Dear community
I struggle for the second day, ChatGPTing, googleing, searching in the forum and trying different solutions.
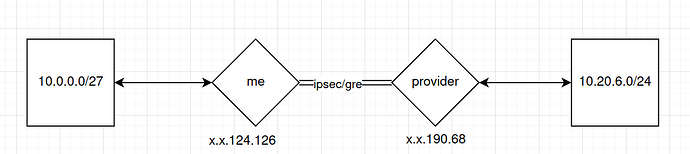
The issue in is that the ikev2 vpn tunnel to the remote provider Fortigate is connected but no traffic is going through.
The current overview and configuration:
OnSite (at OVH):
- Server: Proxmox VE Advance server with 1 additional IP
- virtual Vyos:
VyOS 1.5-rolling-202411050007
- OVH specific routing rule in
/config/scripts/vyos-postconfig-bootup.script
sudo ip route replace default via 192.168.0.1 dev eth0 onlink src X.X.124.126
- vyos configuration
set interfaces ethernet eth0 address '192.168.0.2/24'
set interfaces ethernet eth0 address 'X.X.124.126/32'
set interfaces ethernet eth1 vif 100 address '10.0.1.1/27'
set interfaces ethernet eth2 vif 200 address '10.0.0.1/27'
set interfaces loopback lo
set interfaces tunnel tun20 encapsulation 'gre'
set interfaces tunnel tun20 parameters ip key '1'
set interfaces tunnel tun20 remote 'x.x.190.68'
set interfaces tunnel tun20 source-address 'x.x.124.126'
set protocols static route 0.0.0.0/0 interface eth0
set protocols static route 0.0.0.0/0 next-hop 192.168.0.1
set protocols static route 10.20.6.0/24 interface tun20
set protocols static route 10.20.6.0/24 next-hop x.x.190.68
set vpn ipsec authentication psk companya id 'x.x.190.68'
set vpn ipsec authentication psk companya secret 'arealsecred'
set vpn ipsec esp-group ESP-Group lifetime '3600'
set vpn ipsec esp-group ESP-Group mode 'tunnel'
set vpn ipsec esp-group ESP-Group pfs 'enable'
set vpn ipsec esp-group ESP-Group proposal 1 encryption 'aes256'
set vpn ipsec esp-group ESP-Group proposal 1 hash 'sha384'
set vpn ipsec ike-group IKE-Group key-exchange 'ikev2'
set vpn ipsec ike-group IKE-Group lifetime '86400'
set vpn ipsec ike-group IKE-Group proposal 1 dh-group '14'
set vpn ipsec ike-group IKE-Group proposal 1 encryption 'aes256'
set vpn ipsec ike-group IKE-Group proposal 1 hash 'sha384'
set vpn ipsec interface 'eth0'
set vpn ipsec log level '2'
set vpn ipsec options virtual-ip
set vpn ipsec site-to-site peer companya authentication local-id 'x.x.124.126'
set vpn ipsec site-to-site peer companya authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer companya authentication remote-id 'x.x.190.68'
set vpn ipsec site-to-site peer companya default-esp-group 'ESP-Group'
set vpn ipsec site-to-site peer companya ike-group 'IKE-Group'
set vpn ipsec site-to-site peer companya local-address 'x.x.124.126'
set vpn ipsec site-to-site peer companya remote-address 'x.x.190.68'
set vpn ipsec site-to-site peer companya tunnel 1 local prefix '0.0.0.0/0'
set vpn ipsec site-to-site peer companya tunnel 1 protocol 'gre'
set vpn ipsec site-to-site peer companya tunnel 1 remote prefix '0.0.0.0/0'
- connection is open:
show vpn ipsec sa
Connection State Uptime Bytes In/Out Packets In/Out Remote address Remote ID Proposal
----------------------------- ------- -------- -------------- ---------------- ---------------- ------------ -----------------------------
convotis-tunnel-1-passthrough up 24m59s 0B/0B 0/0 x.x.190.68 x.x.190.68 AES_CBC_256/HMAC_SHA2_384_192
show vpn ike sa
Peer ID / IP Local ID / IP
------------ -------------
x.x.190.68 x.x.190.68 x.x.124.126 x.x.124.126
State IKEVer Encrypt Hash D-H Group NAT-T A-Time L-Time
----- ------ ------- ---- --------- ----- ------ ------
up IKEv2 AES_CBC_256 HMAC_SHA2_384_192 MODP_2048 no 1545 78522
- routing information
S 0.0.0.0/0 [1/0] is directly connected, eth0, weight 1, 00:25:43
via 192.168.0.1, eth0, weight 1, 00:25:43
K>* 0.0.0.0/0 [0/0] via 192.168.0.1, eth0 onlink, src x.x.124.126, 01:30:22
C>* 10.0.0.0/27 is directly connected, eth2.200, 01:30:25
C>* 10.0.1.0/27 is directly connected, eth1.100, 01:30:26
S 10.1.1.0/24 [1/0] is directly connected, vtun10, weight 1, 01:30:24
C>* 10.1.1.0/24 is directly connected, vtun10, 01:30:24
S>* 10.20.6.0/24 [1/0] is directly connected, tun20, weight 1, 00:32:16
via x.x.190.68 (recursive), weight 1, 00:32:16
* via 192.168.0.1, eth0 onlink, weight 1, 00:32:16
C>* x.x.124.126/32 is directly connected, eth0, 01:30:26
C>* 192.168.0.0/24 is directly connected, eth0, 01:30:26
- a traffic dump while try to connect to the other side
udo tcpdump -i eth0 host x.x.190.68
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
08:28:35.373924 IP x.x.124.126 > x.x.190.68: GREv0, key=0x1, length 60: IP 10.0.0.6.53596 > 10.20.6.101.http: Flags [SEW], seq 1781393755, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
08:28:36.374386 IP x.x.124.126 > x.x.190.68: GREv0, key=0x1, length 60: IP 10.0.0.6.53596 > 10.20.6.101.http: Flags [SEW], seq 1781393755, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
- not part of this configuration is my remote access via OpenVPN to vyos, this works perfectly
OffSite (Service Provider)
- Fortigate Firewall
- Destination Network 10.20.6.0/24
Your help would mean a lot, especially as I have a highly pregnant wife at home and need to resolve this as soon as possible ![]()
All the best Steffen