Hello, new to VyOS. Using as my home router/firewall, but looking for help with either a firewall or system configure issue. Here is the context:
- VyOS 1.5-Rolling router
- hosted in ESXi
- two nics (LAN and WAN)
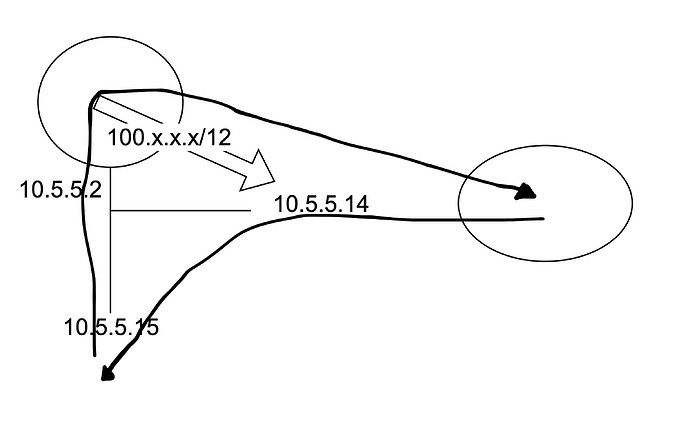
- LAN side is 10.5.5.2
- All nodes on network use 10.5.5.2 as GW
- 10.5.5.14 hosts my tailscale client
- I have a static route for 100.x.x.x/12 via 10.5.5.14 within VyOS
- 100.x.x.x is the IP to one instance on my tailscale network
- I’m essentially using Quick Start — VyOS 1.5.x (circinus) documentation as my starting point.
I’ve previously had this working on my EdgeOS system, but not quite sure what is different between that and the VyOS system. Comparing the configs isn’t trivial since they are quite different.
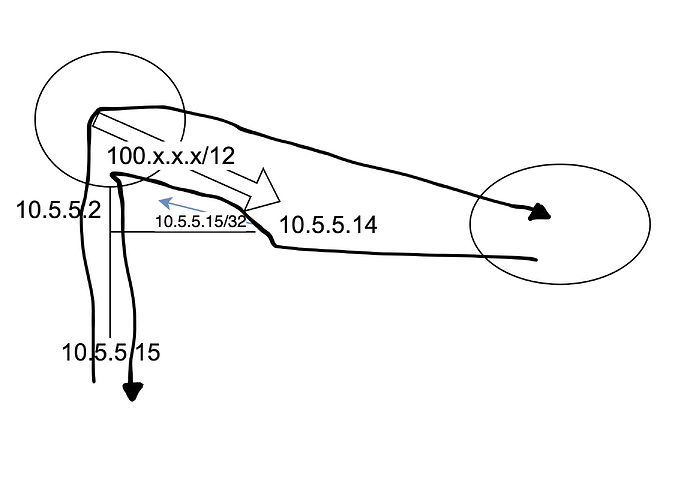
I’d like to have VyOS route traffic to a router on the same L3 segment without using ICMP redirects. The router is not resource constrained. I’d rather avoid the extra chatter of the ICMP redirects if I can.
Here is my problem that I’m noticing. I’m trying to access a HTTP service on 100.x.x.x:9000 from a machine (10.5.5.15) that doesn’t accept [ICMP] redirects. This is apparent because I see host 10.5.5.15/if2 ignores redirects for 100.x.x.x. to 10.5.5.14 within dmesg on my VyOS box. Other machines with accept [ICMP] redirects can complete the request just fine. Enabling this machine to accept redirects allows curl to complete the request. This also updates my ip route get 100.x.x.x to return back 10.5.5.14 instead of the default gateway, the whole purpose of ICMP redirects.
What’s interesting is that some packet get routed as seen via tcpdump on 10.5.5.14 or 100.x.x.x, but the TCP stream cannot complete the connection to transfer the rest of the packets. This makes me think there is some state that gets built up during the first few packets, but then gets filtered out.
My understanding is that even through the kernel notices there is a better route, it will still forward the packet to my destination, but also notify my host of that better route. This is why I think I see partial packets land at the destination. Even if I tell VyOS to disable send-redirects curl continues to not complete the request.