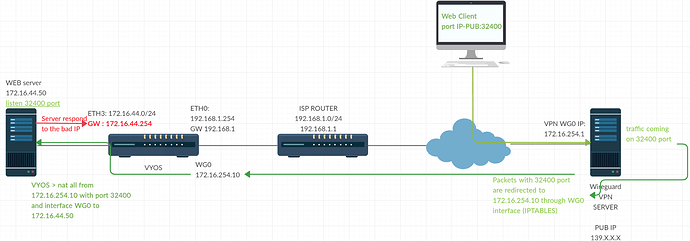
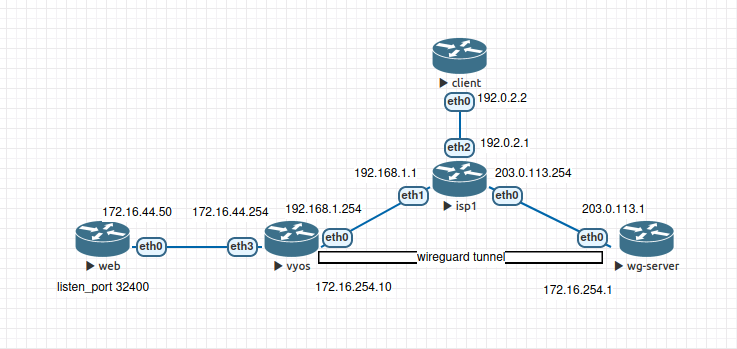
Hello all, I have a little problem, i have setup a VyOS server with a wireguard VPN on a VPS.
I have a web server behind the VyOS with 32400 port I would like redirect all packets with 32400 port coming from my VPS to the web server, on the VPS (Green arrow on my diagram) I have make a IPTABLES rules, it’s ok for this part.
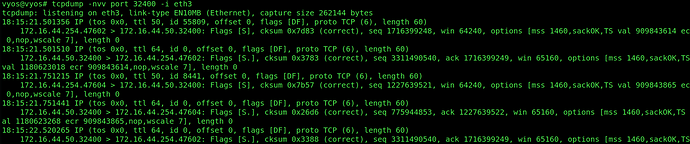
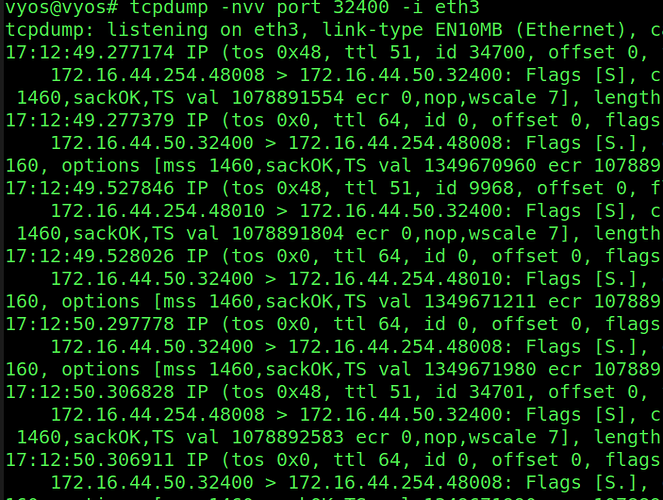
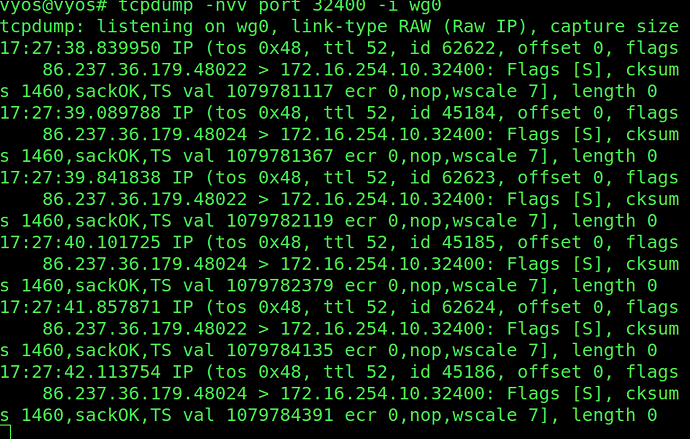
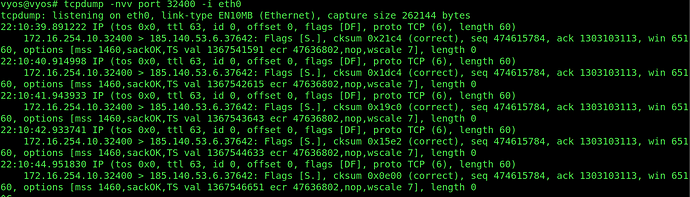
On the VyOS I’ve try to nat 32400 port from WG0 interface and with ip 172.16.254.10 to the 172.16.44.50(web server) I think it’s ok because I see the packets (with tcpdump) going to this IP but the server respond to his gateway: 172.16.44.254
I don’t know how to force to respond at the 172.16.254.10, I have try lot of nat configuration but nothing to work.
thanks for your help, my config (without nat rules):
set interfaces ethernet eth0 address '192.168.1.254/24'
set interfaces ethernet eth0 description 'WAN'
set interfaces ethernet eth3 address '172.16.44.254/24'
set interfaces ethernet eth3 policy route 'PBR3-1'
set interfaces loopback lo
set interfaces wireguard wg0 address '172.16.254.10/32'
set interfaces wireguard wg0 peer SRV address '139.X.X.X'
set interfaces wireguard wg0 peer SRV allowed-ips '0.0.0.0/0'
set interfaces wireguard wg0 peer SRV persistent-keepalive '25'
set interfaces wireguard wg0 peer SRV port '64216'
set interfaces wireguard wg0 peer SRV preshared-key 'XXXXXXXXX'
set interfaces wireguard wg0 peer SRV pubkey 'XXXXXXXXX'
set nat source rule 300 outbound-interface 'wg0'
set nat source rule 300 source address '172.16.44.0/24'
set nat source rule 300 translation address 'masquerade'
set nat source rule 350 outbound-interface 'eth3'
set nat source rule 350 translation address 'masquerade'
set nat source rule 999 outbound-interface 'eth0'
set nat source rule 999 translation address 'masquerade'
set policy route PBR3-1 rule 10 destination address '!172.16.0.0/16'
set policy route PBR3-1 rule 10 set table '100'
set policy route PBR3-1 rule 10 source address '172.16.44.0/24'
set protocols static interface-route 172.16.254.0/24 next-hop-interface wg0
set protocols static interface-route 192.168.1.1/32 next-hop-interface eth0
set protocols static route 0.0.0.0/0 next-hop 192.168.1.1
set protocols static table 100 route 0.0.0.0/0 next-hop 172.16.254.1 next-hop-interface 'wg0'
set service dhcp-server shared-network-name ETH-VM authoritative
set service dhcp-server shared-network-name ETH-VM subnet 172.16.44.0/24 default-router '172.16.44.254'
set service dhcp-server shared-network-name ETH-VM subnet 172.16.44.0/24 dns-server '8.8.8.8'
set service dhcp-server shared-network-name ETH-VM subnet 172.16.44.0/24 lease '86400'
set service dhcp-server shared-network-name ETH-VM subnet 172.16.44.0/24 range 3 start '172.16.44.1'
set service dhcp-server shared-network-name ETH-VM subnet 172.16.44.0/24 range 3 stop '172.16.44.250'
set service ssh listen-address '192.168.1.254'
set service ssh port '22'
set system name-server '8.8.8.8'
set system name-server '8.8.4.4'