Hi Team,
I am running off-path firewall PoC on eve-ng using vyos 1.4.0 epa2. But the pc couldn’t pass through nat on router to access internet node if policy route is enabled.
My topology is as the following:
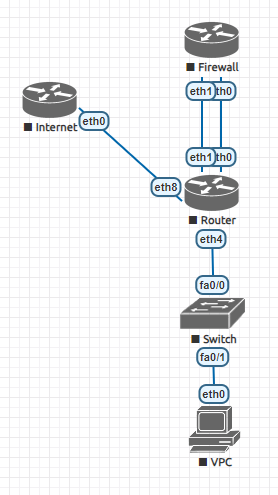
I run vxlan over bgp on router for VPCs in several subnets, which works fine.
And also I enable policy route to redirect cross subnet traffic to firewall as transparent off-path firewall topology.
The core config on router is:
set interfaces ethernet eth0 address 10.1.1.1/24
set interfaces ethernet eth1 address 10.1.2.1/24
set interfaces ethernet eth4 vif 20
set interfaces bridge br20 address '10.64.2.1/24'
set interfaces bridge br20 member interface eth4.20
set interfaces bridge br20 member interface vxlan102
set policy route CROSS_ZONE interface br20
set policy route CROSS_ZONE rule 11 source address 10.64.0.0/11
set policy route CROSS_ZONE rule 11 destination address !10.64.0.0/11
set policy route CROSS_ZONE rule 11 protocol all
set policy route CROSS_ZONE rule 11 set table 10
set protocols static table 10 route 0.0.0.0/0 next-hop 10.1.2.254
set interfaces ethernet eth8 address 1.1.1.2/24
set nat source rule 2000 outbound-interface name eth8
set nat source rule 2000 source address 10.0.0.0/8
set nat source rule 2000 translation address 'masquerade'
set nat source rule 2000 protocol all
set protocols static route 0.0.0.0/0 next-hop 1.1.1.1
I dived into traffic paths and shows that NAT is not performed on eth8.
14:47:35.529249 eth4 P IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
14:47:35.529249 eth4.20 P IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
14:47:35.529249 br20 In IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
14:47:35.529292 eth1 Out IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
14:47:35.531928 eth0 In IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
14:47:35.531947 eth8 Out IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 2040, seq 322, length 64
But when I remove the config:
set policy route CROSS_ZONE interface br20
The NAT works well:
14:46:43.353490 eth4 P IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 54263, seq 271, length 64
14:46:43.353490 eth4.20 P IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 54263, seq 271, length 64
14:46:43.353490 br20 In IP 10.64.2.11 > 2.2.2.2: ICMP echo request, id 54263, seq 271, length 64
14:46:43.353533 eth8 Out IP 1.1.1.2 > 2.2.2.2: ICMP echo request, id 54263, seq 271, length 64
It looks like the policy route breaks the NAT.
Could you please help on this issue?