaces ethernet eth0 firewall local name 'WAN_LOCAL'
set interfaces ethernet eth0 hw-id '00:a0:c9:69:80:7b'
set interfaces ethernet eth0 redirect 'ifb1'
set interfaces ethernet eth0 traffic-policy out 'UPLOAD'
set interfaces ethernet eth1 address '192.168.1.1/24'
set interfaces ethernet eth1 description 'LAN'
set interfaces ethernet eth1 firewall in name 'LAN_IN'
set interfaces ethernet eth1 hw-id '00:a0:c9:69:80:7c'
set interfaces ethernet eth1 policy
set interfaces ethernet eth2 hw-id '00:a0:c9:69:80:7d'
set interfaces ethernet eth3 hw-id '00:a0:c9:69:80:7e'
set interfaces input ifb1 traffic-policy out 'DOWNLOAD'
set interfaces loopback lo
set nat source rule 100 outbound-interface 'eth0'
set nat source rule 100 translation address 'masquerade'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 default-router '192.168.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 lease '86400'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range 0 start '192.168.1.10'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range 0 stop '192.168.1.254'
set service ssh port '22'
set system config-management commit-revisions '100'
set system console device ttyS0 speed '115200'
set system host-name 'vyos'
set system login user vyos authentication encrypted-password '$6$9RjedjecvB9$GhTyfAOg2RRc77gPFa64SOZqE714md1cXh3L9w6HIiVagqjuNIBLobDW/pQJmNlwj6OzA4Ul/ZpqvLzoV.O.l/'
set system login user vyos authentication plaintext-password ''
set system name-server '1.1.1.1'
set system name-server '8.8.8.8'
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system syslog global facility all level 'info'
set system syslog global facility protocols level 'debug'
set system time-zone 'America/Montreal'
set traffic-policy shaper DOWNLOAD bandwidth '15mbit'
set traffic-policy shaper DOWNLOAD class 12 bandwidth '8mbit'
set traffic-policy shaper DOWNLOAD class 12 ceiling '8mbit'
set traffic-policy shaper DOWNLOAD class 12 match LAN ip destination address '192.168.1.0/24'
set traffic-policy shaper DOWNLOAD default bandwidth '1kbit'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set traffic-policy shaper UPLOAD bandwidth '10mbit'
set traffic-policy shaper UPLOAD class 12 bandwidth '5mbit'
set traffic-policy shaper UPLOAD class 12 ceiling '5mbit'
set traffic-policy shaper UPLOAD class 12 match LAN ip source address '192.168.1.0/24'
set traffic-policy shaper UPLOAD default bandwidth '1kbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
I start to think there’s an issue with VyOS. Does my configuration is supposed to be good?
Dont know if im right but maybe try and apply the policy to eth1 as that is on the same ip range as the one you trying to limit.
Thanks @skoenman but If I’m doing that, I’m not sure it will have the behavior that I want.
I want to give a guaranteed WAN speed to each VLAN but if link is available, a VLAN can take all the available bandwidth.
I’m not sure it will work if I’m applying this policy to the LAN interface instead of the WAN. Maybe I’m wrong too.
I see what you saying …Can anybody comment on how to get policy on certail vlan it doesnt seem like it shows under interfaces???
In the last example that I gave, I didn’t add VLAN. I just wanted to test with LAN only. That’s why there’s no VLAN under show interfaces.
As far as I know, we have a problem when matching by VLAN and this command does not work. We are investigating it.
In the case you can verify it works for you, please let us know your version and configuration.
I confirm that the configuration below works for PPPoE interface with version VyOS 1.3-rolling-202009220118 but it doesn’t for ethernet interface.
set traffic-policy shaper UPLOAD bandwidth '500mbit'
set traffic-policy shaper UPLOAD class 10 bandwidth '50mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '61mbit'
set traffic-policy shaper UPLOAD class 10 match VLAN10 interface eth4.10
set traffic-policy shaper UPLOAD default bandwidth '400mbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
set interfaces pppoe pppoe0 traffic-policy out 'UPLOAD'
@fegauthier Thank you. It’d be very useful if you could please show the rest of the configuration.
You can hide private data by using
show configuration commands | strip-private
This is my whole configuration
set firewall all-ping 'enable'
set firewall broadcast-ping 'disable'
set firewall config-trap 'disable'
set firewall ipv6-receive-redirects 'disable'
set firewall ipv6-src-route 'disable'
set firewall ip-src-route 'disable'
set firewall log-martians 'enable'
set firewall name IPTV_IN default-action 'drop'
set firewall name IPTV_IN description 'IPTV To Lan'
set firewall name IPTV_IN rule 5 action 'accept'
set firewall name IPTV_IN rule 5 description 'Accept established'
set firewall name IPTV_IN rule 5 log 'disable'
set firewall name IPTV_IN rule 5 protocol 'all'
set firewall name IPTV_IN rule 5 state established 'enable'
set firewall name IPTV_IN rule 5 state related 'enable'
set firewall name IPTV_IN rule 10 action 'accept'
set firewall name IPTV_IN rule 10 description 'Allow IGMP'
set firewall name IPTV_IN rule 10 log 'disable'
set firewall name IPTV_IN rule 10 protocol 'igmp'
set firewall name IPTV_IN rule 20 action 'accept'
set firewall name IPTV_IN rule 20 description 'Allow IPTV-Bell'
set firewall name IPTV_IN rule 20 log 'disable'
set firewall name IPTV_IN rule 20 protocol 'udp'
set firewall name IPTV_IN rule 30 action 'drop'
set firewall name IPTV_IN rule 30 description 'Drop invalid'
set firewall name IPTV_IN rule 30 log 'disable'
set firewall name IPTV_IN rule 30 protocol 'all'
set firewall name IPTV_IN rule 30 state invalid 'enable'
set firewall name IPTV_LOCAL default-action 'drop'
set firewall name IPTV_LOCAL rule 5 action 'accept'
set firewall name IPTV_LOCAL rule 5 description 'Accept established'
set firewall name IPTV_LOCAL rule 5 log 'disable'
set firewall name IPTV_LOCAL rule 5 protocol 'all'
set firewall name IPTV_LOCAL rule 5 source
set firewall name IPTV_LOCAL rule 5 state established 'enable'
set firewall name IPTV_LOCAL rule 5 state related 'enable'
set firewall name IPTV_LOCAL rule 10 action 'accept'
set firewall name IPTV_LOCAL rule 10 description 'Allow IPTV-UDP'
set firewall name IPTV_LOCAL rule 10 log 'disable'
set firewall name IPTV_LOCAL rule 10 protocol 'udp'
set firewall name IPTV_LOCAL rule 20 action 'accept'
set firewall name IPTV_LOCAL rule 20 description 'Allow IGMP'
set firewall name IPTV_LOCAL rule 20 log 'disable'
set firewall name IPTV_LOCAL rule 20 protocol 'igmp'
set firewall name IPTV_LOCAL rule 30 action 'accept'
set firewall name IPTV_LOCAL rule 30 description 'Allow ICMP'
set firewall name IPTV_LOCAL rule 30 log 'disable'
set firewall name IPTV_LOCAL rule 30 protocol 'icmp'
set firewall name IPTV_LOCAL rule 60 action 'drop'
set firewall name IPTV_LOCAL rule 60 description 'Drop invalid'
set firewall name IPTV_LOCAL rule 60 log 'disable'
set firewall name IPTV_LOCAL rule 60 protocol 'all'
set firewall name IPTV_LOCAL rule 60 state invalid 'enable'
set firewall name WAN_IN default-action 'drop'
set firewall name WAN_IN rule 10 action 'accept'
set firewall name WAN_IN rule 10 state established 'enable'
set firewall name WAN_IN rule 10 state related 'enable'
set firewall name WAN_IN rule 11 action 'accept'
set firewall name WAN_IN rule 11 description 'Allow HTTPS'
set firewall name WAN_IN rule 11 destination address '172.16.12.5'
set firewall name WAN_IN rule 11 destination port '443'
set firewall name WAN_IN rule 11 log 'disable'
set firewall name WAN_IN rule 11 protocol 'tcp'
set firewall name WAN_IN rule 11 state new 'enable'
set firewall name WAN_LOCAL default-action 'drop'
set firewall name WAN_LOCAL rule 10 action 'accept'
set firewall name WAN_LOCAL rule 10 state established 'enable'
set firewall name WAN_LOCAL rule 10 state related 'enable'
set firewall name WAN_LOCAL rule 20 action 'accept'
set firewall name WAN_LOCAL rule 20 icmp type-name 'echo-request'
set firewall name WAN_LOCAL rule 20 protocol 'icmp'
set firewall name WAN_LOCAL rule 20 state new 'enable'
set firewall name WAN_LOCAL rule 30 action 'drop'
set firewall name WAN_LOCAL rule 30 destination port '22'
set firewall name WAN_LOCAL rule 30 protocol 'tcp'
set firewall name WAN_LOCAL rule 30 recent count '4'
set firewall name WAN_LOCAL rule 30 recent time '60'
set firewall name WAN_LOCAL rule 30 state new 'enable'
set firewall name WAN_LOCAL rule 31 action 'accept'
set firewall name WAN_LOCAL rule 31 destination port '22'
set firewall name WAN_LOCAL rule 31 protocol 'tcp'
set firewall name WAN_LOCAL rule 31 state new 'enable'
set firewall name WAN_LOCAL rule 32 action 'accept'
set firewall name WAN_LOCAL rule 32 destination port '443'
set firewall name WAN_LOCAL rule 32 protocol 'tcp'
set firewall name WAN_LOCAL rule 32 state new 'enable'
set firewall name WAN_LOCAL rule 33 action 'accept'
set firewall name WAN_LOCAL rule 33 destination port '1195'
set firewall name WAN_LOCAL rule 33 protocol 'udp'
set firewall name WAN_LOCAL rule 33 state new 'enable'
set firewall receive-redirects 'disable'
set firewall send-redirects 'enable'
set firewall source-validation 'disable'
set firewall syn-cookies 'enable'
set firewall twa-hazards-protection 'disable'
set interfaces bridge br0 address '172.16.10.1/24'
set interfaces bridge br0 description 'BRIDGE_LAN'
set interfaces bridge br0 member interface eth0
set interfaces bridge br0 member interface eth2
set interfaces ethernet eth0 hw-id 'f4:e9:d4:84:52:50'
set interfaces ethernet eth1 hw-id 'f4:e9:d4:84:52:52'
set interfaces ethernet eth1 mtu '1508'
set interfaces ethernet eth1 vif 35 description 'BELL_INTERNET_VLAN'
set interfaces ethernet eth1 vif 35 mtu '1508'
set interfaces ethernet eth1 vif 36 address 'dhcp'
set interfaces ethernet eth1 vif 36 description 'BELL_IPTV'
set interfaces ethernet eth1 vif 36 firewall in name 'IPTV_IN'
set interfaces ethernet eth1 vif 36 firewall local name 'IPTV_LOCAL'
set interfaces ethernet eth2 hw-id 'b4:2e:99:84:b6:21'
set interfaces ethernet eth3 address '192.168.5.1/24'
set interfaces ethernet eth3 description 'IPTV_LAN'
set interfaces ethernet eth3 hw-id '68:1c:a2:13:48:c5'
set interfaces ethernet eth4 address '172.16.11.1/24'
set interfaces ethernet eth4 description 'WLAN'
set interfaces ethernet eth4 hw-id '68:1c:a2:13:48:c6'
set interfaces ethernet eth4 vif 10 address '192.168.10.1/24'
set interfaces ethernet eth4 vif 10 description 'VLAN10'
set interfaces ethernet eth5 address '172.16.12.1/24'
set interfaces ethernet eth5 description 'SERVER'
set interfaces ethernet eth5 hw-id '68:1c:a2:13:48:c7'
set interfaces ethernet eth6 hw-id '68:1c:a2:13:48:c8'
set interfaces input ifb3 traffic-policy out 'DOWNLOAD'
set interfaces loopback lo
set interfaces pppoe pppoe0 authentication password '****'
set interfaces pppoe pppoe0 authentication user '****'
set interfaces pppoe pppoe0 default-route 'force'
set interfaces pppoe pppoe0 firewall in name 'WAN_IN'
set interfaces pppoe pppoe0 firewall local name 'WAN_LOCAL'
set interfaces pppoe pppoe0 mtu '1500'
set interfaces pppoe pppoe0 redirect 'ifb3'
set interfaces pppoe pppoe0 source-interface 'eth1.35'
set interfaces pppoe pppoe0 traffic-policy out 'UPLOAD'
set interfaces wireguard wg0 address '10.66.58.44/32'
set interfaces wireguard wg0 description 'Mullvad'
set interfaces wireguard wg0 peer wg-peer address '89.36.78.162'
set interfaces wireguard wg0 peer wg-peer allowed-ips '0.0.0.0/0'
set interfaces wireguard wg0 peer wg-peer port '51820'
set interfaces wireguard wg0 peer wg-peer pubkey '****'
set interfaces wireguard wg0 port '1195'
set interfaces wireguard wg0 private-key 'default'
set interfaces wireguard wg1 address '10.69.115.243/32'
set interfaces wireguard wg1 description 'Mullvad2'
set interfaces wireguard wg1 disable
set interfaces wireguard wg1 peer wg-peer2 address '89.36.78.178'
set interfaces wireguard wg1 peer wg-peer2 allowed-ips '0.0.0.0/0'
set interfaces wireguard wg1 peer wg-peer2 port '51819'
set interfaces wireguard wg1 peer wg-peer2 pubkey '****'
set interfaces wireguard wg1 private-key 'wg1'
set nat destination rule 10 description 'Port Forward HTTPS'
set nat destination rule 10 destination port '443'
set nat destination rule 10 inbound-interface 'pppoe0'
set nat destination rule 10 protocol 'tcp'
set nat destination rule 10 translation address '172.16.12.5'
set nat source rule 99 outbound-interface 'wg0'
set nat source rule 99 source address '192.168.10.0/24'
set nat source rule 99 translation address 'masquerade'
set nat source rule 100 outbound-interface 'pppoe0'
set nat source rule 100 translation address 'masquerade'
set nat source rule 101 description 'Bell IPTV'
set nat source rule 101 destination address '10.0.0.0/8'
set nat source rule 101 outbound-interface 'eth1.36'
set nat source rule 101 protocol 'all'
set nat source rule 101 translation address 'masquerade'
set policy route VPN rule 10 set table '10'
set policy route VPN rule 10 source address '192.168.10.0/24'
set protocols igmp-proxy interface eth1.36 alt-subnet '224.0.0.0/8'
set protocols igmp-proxy interface eth1.36 alt-subnet '10.0.0.0/8'
set protocols igmp-proxy interface eth1.36 role 'upstream'
set protocols igmp-proxy interface eth1.36 threshold '1'
set protocols igmp-proxy interface eth3 alt-subnet '192.168.5.0/24'
set protocols igmp-proxy interface eth3 role 'downstream'
set protocols igmp-proxy interface eth3 threshold '1'
set protocols static interface-route 10.255.1.0/24 next-hop-interface vtun1
set protocols static route 10.0.0.0/8 next-hop 10.247.48.1 distance '1'
set protocols static table 10 interface-route 0.0.0.0/0 next-hop-interface wg0
set service dhcp-server global-parameters 'option option-138 code 138 = ip-address;'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 default-router '192.168.5.1'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 dns-server '207.164.234.129'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 dns-server '207.164.234.193'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 lease '86400'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 range 0 start '192.168.5.10'
set service dhcp-server shared-network-name IPTV_LAN subnet 192.168.5.0/24 range 0 stop '192.168.5.254'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 default-router '172.16.10.1'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 lease '86400'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 range 0 start '172.16.10.10'
set service dhcp-server shared-network-name LAN subnet 172.16.10.0/24 range 0 stop '172.16.10.254'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 default-router '172.16.12.1'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 lease '86400'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 range 0 start '172.16.12.10'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 range 0 stop '172.16.12.254'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping GloboMine ip-address '172.16.12.4'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping GloboMine mac-address '32:08:c6:1b:fe:4e'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping LaPetiteReplique ip-address '172.16.12.3'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping LaPetiteReplique mac-address '36:38:9e:c2:6c:34'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping Proxmox ip-address '172.16.12.10'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping Proxmox mac-address 'e2:f7:fa:62:2c:6c'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping ReverseProxy ip-address '172.16.12.5'
set service dhcp-server shared-network-name SERVER subnet 172.16.12.0/24 static-mapping ReverseProxy mac-address '66:16:fc:66:06:c7'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 default-router '192.168.10.1'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 lease '86400'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 range 0 start '192.168.10.10'
set service dhcp-server shared-network-name VLAN10 subnet 192.168.10.0/24 range 0 stop '192.168.10.254'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 default-router '172.16.11.1'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 lease '86400'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 range 0 start '172.16.11.10'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 range 0 stop '172.16.11.254'
set service dhcp-server shared-network-name WLAN subnet 172.16.11.0/24 subnet-parameters 'option option-138 ****;'
set service dns dynamic interface pppoe0 service cloudflare host-name '****'
set service dns dynamic interface pppoe0 service cloudflare login '****'
set service dns dynamic interface pppoe0 service cloudflare password '****'
set service dns dynamic interface pppoe0 service cloudflare protocol 'cloudflare'
set service dns dynamic interface pppoe0 service cloudflare zone 'globomine.ca'
set service dns dynamic interface pppoe0 use-web skip 'Current IP Address: '
set service dns dynamic interface pppoe0 use-web url 'http://checkip.dyndns.com/'
set service ssh port '22'
set system config-management commit-revisions '100'
set system console device ttyS0 speed '115200'
set system host-name 'vyos'
set system login user vyos authentication encrypted-password '$6$Kogw7..UJ87oh$slOo4Uln8isHHn/McmRerZN5Upq7xQbzopqw5TvTTlyMnmM3Cw6QwWFcwJiUDk0x3tVdt/UTc9dprNmp91BYU/'
set system login user vyos authentication plaintext-password ''
set system name-server '1.1.1.1'
set system name-server '8.8.8.8'
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system syslog global facility all level 'info'
set system syslog global facility protocols level 'debug'
set traffic-policy shaper DOWNLOAD bandwidth '600mbit'
set traffic-policy shaper DOWNLOAD class 10 bandwidth '20mbit'
set traffic-policy shaper DOWNLOAD class 10 ceiling '60mbit'
set traffic-policy shaper DOWNLOAD class 10 match VLAN10 ip destination address '192.168.10.0/24'
set traffic-policy shaper DOWNLOAD default bandwidth '1mbit'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set traffic-policy shaper UPLOAD bandwidth '500mbit'
set traffic-policy shaper UPLOAD class 10 bandwidth '50mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '61mbit'
set traffic-policy shaper UPLOAD class 10 match VLAN10 interface 'eth4.10'
set traffic-policy shaper UPLOAD default bandwidth '400mbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
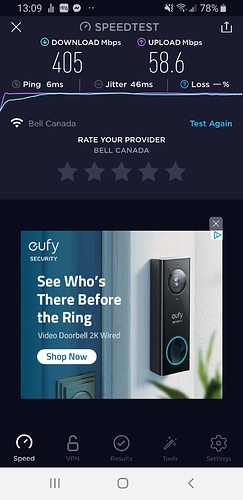
This is the speedtest related to the above config
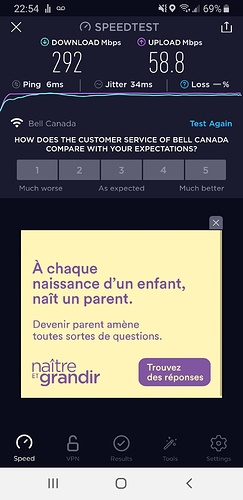
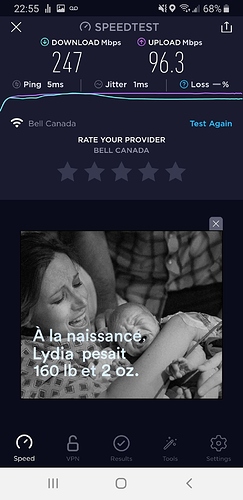
After that I commited these two lines
set traffic-policy shaper UPLOAD class 10 bandwidth '90mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '100mbit'
This is my new speedtest
It doesn’t work with ethernet interface. I tried the samething with my Ethernet WAN and the traffic is not shaping. If I use ip source ‘192.168.10.0/24’, it doesn’t work.
It’s not working for download because redirect doesn’t work with PPPoE…
Do you know what happen? Does the traffic shaping is supposed to work?
Interesting. Before answering your questions, let me please find out what is happening.
How is traffic from that client getting into interface eth4.10?
Is that traffic tagged or untagged?
The wireless access point SSID tag the VLAN
Regarding your question here:
When looking at the numbers, it looks like you are not being matched by class 12, but by default. I guess the first thing I would do is to check the IP address of that client is within 192.168.1.0/24.
Would you please show me the outcome of
tcpdump -eni eth4 -c30
Executing it while you are doing that speed test from your Wi-Fi client.