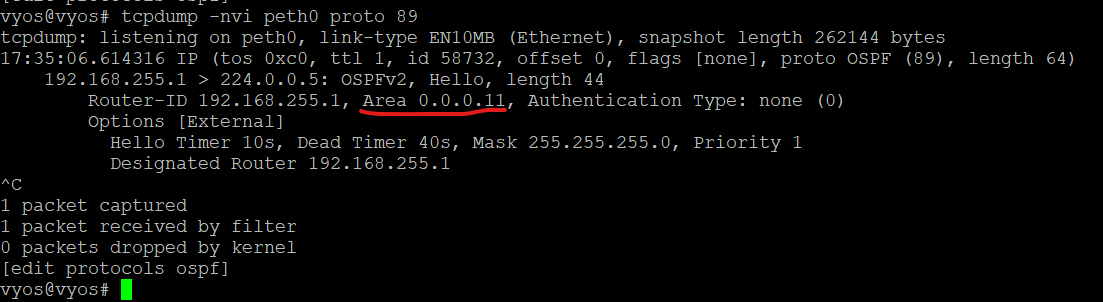
I want to setup an ospf connection to a fortigate firewall.
This will be to use an IPSec tunnel on the FortiGate to another FortiGate.
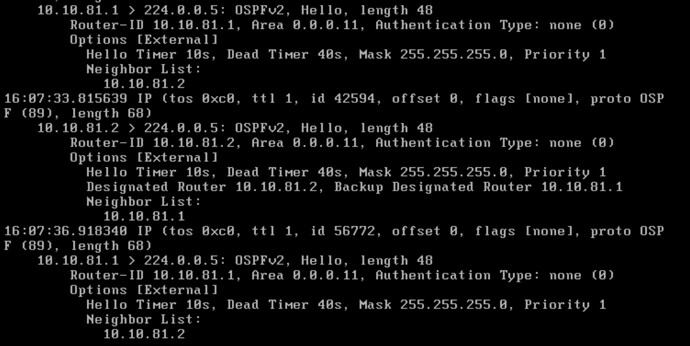
I will also be running OSPF between the IPSec tunnel.
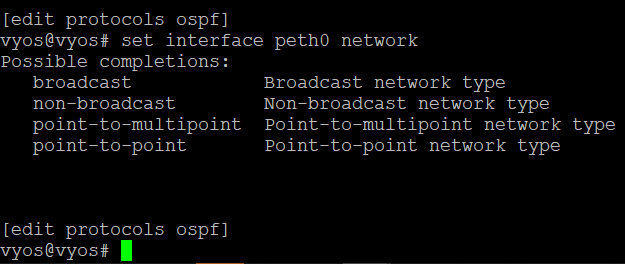
But in the meantime, I am wondering about the OSPF Config for VYOS’s side connected to both Fortigates to redistribute connected networks.
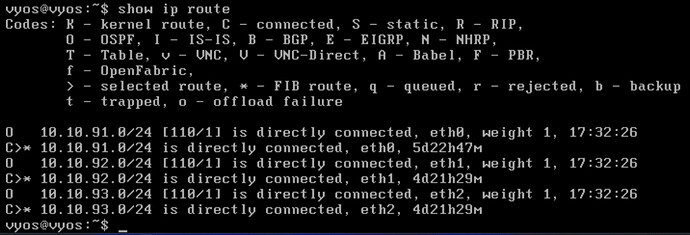
set interfaces ethernet eth0 address '10.10.91.2/24'
set interfaces ethernet eth1 address '10.10.92.1/24'
set interfaces ethernet eth2 address '10.10.93.1/24'
set policy route-map CONNECT rule 10 action 'permit'
set policy route-map CONNECT rule 10 action match interface 'eth1'
set policy route-map CONNECT rule 20 action 'permit'
set policy route-map CONNECT rule 20 action match interface 'eth2'
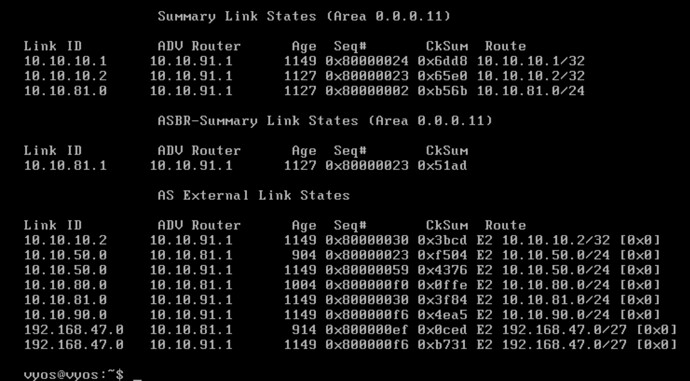
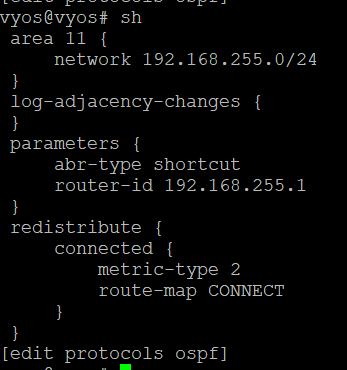
set protocols ospf area 11 network '10.10.91.0/24'
set protocols ospf area 11 network '10.10.92.0/24'
set protocols ospf area 11 network '10.10.93.0/24
set protocols ospf log-adjacency-changes
set protocols ospf parameters abr-type 'shortcut'
set protocols ospf parameters router-id '10.10.91.2'
set protocols ospf redistribute connected metric-type '2'
set protocols ospf redistribute connected route-map 'CONNECT'