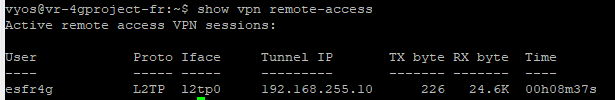
Hello All,
i’m configuring zone policy on my virtual router below my configuration.
////// ****** FIREWALL ****** ////////
firewall {
all-ping enable
broadcast-ping disable
config-trap disable
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name BLOCK-SSH-ACCESS {
default-action drop
description SSH-RESTRICTED
rule 1 {
action accept
}
rule 2 {
action accept
state {
established enable
invalid disable
related enable
}
}
rule 40 {
action accept
destination {
}
protocol esp
}
rule 41 {
action accept
destination {
port 500
}
protocol udp
}
rule 42 {
action accept
destination {
port 4500
}
protocol udp
}
rule 43 {
action accept
destination {
port 1701
}
ipsec {
match-ipsec
}
protocol udp
}
}
///// ******* ///////
interfaces {
bridge br0 {
address 192.168.255.1/24
description "L2 VPN Bridge"
}
ethernet eth0 {
address 172.24.2.95/19
duplex auto
hw-id 00:50:56:98:2a:15
smp-affinity auto
speed auto
}
ethernet eth1 {
bridge-group {
bridge br0
}
description "L2 VPN Physical port"
duplex auto
hw-id 00:50:56:98:b4:e3
smp-affinity auto
speed auto
vif 266 {
address 192.168.0.1/24
description LAN-IA
}
vif 267 {
address 192.168.1.1/24
description ENB-MGMT
}
vif 268 {
address 192.168.2.1/24
description MGMT-SRV
}
}
ethernet eth2 {
[ IP ADRRESS CONFIDENTIAL]
}
l2tpv3 l2tpeth0 {
bridge-group {
bridge br0
}
local-ip 192.168.255.1
peer-session-id 110
peer-tunnel-id 10
remote-ipX.X.X.X
session-id 110
tunnel-id 10
}
loopback lo {
}
}
////////////// *********** ZONE POLICY *************** /////////////////
zone-policy {
zone LAN266 {
default-action drop
from WAN {
firewall {
name BLOCK-SSH-ACCESS
}
}
interface eth1.266
}
zone LAN267 {
default-action drop
interface eth1.267
}
zone LAN268 {
default-action drop
interface eth1.268
}
zone WAN {
default-action drop
from LAN266 {
firewall {
name BLOCK-SSH-ACCESS
}
}
from br0l2tp {
firewall {
name BLOCK-SSH-ACCESS
}
}
from l2tp {
firewall {
name BLOCK-SSH-ACCESS
}
}
interface eth2
}
zone br0l2tp {
from WAN {
firewall {
name BLOCK-SSH-ACCESS
}
}
interface br0
}
zone l2tp {
from WAN {
firewall {
name BLOCK-SSH-ACCESS
}
}
interface l2tpeth0
}
}
[[[[[[[[[[[[[[[[[[[[[[[
set zone-policy zone LAN266 default-action 'drop'
set zone-policy zone LAN266 from WAN firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone LAN266 interface 'eth1.266'
set zone-policy zone LAN267 default-action 'drop'
set zone-policy zone LAN267 interface 'eth1.267'
set zone-policy zone LAN268 default-action 'drop'
set zone-policy zone LAN268 interface 'eth1.268'
set zone-policy zone WAN default-action 'drop'
set zone-policy zone WAN from LAN266 firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone WAN from br0l2tp firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone WAN from l2tp firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone WAN interface 'eth2'
set zone-policy zone br0l2tp from WAN firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone br0l2tp interface 'br0'
set zone-policy zone l2tp from WAN firewall name 'BLOCK-SSH-ACCESS'
set zone-policy zone l2tp interface 'l2tpeth0'
]]]]]]]]]]]]]]]]]]]]]]]]]]]]]]
Internet Acces on VLAN authorized works fine. but L2TP/IPSEC is broken.
//////////// **************** ZONE POLICY CONFIGURATION ARRAY*********************** //////////////////
vyos@vr-4gproject-fr:~$ show zone-policy
-------------------
Name: LAN266
Interfaces: eth1.266
From Zone:
name firewall
---- --------
WAN BLOCK-SSH-ACCESS
-------------------
Name: LAN267
Interfaces: eth1.267
From Zone:
name firewall
---- --------
-------------------
Name: LAN268
Interfaces: eth1.268
From Zone:
name firewall
---- --------
-------------------
Name: WAN
Interfaces: eth2
From Zone:
name firewall
---- --------
LAN266 BLOCK-SSH-ACCESS
br0l2tp BLOCK-SSH-ACCESS
l2tp BLOCK-SSH-ACCESS
-------------------
Name: br0l2tp
Interfaces: br0
From Zone:
name firewall
---- --------
WAN BLOCK-SSH-ACCESS
-------------------
Name: l2tp
Interfaces: l2tpeth0
From Zone:
name firewall
---- --------
WAN BLOCK-SSH-ACCESS
Thanks in advance.