Hi
I am using version 1.4-rolling-202204140217.
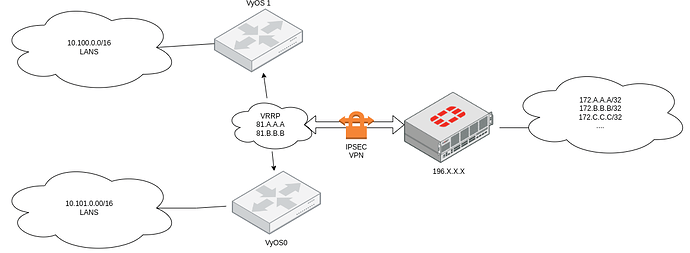
I have a VPN tunnel setup using the VyOS’ 2 VRRP IP addresses (one as host, the other as peer), which requires I SNAT the traffic from the internal subnets behind the VyOS as one of the VRRP IPs.
Unfortunately I am unable to successfully SNAT, and traffic from the internal subnets cannot board the tunnel. I would appreciate some assistance in figuring out what I am doing wrong.
I need to SNAT traffic from 10.100.0.0/16 to 81.B.B.B in order to reach VPN host subnet at the other side 172.24.96.0/20, while 81.A.A.A forms the tunnel.
My configuration is like this:
#run show interfaces
Interface IP Address S/L Description
--------- ---------- --- -----------
eth0 81.C.C.C/27 u/u WAN
81.A.A.A/27
81B.B.B/27
# show nat source
rule 5 {
destination {
address 172.24.96.0/20
}
exclude
outbound-interface eth0
}
rule 10 {
outbound-interface eth0
source {
address 10.100.0.0/16
}
translation {
address 81.B.B.B
}
}
No traffic on the VPN
peer_196-X-X-X_tunnel_0 up 39m7s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
peer_196-X-X-X_tunnel_1 up 40m19s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
peer_196-X-X-X_tunnel_2 up 39m42s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
peer_196-X-X-X_tunnel_3 up 39m6s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
peer_196-X-X-X_tunnel_4 up 38m51s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
peer_196-X-X-X_tunnel_5 up 40m11s 0B/0B 0B/0B 196.X.X.X 196.X.X.X AES_CBC_256/HMAC_SHA1_96
hi
I think we need more information about what type of tunnel do you use? (base-VPN or route-VPN) , also if you have a LAN interface or just one interface(eth0). however, if you are configured well your tunnel, should be able to reach another site of VPN without Nat settings.
fernando.
Apologies.
Its a site to site VPN (I guess based? Not really sure).
My VPN configuration is like this:
set vpn ipsec esp-group esp-s2s compression 'disable'
set vpn ipsec esp-group esp-s2s lifetime '3600'
set vpn ipsec esp-group esp-s2s mode 'tunnel'
set vpn ipsec esp-group esp-s2s pfs 'disable'
set vpn ipsec esp-group esp-s2s proposal 1 encryption 'aes256'
set vpn ipsec esp-group esp-s2s proposal 1 hash 'sha1'
set vpn ipsec ike-group ike-s2s dead-peer-detection action 'clear'
set vpn ipsec ike-group ike-s2s dead-peer-detection interval '30'
set vpn ipsec ike-group ike-s2s dead-peer-detection timeout '90'
set vpn ipsec ike-group ike-s2s ikev2-reauth 'no'
set vpn ipsec ike-group ike-s2s key-exchange 'ikev1'
set vpn ipsec ike-group ike-s2s lifetime '86400'
set vpn ipsec ike-group ike-s2s proposal 1 dh-group '2'
set vpn ipsec ike-group ike-s2s proposal 1 encryption 'aes256'
set vpn ipsec ike-group ike-s2s proposal 1 hash 'sha1'
set vpn ipsec site-to-site peer 196.X.X.X local-address '81.A.A.A'
set vpn ipsec site-to-site peer 196.X.X.X authentication id '81.A.A.A'
set vpn ipsec site-to-site peer 196.X.X.X authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 196.X.X.X authentication pre-shared-secret ''
set vpn ipsec site-to-site peer 196.X.X.X authentication remote-id '196.X.X.X'
set vpn ipsec site-to-site peer 196.X.X.X connection-type 'initiate'
set vpn ipsec site-to-site peer 196.X.X.X ike-group 'ike-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 0 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 0 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 0 remote prefix '172.24.98.155/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 1 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 1 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 1 remote prefix '172.24.98.157/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 2 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 2 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 2 remote prefix '172.24.96.62/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 3 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 3 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 3 remote prefix '172.24.96.64/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 4 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 4 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 4 remote prefix '172.24.104.65/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 5 esp-group 'esp-s2s'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 5 local prefix '81.B.B.B/32'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 5 remote prefix '172.24.106.65/32'
well , there are some points that could cause the problem.
- traffic selectors don’t match with this requirement ( 172.24.96.0/20 - you used all /32)
- 10.100.0.0/16 no present configuration
- exclude nat isn’t necessary
if I understood , you want a translation form 10.100.0.0/16 to 8.1.b.b .it should be something like this :
set nat source rule 10 destination address '172.24.96.0/20'
set nat source rule 10 outbound-interface 'eth0'
set nat source rule 10 source address '10.100.0.0/16'
set nat source rule 10 translation address '8.b.b.b'
and DNAT with the same logic
regards, fernando
Thanks a lot! NAT is working correctly now, but unfortunately, tunnel is still being ignored. Could it be because I am using a subnet for NAT, instead of using the discrete IPs in the VPN configuration?
Even after reducing 172.24.96.0/20 to individual IPs, traffic still isnt onboarding the tunnel. Really stumped.
1 Like
Usually LAN traffic towards the WAN is the target for NAT
And traffic from the local LAN to the remote LAN is the target for IPsec
So in your case I would do something like this:
set vpn ipsec site-to-site peer 196.X.X.X tunnel 1 local prefix '10.100.0.0/16'
set vpn ipsec site-to-site peer 196.X.X.X tunnel 1 remote prefix '172.24.96.0/20'
However, I may have completely misunderstood your task.
Could you draw a little diagram of what you want to achieve?
Certainly, apologies for any misconceptions.
I am trying to setup a VPN between another side (peer IP 196.X.X.X, remote prefix, 172.A.A.A/32, 172.B.B.B/32…) and the VRRP IPs on VyOS (peer 81.A.A.A, local prefix 81.B.B.B).
This means I need to NAT all subnets behind the VyOSes as 81.B.B.B, which I can do, but the traffic is being sent over the internet instead of through the tunnel.
@fernando What do you mean, NAT exclude isn’t necessary?
sNAT rules in topic start look OK to me.
But if some hidden rule already does NAT exclude, rule 10 will never kick in.
The already existing NAT excludes are for other VPN public remote prefixes.
I find that when I do NAT exclude (in a source rule 5, before any others) for this destination, the NAT to convert 10.100.0.0/16 to 81.B.B.B no longer applies.
The problem for me is, why doesnt it onboard the tunnel?
If rule 5 matches, NAT processing stops, and sNAT in rule 10 won’t be hit.
Then packets will not enter the tunnel, as vpn-policy won’t be met. All local/remote policies have 81.B.B.B as source address, but packet still has original LAN source IP
Yes. Also excluding at rule 10 does not help either. Im also not sure I saw the point of the destination nat with the same logic … either I did it wrong or it doesnt make a difference, the source nat works.
Or could not having a working DNAT be why encapsulation isnt happening?
I suppose I could use an IP from each VyOS subnet to make use of the VPN tunnel … would this be easier?
And would VyOS all traffic from ALL subnets behind it to appear as the IPs selected, and encapsulate as needed?
You don’t need dNAT to encapsulate your outgoing packets. dNAT is only needed if you have servers on your end, and the remote end needs to access using the tunnel
Yes, you are right.
I guess I cant get SNAT to work with an external IP local prefix.