Thanks for sharing by Kalyan
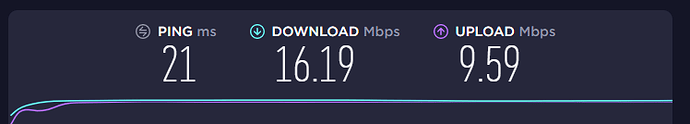
This is the result during the Upload speedtest from my wifi client
11:35:06.149138 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53198: Flags [.], ack 3188627363, win 4887, options [nop,nop,TS val 2118932517 ecr 6914963], length 0
11:35:06.149165 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53192: Flags [.], ack 2542647289, win 4752, options [nop,nop,TS val 2118932517 ecr 6914963], length 0
11:35:06.149192 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53196: Flags [.], ack 1437050607, win 7059, options [nop,nop,TS val 2118932517 ecr 6914963], length 0
11:35:06.149677 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 34753:36201, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149711 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 36201:37649, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149730 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53198 > 184.150.167.222.8080: Flags [.], seq 39097:40545, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149748 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53198 > 184.150.167.222.8080: Flags [.], seq 40545:41993, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149766 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 2973306264:2973307712, ack 3411217281, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149794 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 1448:2896, ack 1, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149817 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53192 > 184.150.167.222.8080: Flags [.], seq 44889:46337, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149835 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53192 > 184.150.167.222.8080: Flags [.], seq 46337:47785, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932510], length 1448: HTTP
11:35:06.149853 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 37649:39097, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932511], length 1448: HTTP
11:35:06.149871 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 39097:40545, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.149931 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53200: Flags [.], ack 4294918064, win 2953, options [nop,nop,TS val 2118932517 ecr 6914962], length 0
11:35:06.149950 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53198: Flags [.], ack 2897, win 4887, options [nop,nop,TS val 2118932517 ecr 6914963], length 0
11:35:06.149968 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53192: Flags [.], ack 2897, win 4752, options [nop,nop,TS val 2118932517 ecr 6914963], length 0
11:35:06.150790 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53196: Flags [.], ack 2897, win 7059, options [nop,nop,TS val 2118932518 ecr 6914963], length 0
11:35:06.150815 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53200: Flags [.], ack 4294920960, win 2953, options [nop,nop,TS val 2118932518 ecr 6914962], length 0
11:35:06.150839 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53198: Flags [.], ack 5793, win 4887, options [nop,nop,TS val 2118932518 ecr 6914963], length 0
11:35:06.150863 68:1c:a2:13:48:c6 > e8:e8:b7:8d:a8:26, ethertype 802.1Q (0x8100), length 70: vlan 10, p 0, ethertype IPv4, 184.150.167.222.8080 > 192.168.10.10.53192: Flags [.], ack 5793, win 4752, options [nop,nop,TS val 2118932518 ecr 6914963], length 0
11:35:06.150990 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 2896:4344, ack 1, win 343, options [nop,nop,TS val 6914964 ecr 2118932513], length 1448: HTTP
11:35:06.151019 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53192 > 184.150.167.222.8080: Flags [.], seq 47785:49233, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151039 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 4344:5792, ack 1, win 343, options [nop,nop,TS val 6914964 ecr 2118932513], length 1448: HTTP
11:35:06.151057 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53198 > 184.150.167.222.8080: Flags [.], seq 41993:43441, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151075 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53192 > 184.150.167.222.8080: Flags [.], seq 49233:50681, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151093 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53198 > 184.150.167.222.8080: Flags [.], seq 43441:44889, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151121 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 5792:7240, ack 1, win 343, options [nop,nop,TS val 6914964 ecr 2118932513], length 1448: HTTP
11:35:06.151144 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 40545:41993, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151162 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53196 > 184.150.167.222.8080: Flags [.], seq 41993:43441, ack 0, win 343, options [nop,nop,TS val 6914964 ecr 2118932512], length 1448: HTTP
11:35:06.151179 e8:e8:b7:8d:a8:26 > 68:1c:a2:13:48:c6, ethertype 802.1Q (0x8100), length 1518: vlan 10, p 0, ethertype IPv4, 192.168.10.10.53200 > 184.150.167.222.8080: Flags [.], seq 7240:8688, ack 1, win 343, options [nop,nop,TS val 6914964 ecr 2118932513], length 1448: HTTPThank you.
There seems to be a bug. VLAN traffic can be used as matching criteria when the policy is applied to a client PPPoE interface. It fails when applying the policy to an Ethernet interface. I reported the bug.
https://phabricator.vyos.net/T2942
Yes. I’m afraid you are facing two bugs!
Please subscribe to both Phabricator tasks to be notified when they are fixed.
Thanks!
Even with ip source ‘192.168.10.0/24’, it doesn’t match. For ethernet and PPPoE. Is this a bug here too?
As far as I know it should work, but we would need more information. Please send the config and a diagram (or explanation of your setup) and explain what the problem is now.
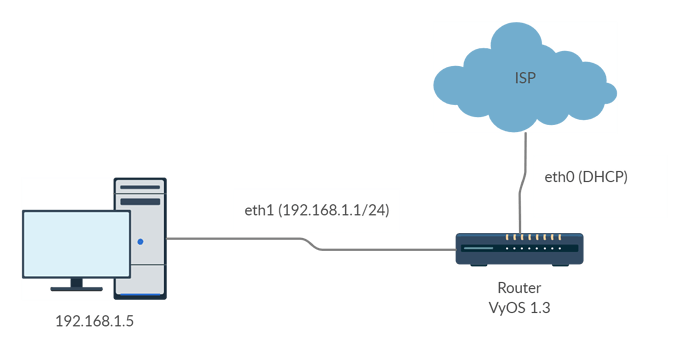
This is the schema of my DHCP WAN and Router
This is my config
set firewall all-ping 'enable'
set firewall broadcast-ping 'disable'
set firewall config-trap 'disable'
set firewall ipv6-receive-redirects 'disable'
set firewall ipv6-src-route 'disable'
set firewall ip-src-route 'disable'
set firewall log-martians 'enable'
set firewall name LAN_IN default-action 'accept'
set firewall name LAN_IN rule 10 action 'drop'
set firewall name LAN_IN rule 10 destination address '192.168.0.0/16'
set firewall name LAN_IN rule 10 source address '192.168.0.0/16'
set firewall name WAN_IN default-action 'drop'
set firewall name WAN_IN rule 10 action 'accept'
set firewall name WAN_IN rule 10 state established 'enable'
set firewall name WAN_IN rule 10 state related 'enable'
set firewall name WAN_LOCAL default-action 'drop'
set firewall name WAN_LOCAL rule 10 action 'accept'
set firewall name WAN_LOCAL rule 10 state established 'enable'
set firewall name WAN_LOCAL rule 10 state related 'enable'
set firewall name WAN_LOCAL rule 20 action 'accept'
set firewall name WAN_LOCAL rule 20 icmp type-name 'echo-request'
set firewall name WAN_LOCAL rule 20 protocol 'icmp'
set firewall name WAN_LOCAL rule 20 state new 'enable'
set firewall name WAN_LOCAL rule 30 action 'drop'
set firewall name WAN_LOCAL rule 30 destination port '22'
set firewall name WAN_LOCAL rule 30 protocol 'tcp'
set firewall name WAN_LOCAL rule 30 recent count '4'
set firewall name WAN_LOCAL rule 30 recent time '60'
set firewall name WAN_LOCAL rule 30 state new 'enable'
set firewall name WAN_LOCAL rule 31 action 'accept'
set firewall name WAN_LOCAL rule 31 destination port '22'
set firewall name WAN_LOCAL rule 31 protocol 'tcp'
set firewall name WAN_LOCAL rule 31 state new 'enable'
set firewall receive-redirects 'disable'
set firewall send-redirects 'enable'
set firewall source-validation 'disable'
set firewall syn-cookies 'enable'
set firewall twa-hazards-protection 'disable'
set interfaces ethernet eth0 address 'dhcp'
set interfaces ethernet eth0 description 'WAN'
set interfaces ethernet eth0 firewall in name 'WAN_IN'
set interfaces ethernet eth0 firewall local name 'WAN_LOCAL'
set interfaces ethernet eth0 hw-id '00:a0:c9:69:80:7b'
set interfaces ethernet eth0 traffic-policy out 'UPLOAD'
set interfaces ethernet eth1 address '192.168.1.1/24'
set interfaces ethernet eth1 description 'LAN'
set interfaces ethernet eth1 firewall in name 'LAN_IN'
set interfaces ethernet eth1 hw-id '00:a0:c9:69:80:7c'
set interfaces ethernet eth2 hw-id '00:a0:c9:69:80:7d'
set interfaces ethernet eth3 hw-id '00:a0:c9:69:80:7e'
set interfaces loopback lo
set nat source rule 100 outbound-interface 'eth0'
set nat source rule 100 translation address 'masquerade'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 default-router '192.168.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 lease '86400'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range 0 start '192.168.1.10'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range 0 stop '192.168.1.254'
set service ssh port '22'
set system config-management commit-revisions '100'
set system console device ttyS0 speed '115200'
set system host-name 'vyos'
set system login user vyos authentication encrypted-password '$6$9RjedjecvB9$GhTyfAOg2RRc77gPFa64SOZqE714md1cXh3L9w6HIiVagqjuNIBLobDW/pQJmNlwj6OzA4Ul/ZpqvLzoV.O.l/'
set system login user vyos authentication plaintext-password ''
set system name-server '1.1.1.1'
set system name-server '8.8.8.8'
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system syslog global facility all level 'info'
set system syslog global facility protocols level 'debug'
set system time-zone 'America/Montreal'
set traffic-policy shaper UPLOAD bandwidth '10mbit'
set traffic-policy shaper UPLOAD class 10 bandwidth '5mbit'
set traffic-policy shaper UPLOAD class 10 ceiling '5mbit'
set traffic-policy shaper UPLOAD class 10 match LAN ip source address '192.168.1.0/24'
set traffic-policy shaper UPLOAD default bandwidth '1kbit'
set traffic-policy shaper UPLOAD default ceiling '100%'
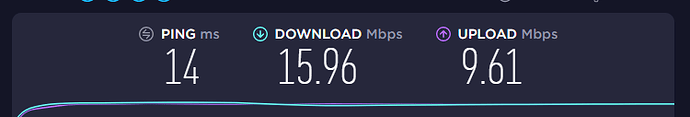
This is my speedtest from the PC 192.168.1.5
With ip source, no shaping is done…
Weird!
Can you please modify class 10 ceiling value and do the test again?
I would like to know if it is somehow inaccurately working.
I changed the ceiling value for ‘6mbit’
set traffic-policy shaper UPLOAD class 10 ceiling '6mbit'
Still no shaping…
Is there any chance you can try any of the following tests? (Or even better if you can try both)
- Test it without NAT.
- Keep your NAT but test it with real traffic. I mean upload a real file, and check the speed without using any speed-test tool that creates artificial traffic.
I’m not sure, I wonder if that speed-test tool, when used with NAT could create some problem, like leaky NAT.
How can I disable nat? Because if I remove the masquerade on the WAN, I will not have access to internet.
I tried to set static route to route traffic from LAN to WAN but it didn’t work
On the first option I mean either testing it from private address to private address, or from public address to public address.
You can also go for the second option.
With option two, nothing is shaped. Upload speed to mega.nz is the same as the speedtest shown me.
Nothing is shape when upload from private address to private address because traffic shaping is applied on the WAN port not the LAN port.
I did a tcpdump and look packets with WireShark.
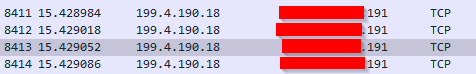
Addresses on eth0 is not 192.168.1.5 but the WAN IP. How traffic shaping translate this? Is this the job of the NAT?
Is it possible that the traffic shaping is done before NAT and the source/destination address is the WAN instead of the LAN client IP? It could explain why it doesn’t match class.
EDIT:
I confirm that traffic shaper is done before NAT and that’s why class are not matched. If I use WAN IP as ip source
The shaper is matching the class. I don’t know if it’s normal that shaper is done before translating address?
Good finding. Yes, that is correct, traffic-policy is applied after NAT. You can use FWMARK to mark your traffic (you can do so through policy-route) and then, in your traffic-policy, use fwmark as the matching criteria. That will solve the problem.
Does the policy needs to be applied to WAN interface or the LAN interface?
I did
set policy route WAN rule 10 set mark '10'
set policy route WAN rule 10 source address '192.168.1.0/24'
I apply the policy to the WAN interface and I change the criteria of the traffic shaper but it doesn’t work.
set traffic-policy shaper UPLOAD class 10 match LAN mark '10'
If I apply the policy to the LAN interface instead of the WAN, It’s working for UPLOAD shaping but I didn’t get DOWNLOAD shaping to work yet
It’s logic for the UPLOAD traffic to mark the traffic before if goes to the WAN interface. But for DOWNLOAD, I don’t think it can work because the traffic came from WAN and after goes to the LAN interface, so it’s not possible to mark this traffic.
Is there another way to get the download shaping working?
Yes, there is a way, but, as far as I know, VyOS CLI does not support it. You can follow this guide.
I have opened a feature request to see if that could be integrated into VyOS CLI. You can subscribe to receive updates.
Cool! Thanks for your help! Do you know how many times it could take before that feature to be implemented? Do we talk about months or year?
Unfortunately I don’t know. I wish it could be done as soon as possible, but I cannot tell when. I can tell you it won’t be forgotten, it will be chased. So, if you are subscribed to the Phabricator task, sooner or later you’ll get some news.
There is also the option of contributing, where everyone is welcome.
I’m trying to get it work from the ArchLinux guide you sent me.
I used this to mark OUTPUT traffic with 3
# Outgoing traffic from 192.168.1.5 is marked with "3"
iptables -t mangle -N QOS
iptables -t mangle -A FORWARD -o eth0 -j QOS
iptables -t mangle -A OUTPUT -o eth0 -j QOS
iptables -t mangle -A QOS -j CONNMARK --restore-mark
iptables -t mangle -A QOS -s 192.168.1.5 -m mark --mark 0 -j MARK --set-mark 3
iptables -t mangle -A QOS -j CONNMARK --save-mark
This is my shaper config
set traffic-policy shaper DOWNLOAD bandwidth '15mbit'
set traffic-policy shaper DOWNLOAD class 10 bandwidth '10mbit'
set traffic-policy shaper DOWNLOAD class 10 burst '15k'
set traffic-policy shaper DOWNLOAD class 10 ceiling '10mbit'
set traffic-policy shaper DOWNLOAD class 10 match LAN mark '3'
set traffic-policy shaper DOWNLOAD class 10 queue-type 'fair-queue'
set traffic-policy shaper DOWNLOAD default bandwidth '1kbit'
set traffic-policy shaper DOWNLOAD default burst '15k'
set traffic-policy shaper DOWNLOAD default ceiling '100%'
set traffic-policy shaper DOWNLOAD default queue-type 'fair-queue'
set interfaces ethernet eth0 redirect 'ifb0'
set interfaces input ifb0 traffic-policy out 'DOWNLOAD'
The traffic doesn’t seems to be mark… Maybe something that I missed? Do you have an idea?