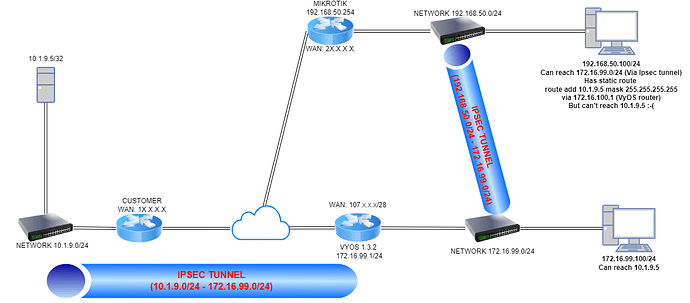
We have the following scenario:
VyOS router with two interfaces (WAN/LAN)
WAN is directly connected to internet and has an address like ‘107.x.x.x/28’ and it works perfecty.
LAN is 172.16.99.1/24
Two Ipsec tunnels
- Local subnet 172.16.99.1/24 and remote subnet 10.1.10.0/24
- Local subnet 172.16.99.1/24 and remote subnet 192.168.50.0/24
From a computer on subnet 192.168.50.0/24 we can ping to 172.16.99.1.
We need to have access to subnet 10.1.10.0/24 from 192.168.50.0/24 then we have added static routes on the computers on 192.168.50.0/24 like this
route add 10.1.10.0 mask 255.255.255.0 172.16.99.1
but it’s not working.
How can we route traffic between 192.168.50.0/24 and 10.1.10.0/24?
Can you share vpn configuration and vyos version? Are you using policy-based or route-based VPN?
Here you can find configuration example: Site-to-Site — VyOS 1.4.x (sagitta) documentation
We are using VyOS 1.3.2 and here is full config.
set interfaces ethernet eth0 address ‘107.x.x.x/28’
set interfaces ethernet eth1 address ‘172.16.99.1/24’
set protocols static route 0.0.0.0/0 next-hop 107.x.x.1
set service ssh
set system name-server ‘1.x.x.x’
set system name-server ‘1.x.x.x’
set vpn ipsec esp-group ESP-1MIKRO compression ‘disable’
set vpn ipsec esp-group ESP-1MIKRO lifetime ‘3600’
set vpn ipsec esp-group ESP-1MIKRO mode ‘tunnel’
set vpn ipsec esp-group ESP-1MIKRO pfs ‘enable’
set vpn ipsec esp-group ESP-1MIKRO proposal 1 encryption ‘aes128’
set vpn ipsec esp-group ESP-1MIKRO proposal 1 hash ‘sha1’
set vpn ipsec esp-group ESP-TRR compression ‘disable’
set vpn ipsec esp-group ESP-TRR lifetime ‘43200’
set vpn ipsec esp-group ESP-TRR mode ‘tunnel’
set vpn ipsec esp-group ESP-TRR pfs ‘enable’
set vpn ipsec esp-group ESP-TRR proposal 1 encryption ‘aes256’
set vpn ipsec esp-group ESP-TRR proposal 1 hash ‘sha256’
set vpn ipsec ike-group IKE-1MIKRO ikev2-reauth ‘no’
set vpn ipsec ike-group IKE-1MIKRO key-exchange ‘ikev1’
set vpn ipsec ike-group IKE-1MIKRO lifetime ‘28800’
set vpn ipsec ike-group IKE-1MIKRO proposal 1 dh-group ‘5’
set vpn ipsec ike-group IKE-1MIKRO proposal 1 encryption ‘aes128’
set vpn ipsec ike-group IKE-1MIKRO proposal 1 hash ‘sha1’
set vpn ipsec ike-group IKE-TRR close-action ‘none’
set vpn ipsec ike-group IKE-TRR ikev2-reauth ‘no’
set vpn ipsec ike-group IKE-TRR key-exchange ‘ikev2’
set vpn ipsec ike-group IKE-TRR lifetime ‘86400’
set vpn ipsec ike-group IKE-TRR proposal 1 dh-group ‘19’
set vpn ipsec ike-group IKE-TRR proposal 1 encryption ‘aes256’
set vpn ipsec ike-group IKE-TRR proposal 1 hash ‘sha256’
set vpn ipsec ipsec-interfaces interface ‘eth0’
set vpn ipsec nat-traversal ‘disable’
set vpn ipsec site-to-site peer 2x.x.x.x authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer 2x.x.x.x authentication pre-shared-secret ‘xxxxxxxxxxxxx’
set vpn ipsec site-to-site peer 2x.x.x.x connection-type ‘respond’
set vpn ipsec site-to-site peer 2x.x.x.x ike-group ‘IKE-1MIKRO’
set vpn ipsec site-to-site peer 2x.x.x.x ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer 2x.x.x.x local-address ‘107.x.x.x’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 1 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 1 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 1 esp-group ‘ESP-1MIKRO’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 1 local prefix ‘172.16.99.0/24’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 1 remote prefix ‘192.168.50.0/24’
set vpn ipsec site-to-site peer 1x.x.x.x authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer 1x.x.x.x authentication pre-shared-secret ‘xxxxxxxxxxxxx’
set vpn ipsec site-to-site peer 1x.x.x.x connection-type ‘initiate’
set vpn ipsec site-to-site peer 1x.x.x.x ike-group ‘IKE-TRR’
set vpn ipsec site-to-site peer 1x.x.x.x ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer 1x.x.x.x local-address ‘any’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 1 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 1 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 1 esp-group ‘ESP-TRR’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 1 local prefix ‘172.16.99.0/24’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 1 remote prefix ‘10.1.9.5/32’
Routing is not enough for IPSEC, at least in this config.
You also need to define any additional tunnels with the subnets that will be considered as “interesting traffic” so it can be encrypted and sent along. In Cisco routers this is accomplished by creating ACLs and associating them to the crypto map. Here I believe you would create additional tunnels with the criteria to match on the subnet (local/remote prefixes). Once you send a ping across it should show up as an additional SA in show vpn ipsec sa
Looking over the doc link @n.fort provided I’m thinking to make all this easier on yourself you may want to convert this into a setup that uses a VTI. Then you don’t have to worry about any additional SAs forming or breaking. Anything sent to the VTI is encrypted and sent right along and the static route will come into play.
Keep us up to date
1 Like
We can’t use VTI on peer 2x.x.xx.x and peer 1x.x.x.x because we have no control about theese routers. Peer 2x.x.x.x uses Mikrotik.
Ugh, Mikrotik really needs to roll VTI out in RouterOS. I’m going to ask this even though I have a hunch the answer will be no for whatever reason.
Why do those two sites not have their own ipsec tunnel?
Policy based ipsec can turn into a nightmare, you are better off configuring GRE/IPsec if you can’t do VTI. Tunnel traffic would be the interesting traffic and the GRE tunnel would only be in UP state if there is an established SA.
See: IPsec policy matching GRE
This has nothing to do with IPSEC. Routing between those remote subnets should be configured on remote router itself
1 Like
mmmmmmm didn’t read this close enough…
Yes my bad… @jotauve he is correct. You let the routers handle that upstream, not on the computers. Betting your pings were making it to 10.1.10.x but had no return path.
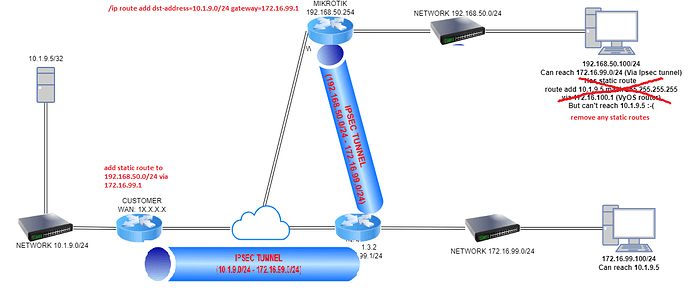
Here is a schema. Hope it helps.
Did a little rearranging, here’s what needs to be done.
On VyOS , you need 4 VPN tunnels 2 for each peer. Add something like:
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 2 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 2 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 2 esp-group ‘ESP-TRR’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 2 local prefix ‘192.168.50.0/24’
set vpn ipsec site-to-site peer 1x.x.x.x tunnel 2 remote prefix ‘10.1.9.5/32’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 2 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 2 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 2 esp-group ‘ESP-1MIKRO’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 2 local prefix ‘10.1.9.5/32’
set vpn ipsec site-to-site peer 2x.x.x.x tunnel 2 remote prefix ‘192.168.50.0/24’
But this requires changes on remotes too, so better setup a direct tunnel between those 2 peers.
2 Likes