Hi All,
Recently I decided to setup a WireGuard Road Warrior configuration and thought I’d share the experience in case someone else was looking at doing the same.
The documentation is here but it piggybacks off Site-Site and took me a little more reading to work out what was actually needed. So I’ve tried to simplify it even further.
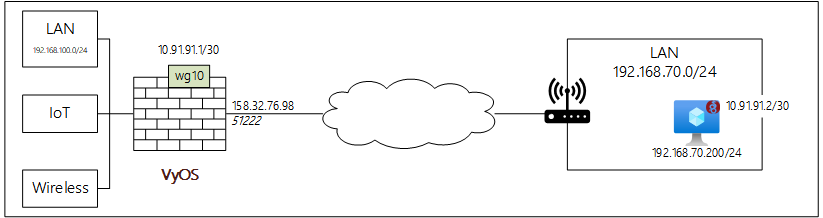
Here is the idea. I want to connect a Linux VM from remote location to SOHO.
Create a Private & Public Keys for both Server and Client
Keys will be generated for you and replace the placeholders below. Keep these handy but hidden ![]()
# Generate key pair for Server Side
run generate pki wireguard key-pair
Private key: <SERVER_PRIVATEKEY>
Public key: <SERVER_PUBLICKEY>
# Generate key pair for Client Side.
run generate pki wireguard key-pair
Private key: <CLIENT_PRIVATEKEY>
Public key: <CLIENT_PUBLICKEY>
Create a preshared key
Like mentioned this is optional but a good to have I guess.
run generate pki wireguard preshared-key
Pre-shared key: <PRESHARED_KEY>
VyOS Wireguard Configuration
Set our internal address as shown in diagram above. Couple of things to note:
I use PPPoE and after some reading it recommends using an MTU of 1412.
We add our remote host whatever name ArchLinux + information as well. We only add the remote WireGuard endpoint address 10.91.91.2/32
set interfaces wireguard wg10 address '10.91.91.1/30'
set interfaces wireguard wg10 description 'RoadRunner'
set interfaces wireguard wg10 ip adjust-mss 'clamp-mss-to-pmtu'
set interfaces wireguard wg10 mtu '1412'
set interfaces wireguard wg10 peer ArchLinux allowed-ips '10.91.91.2/32'
set interfaces wireguard wg10 peer ArchLinux persistent-keepalive '15'
set interfaces wireguard wg10 peer ArchLinux public-key '<CLIENT_PUBLICKEY>'
set interfaces wireguard wg10 peer ArchLinux preshared-key '<PRESHARED_KEY>'
set interfaces wireguard wg10 port '51222'
set interfaces wireguard wg10 private-key '<SERVER_PRIVATEKEY>'
Firewall Rules + zones
I use firewall zones, so in my case I had to add additional zone and rules for WireGuard.
# Allow external to access Wireguard port.
set firewall ipv4 name WAN-LOCAL default-log
set firewall ipv4 name WAN-LOCAL rule 1000 action 'accept'
set firewall ipv4 name WAN-LOCAL rule 1000 description 'Allow WIREGUARD-IN WAN-LOCAL'
set firewall ipv4 name WAN-LOCAL rule 1000 destination port '51222'
set firewall ipv4 name WAN-LOCAL rule 1000 log
set firewall ipv4 name WAN-LOCAL rule 1000 protocol 'udp'
# For now just allow icmp from LAN to WIREGUARD. More rules can be added later.
set firewall ipv4 name LAN-WIREGUARD rule 101 action 'accept'
set firewall ipv4 name LAN-WIREGUARD rule 101 description 'Allow ICMP LAN-WAN'
set firewall ipv4 name LAN-WIREGUARD rule 101 icmp type-name 'echo-request'
set firewall ipv4 name LAN-WIREGUARD rule 101 log
set firewall ipv4 name LAN-WIREGUARD rule 101 protocol 'icmp'
set firewall ipv4 name LAN-WIREGUARD rule 101 state 'new'
# For now just allow icmp from Wireguard to LAN. More rules can be added later.
set firewall ipv4 name WIREGUARD-LAN rule 101 action 'accept'
set firewall ipv4 name WIREGUARD-LAN rule 101 description 'Allow ICMP WIREGUARD-LAN'
set firewall ipv4 name WIREGUARD-LAN rule 101 icmp type-name 'echo-request'
set firewall ipv4 name WIREGUARD-LAN rule 101 log
set firewall ipv4 name WIREGUARD-LAN rule 101 protocol 'icmp'
set firewall ipv4 name WIREGUARD-LAN rule 101 state 'new'
# Add new rule to existing zone LAN.
set firewall zone LAN from WIREGUARD firewall name 'WIREGUARD-LAN'
# Add new zone for Wireguard
set firewall zone WIREGUARD default-action 'drop'
set firewall zone WIREGUARD default-log
set firewall zone WIREGUARD from LAN firewall name 'LAN-WIREGUARD'
set firewall zone WIREGUARD interface 'wg10'
Note: No need a static route because network 10.91.91.0/30 is visible to VyOS on interface wg10. This would only be required if routing via a remote firewall/router.
Linux VM side configuration
Install WireGuard onto your remote system. Mine used NetworkManager, although may differ depending on the network service used (systemd.networkd, networking is slightly different).
Create a file with the name of the adapter you want e.g WireGuard.config (adapter will be called WireGuard). This file is specific to WireGuard so will be the same on any distribution.
Also noticed that some example configs show a “-” between words (private-key, public-key ) and others don’t, seems not to matter?
Add our external address + port and allowed internal IPs you wish to reach. In this case LAN.
[Interface]
privatekey = <CLIENT_PRIVATEKEY>
address = 10.91.91.2/32
dns = 1.1.1.1
[Peer]
publickey = <SERVER_PUBLICKEY>
endpoint = 158.32.76.98:51222
allowedips = 192.168.100.0/24
presharedkey = <PRESHARED_KEY>
Apply the configuration to NetworkManager.
nmcli connection import type wireguard file \<location>\WireGuard.conf
You should now be able to ping from remote to LAN and from LAN to remote endpoint 10.91.91.2/30 (not 192.168.70.200/24).
Hope this helps someone.