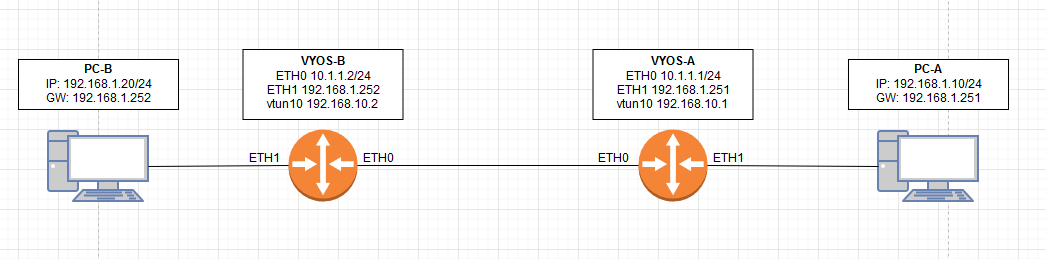
My configuration for openvpn is not working as expected and I am suspecting that I might have not configured something right.
I want to PC-A to be able to ping PC-B
VYOS-A configuration:
VYOS-A configuration:
Not using NAT, Not using Firewall.
Any Suggestions?
rob
December 15, 2019, 8:31pm
2
Hi,
the both eth1 networks on Side A and B are two different Layer2 domains so you need NAT.https://docs.vyos.io/en/latest/configuration/interfaces/bridge.html
I am actually was trying to avoid double NAT as it is a headache in troubleshooting network issues.
That is a good idea, I will try it.
I forgot to mention, openVPN link is not up, I can’t ping 192.168.10.2 from VyOS-A
vyos@vyos-A:~$ show openvpn site-to-site status
OpenVPN client status on vtun10 []
Remote CN Remote IP Tunnel IP TX byte RX byte Connected Since
--------- --------- --------- ------- ------- ---------------
None (PSK) 10.1.1.20 192.168.10.2 420 0 N/A
vyos@vyos-B:~$ show openvpn site-to-site status
OpenVPN client status on vtun10 []
Remote CN Remote IP Tunnel IP TX byte RX byte Connected Since
--------- --------- --------- ------- ------- ---------------
None (PSK) 10.1.1.10 192.168.10.1 540 0 N/A
In previous vyos/vyatta releases (1.1x), I was able to carry a L2 VLAN across an OpenVPN tunnel…and it seems to be what you’re looking for also.
Here’s my server config. I NAT the L2 VLAN out the server’s eth1 interface. In your case, since you want the remote end to be on the same VLAN as your LAN, you can add eth1 to br0 and re-assign br0 with the LAN IP.
interfaces {
bridge br0 {
address 88.88.88.1/24
description vpn_88_net
}
ethernet eth1 {
address 192.168.1.88/24
description to_LAN }
openvpn vtun1 {
bridge-group {
bridge br0
}
description tcp_8881
local-port 8881
mode site-to-site
openvpn-option --comp-lzo
protocol tcp-passive
tls {
ca-cert-file /config/auth/ca.crt
cert-file /config/auth/vpnserver.crt
dh-file /config/auth/dh.pem
key-file /config/auth/vpnserver.key
role passive
}
}
nat {
source {
rule 10 {
outbound-interface eth1
source {
address 88.88.88.0/24
}
translation {
address masquerade
}
}
}
}
service {
dhcp-server {
disabled false
shared-network-name 88NET {
authoritative disable
subnet 88.88.88.0/24 {
default-router 88.88.88.1
dns-server 88.88.88.1
domain-name 88net.local
lease 86400
start 88.88.88.100 {
stop 88.88.88.254
}
}
}
}
Remote side config:
interfaces {
bridge br0 {
description vpn_88_net
}
ethernet eth0 {
address dhcp
description WAN
}
}
ethernet eth1 {
bridge-group {
bridge br0
}
description vpn_88_net_bridgeport
}
ethernet eth2 {
bridge-group {
bridge br0
}
description vpn_88_net_bridgeport
}
ethernet eth3 {
bridge-group {
bridge br0
}
description vpn_88_net_bridgeport
}
ethernet eth4 {
bridge-group {
bridge br0
}
description vpn_88_net_bridgeport
}
ethernet eth5 {
bridge-group {
bridge br0
}
description vpn_88_net_bridgeport
}
openvpn vtun0 {
bridge-group {
bridge br0
}
description vpn_88_tunnel
mode site-to-site
openvpn-option "--comp-lzo"
protocol tcp-active
remote-host my-openvpn-server.dyndns.org
remote-port 8881
tls {
ca-cert-file /config/auth/ca.crt
cert-file /config/auth/s2sremote1.crt
key-file /config/auth/s2sremote1.key
role active
}
}
}