I tested vyos as pppoe server but unfortunately I can’t use it. Because of one problem that is username must be included in logs which are stored on syslog server. This is must for an ISP. I found a solution. Someone, helped and told to rename NAS-Port-Id from radius it worked. But its not stable. Because of this pppoe server becomes unstable and disconnects users. And also stops authentication using radius. Unless either I restart service or restart the router itself. I think this is should be present in vyos builtin. Without logs. There is no purpose of pppoe server on vyos
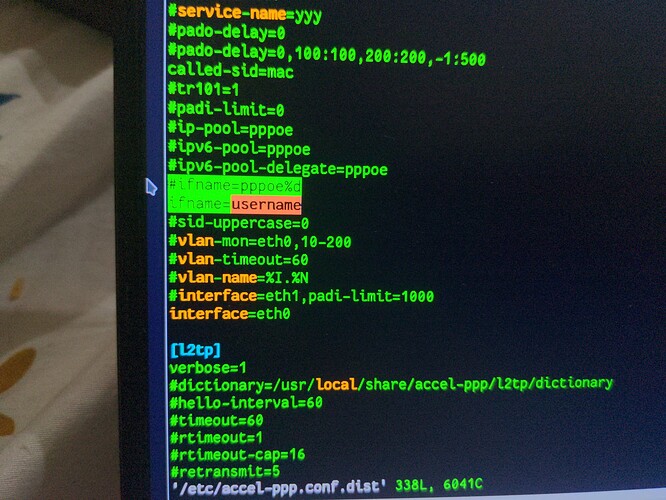
It should be set to pppoe username only. No extra characters should be added. Because accel-ppp has 15 characters limit for interface name
It is not accell-ppp limit but the Linux kernel limit T6223
It is not clear which feature you are suggesting as you said it is not stable. Probably this should be added/fixed for upstream feature/bug
issue is we have to rename interface from radius which is causing sort of issue. And because of which pppoe becomes unstable. I am suggesting to create virtual ppp interface instead of this format “ppp-”. Use username instead of it. So, we don’t have to rename this interface from radius
this is important because in firewall logs virtual interface appears not the username. Username only appears if we rename virtual interface from radius which is causing issues. Major issue is all users are randomly disconnect. In order to resolve the issue either have to restart ppp-accel service or restart the router. Previously, I tested pppoe-server without nas-port-od changing. Means with interface names prefixed with “ppp-” got no issue like this
You should add this request to the upstream, i.e. accel-ppp
That will not work. At best, you’ll end up with 1 user logged in, an interface called “username” and no further logins will be possible. At worst, the daemon will crash.
NAS-Port-Id overrides the mechanism in the configuration file, to force ifname_rename on the session to the RADIUS value, and is subject to the same restrictions (maximum length, only certain characters allowed, etc). Whether it comes from the config file or RADIUS, the string is fed straight to the kernel. It may be an ordinal pattern (the %d part), for an auto-calculated sequence number.
Renaming interfaces like this also a really bad idea, since the namespace is full of special stuff. A user called “lo” is going to really break things.
The normal way of correlating network and session logs is by timestamp and IP address, which should all be recorded by RADIUS. FreeRADIUS & daloRADIUS, for eg, keep all the session and accounting records in an SQL backend. It’s easy to look up who was assigned each IP within a time range. It’s the purpose of RADIUS to expose this data for accounting and reporting, all RADIUS solutions I’m aware of are capable of presenting API or DB access.
If your network logging is raw syslog out of a firewall rule and not something a bit easier to work with, like netflows, it should still include the relevant IP addresses. If the syslog feed is from RADIUS or something else, I’m not sure how the interface name is relevant.
If all you are doing is trying to track data usage and connected time, that information is already available in RADIUS, directly correlated with user sessions and accounts.
If you’re using some crazy tooling which really wants to use interface names in syslog, you might be able to rig a user session to interface name mapping by catching the auth event then asking SNMP on VyOS: the accel-ppp MIBs expose the interface name, user, Uniq-IDs, etc for active sessions.
thanks got it. My aim is only to collect logs