Hello,
I have a Vyos, we tried 1.2.1 then 1.2.8 then 1.3.1, it all happens the same and we dont know why.
We have a vyos with 2 ISPs and 2 VPNs to a Fortigate that also has 2ISP’s and 2 VPNs
To summarize the problem, whenever VPN2 fails, Vyos routes everything, including remote access, to PEER0 of the vpn.
More exactly, if we drop VTI1 from the Fortigate side, after a few seconds we lose connectivity to this box. We connect via the static route, not via the tunnel in any way
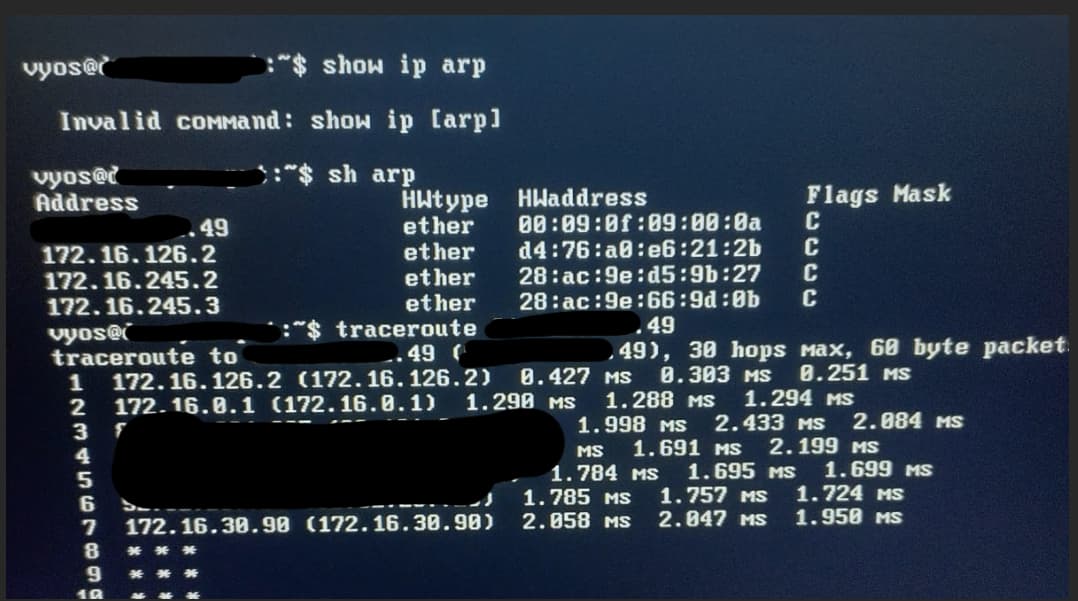
Since it’s virtual, we have a console on it.
The device loses all ARP towards the gateway. It does not respond to PING/SSH, and here’s the catch:
Tracerouting a static route OR the default next-hop shows that the traffic goes via eth4, as in 126.2
The fix is to do “restart vpn” and it suddently works. My sole suspicion is that somehow vyos has a mismatch/routes a 0.0.0.0/0 to 126.2 which is the vpn peer.
Ive checked ip routing and ip ro, the routes are still the same and they are correct
Please assist!
interfaces {
ethernet eth3 {
address xxx.xxx.162.53/28
duplex auto
hw-id xx:xx:xx:xx:xx:65
offload {
gro
gso
sg
tso
}
speed auto
}
ethernet eth4 {
address xxx.xxx.126.1/30
description DF
duplex auto
hw-id xx:xx:xx:xx:xx:91
offload {
gro
gso
sg
tso
}
speed auto
}
ethernet eth5 {
address xxx.xxx.245.1/29
duplex auto
hw-id xx:xx:xx:xx:xx:5b
offload {
gro
gso
sg
tso
}
speed auto
}
loopback lo {
}
vti vti0 {
address xxx.xxx.254.1/30
mtu 1400
}
vti vti1 {
address xxx.xxx.254.5/30
description DF
mtu 1400
}
}
nat {
destination {
rule 100 {
destination {
address xxx.xxx.162.53
port 162
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.2
port 161
}
}
rule 101 {
destination {
address xxx.xxx.162.53
port 163
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.99
port 161
}
}
rule 102 {
destination {
address xxx.xxx.162.53
port 164
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.11
port 161
}
}
rule 103 {
destination {
address xxx.xxx.162.53
port 165
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.12
port 161
}
}
rule 104 {
destination {
address xxx.xxx.162.53
port 166
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.13
port 161
}
}
rule 105 {
destination {
address xxx.xxx.162.53
port 167
}
inbound-interface eth3
protocol udp
translation {
address xxx.xxx.111.14
port 161
}
}
rule 120 {
destination {
address xxx.xxx.162.53
port 3396
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.1.56
port 3389
}
}
rule 121 {
destination {
address xxx.xxx.162.53
port 3395
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.1.201
port 3389
}
}
rule 122 {
destination {
address xxx.xxx.162.53
port 2222
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.1.2
port 22
}
}
rule 123 {
destination {
address xxx.xxx.162.53
port 6789
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.1.200
port 22
}
}
rule 124 {
destination {
address xxx.xxx.162.53
port 6688
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.111.20
port 3389
}
}
rule 125 {
destination {
address xxx.xxx.162.53
port 8888
}
inbound-interface eth3
protocol tcp
translation {
address xxx.xxx.1.200
port 80
}
}
}
}
protocols {
ospf {
area xxx.xxx.0.0 {
network xxx.xxx.254.0/30
network xxx.xxx.254.4/30
network xxx.xxx.245.0/29
}
}
static {
route xxx.xxx.146.175/32 {
next-hop xxx.xxx.162.49 {
}
}
route xxx.xxx.162.17/32 {
next-hop xxx.xxx.162.49 {
}
}
route xxx.xxx.162.18/32 {
next-hop xxx.xxx.162.49 {
}
}
route xxx.xxx.162.24/32 {
next-hop xxx.xxx.162.49 {
}
}
route xxx.xxx.162.27/32 {
next-hop xxx.xxx.162.49 {
}
}
route xxx.xxx.162.54/32 {
next-hop xxx.xxx.254.6 {
}
}
route xxx.xxx.221.0/24 {
next-hop xxx.xxx.254.6 {
}
}
route xxx.xxx.12.119/32 {
next-hop xxx.xxx.254.6 {
}
}
}
}
system {
config-management {
commit-revisions 100
}
conntrack {
modules {
ftp
h323
nfs
pptp
sip
sqlnet
tftp
}
}
console {
device ttyS0 {
speed 9600
}
}
host-name xxxxxx
login {
user xxxxxx {
authentication {
encrypted-password xxxxxx
plaintext-password xxxxxx
}
}
user xxxxxx {
authentication {
encrypted-password xxxxxx
plaintext-password xxxxxx
}
}
}
ntp {
server xxxxx.tld {
}
server xxxxx.tld {
}
server xxxxx.tld {
}
}
syslog {
global {
facility all {
level info
}
facility protocols {
level debug
}
}
}
time-zone UTC
}
vpn {
ipsec {
esp-group fortivpn {
compression disable
lifetime 3600
mode tunnel
pfs enable
proposal 1 {
encryption aes256
hash sha256
}
}
ike-group fortivpn {
close-action none
ikev2-reauth no
key-exchange ikev1
lifetime 3600
proposal 1 {
dh-group 2
encryption aes256
hash sha256
}
}
ipsec-interfaces {
interface eth3
interface eth4
}
site-to-site {
peer xxxxx.tld {
authentication {
mode pre-shared-secret
pre-shared-secret xxxxxx
}
connection-type initiate
default-esp-group fortivpn
ike-group fortivpn
ikev2-reauth inherit
local-address xxx.xxx.162.53
vti {
bind vti0
esp-group fortivpn
}
}
peer xxxxx.tld {
authentication {
mode pre-shared-secret
pre-shared-secret xxxxxx
}
connection-type initiate
default-esp-group fortivpn
ike-group fortivpn
ikev2-reauth inherit
local-address xxx.xxx.126.1
vti {
bind vti1
esp-group fortivpn
}
}
}
}
}