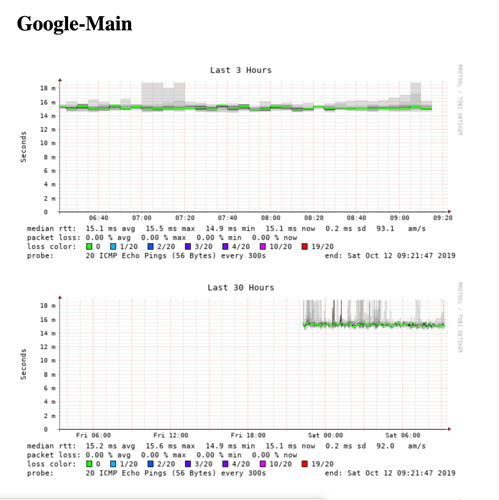
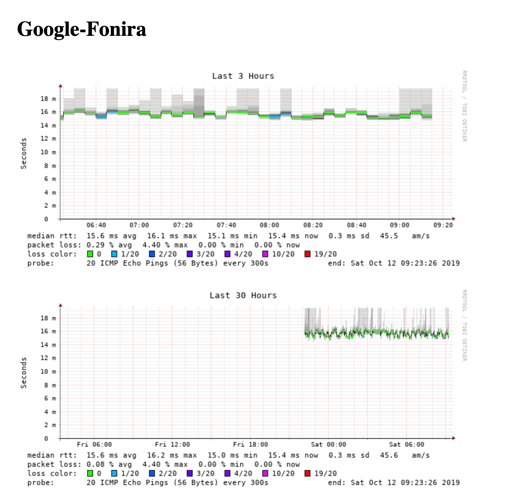
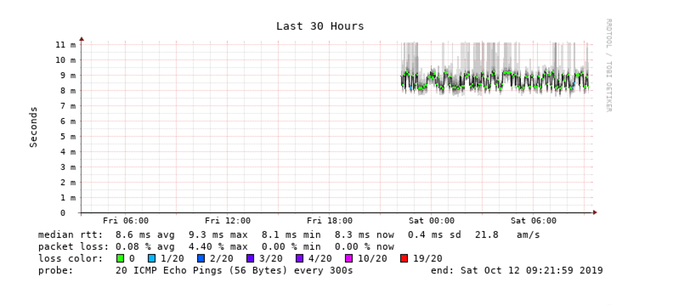
Sorry for no answering , but my account was disabled
@s.lorente .
i have 3 routing Settings
One for PPPOE0 wan-loadbalance Test to IP 8.8.4.4
second for PPPOE1 wan-loadbalance Test to 1.1.1.1
And 0.0.0.0/0 with distance interface-pppoe0 distance "1!
if you say me how i can upload my config file.
Alll three of them are without packet loss during the hole time .
i have also make an video because its very difficult to explain this issue.
But you can understand it like this:
"I browser google , news.google.at or lteforum.at.
One time it works perfectly a second or third time it could run in an timeout ( But ping works perfectly)
If its not working you have to refresh the browser 1 or 2 times after that it works.
This extremly sounds like dns problem but i have also tried to configure manuel 8.8.8.8 in my NIC… this “works” the same way.
vyos@vyos:~$ show interfaces detail
eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:b9:42:d7:30 brd ff:ff:ff:ff:ff:ff
inet 172.16.0.254/24 brd 172.16.0.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20d:b9ff:fe42:d730/64 scope link
valid_lft forever preferred_lft forever
RX: bytes packets errors dropped overrun mcast
2773705255 5475541 0 10 0 38729
TX: bytes packets errors dropped carrier collisions
12137073778 9934802 0 0 0 0
eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:b9:42:d7:31 brd ff:ff:ff:ff:ff:ff
inet6 fe80::20d:b9ff:fe42:d731/64 scope link
valid_lft forever preferred_lft forever
Description: BONDING
RX: bytes packets errors dropped overrun mcast
6855096095 5476074 0 71426 0 36064
TX: bytes packets errors dropped carrier collisions
1435392951 2901608 0 0 0 0
eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:b9:42:d7:32 brd ff:ff:ff:ff:ff:ff
inet6 fe80::20d:b9ff:fe42:d732/64 scope link
valid_lft forever preferred_lft forever
Description: A1
RX: bytes packets errors dropped overrun mcast
5378322070 4726477 0 0 0 35931
TX: bytes packets errors dropped carrier collisions
1347244533 2336822 0 0 0 0
lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
RX: bytes packets errors dropped overrun mcast
2876 26 0 0 0 0
TX: bytes packets errors dropped carrier collisions
2876 26 0 0 0 0
pppoe0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc pfifo_fast state UNKNOWN group default qlen 3
link/ppp
inet 178.251.70.1 peer 100.64.96.1/32 scope global pppoe0
valid_lft forever preferred_lft forever
RX: bytes packets errors dropped overrun mcast
5461545286 4267525 0 0 0 0
TX: bytes packets errors dropped carrier collisions
938294992 2158399 0 0 0 0
pppoe1: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc pfifo_fast state UNKNOWN group default qlen 3
link/ppp
inet 193.81.39.72 peer 91.115.231.254/32 scope global pppoe1
valid_lft forever preferred_lft forever
RX: bytes packets errors dropped overrun mcast
4491551941 4009405 0 0 0 0
TX: bytes packets errors dropped carrier collisions
1103626392 1959577 0 0 0 0
thanks