Hi,
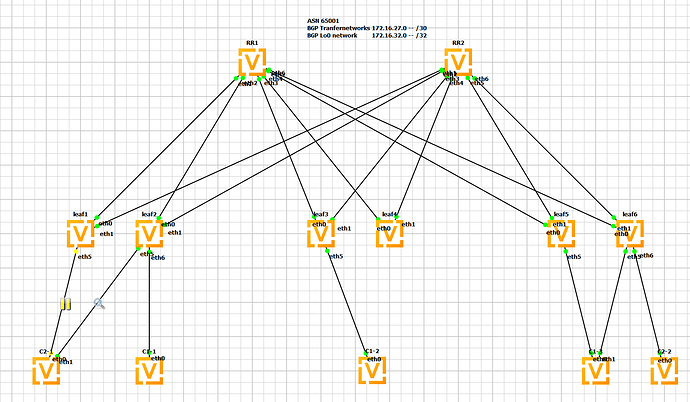
at the moment im testing a leaf-spine vxlan fabric for L2/L3 VPNs in GNS3 with VyOS 1.4.0-epa1
i tried both supported ways to use VXLAN in VyOS and the new way - single VXLAN Device, supported by FRR wont work.
CPE C2-1 is uplinked to leaf1 and leaf2 via ESI-LAG (i know that ESI-LAG all active is not working at the moment).
If the Traffic is passing the link to leaf1 everything is fine and CPE C2-1 can ping the vlan IP Interfaces 100 and 200 of CPE C2-2 via leaf6.
Here is the configuration of …
CPE2-1
Summary
vyos@vyos# show interfaces
bonding bond0 {
description "to leaf1 and leaf2"
lacp-rate fast
member {
interface eth0
interface eth1
}
mode 802.3ad
vif 100 {
address 10.0.100.1/24
}
vif 120 {
address 10.0.120.1/24
}
vif 130 {
address 10.0.130.1/24
}
}
leaf1
Summary
vyos@leaf1# show
interfaces {
bonding bond0 {
description "to C2-1"
evpn {
es-id 00:00:00:00:00:00:00:00:00:01
es-df-pref 1
}
lacp-rate fast
member {
interface eth5
}
min-links 1
mode 802.3ad
vif 100 {
}
vif 120 {
}
vif 130 {
}
}
bridge br100 {
member {
interface bond0.100 {
}
interface vxlan100 {
}
}
}
bridge br120 {
member {
interface bond0.120 {
}
interface vxlan120 {
}
}
}
bridge br130 {
member {
interface bond0.130 {
}
interface vxlan130 {
}
}
}
ethernet eth0 {
address 172.16.27.6/30
description "to RR1"
hw-id 0c:ae:b1:89:00:00
}
ethernet eth1 {
address 172.16.27.46/30
description "to RR2"
hw-id 0c:ae:b1:89:00:01
}
loopback lo {
address 172.16.32.1/32
}
vxlan vxlan100 {
source-address 172.16.32.1
vni 100
}
vxlan vxlan120 {
source-address 172.16.32.1
vni 120
}
vxlan vxlan130 {
source-address 172.16.32.1
vni 130
}
}
protocols {
bfd {
peer 172.16.27.5 {
source {
address 172.16.27.6
}
}
peer 172.16.27.45 {
source {
address 172.16.27.46
}
}
}
bgp {
address-family {
ipv4-unicast {
maximum-paths {
ibgp 4
}
redistribute {
connected {
}
}
}
l2vpn-evpn {
advertise-all-vni
}
}
neighbor 172.16.27.5 {
peer-group evpn
}
neighbor 172.16.27.45 {
peer-group evpn
}
parameters {
log-neighbor-changes
}
peer-group evpn {
address-family {
ipv4-unicast {
nexthop-self {
}
}
l2vpn-evpn {
nexthop-self {
}
}
}
bfd {
}
remote-as 65001
}
system-as 65001
}
}
leaf6
Summary
vyos@leaf6# show
interfaces {
bridge br100 {
member {
interface eth6.100 {
}
interface vxlan100 {
}
}
}
bridge br120 {
member {
interface eth6.120 {
}
interface vxlan120 {
}
}
}
ethernet eth0 {
address 172.16.27.26/30
description "to RR1"
hw-id 0c:38:79:07:00:00
}
ethernet eth1 {
address 172.16.27.66/30
description "to RR2"
hw-id 0c:38:79:07:00:01
}
loopback lo {
address 172.16.32.6/32
}
vxlan vxlan100 {
source-address 172.16.32.6
vni 100
}
vxlan vxlan120 {
source-address 172.16.32.6
vni 120
}
}
protocols {
bfd {
peer 172.16.27.25 {
source {
address 172.16.27.26
}
}
peer 172.16.27.65 {
source {
address 172.16.27.66
}
}
}
bgp {
address-family {
ipv4-unicast {
maximum-paths {
ibgp 4
}
redistribute {
connected {
}
}
}
l2vpn-evpn {
advertise-all-vni
}
}
neighbor 172.16.27.25 {
peer-group evpn
}
neighbor 172.16.27.65 {
peer-group evpn
}
parameters {
log-neighbor-changes
}
peer-group evpn {
address-family {
ipv4-unicast {
nexthop-self {
}
}
l2vpn-evpn {
nexthop-self {
}
}
}
bfd {
}
remote-as 65001
}
system-as 65001
}
}
CPE C2-2
Summary
vyos@vyos# show
interfaces {
ethernet eth0 {
hw-id 0c:2a:a4:39:00:00
vif 100 {
address 10.0.100.10/24
}
vif 120 {
address 10.0.120.10/24
}
vif 130 {
address 10.0.130.10/24
}
}
Unforunatly when i suspend the link to leaf1 to force the traffic passing leaf2 with the new configuration for single VXLAN Device (SVD) its no longer functional.
VyOS Docs: VXLAN — VyOS 1.4.x (sagitta) documentation
FRR Docs: Zebra — FRR latest documentation
leaf2
Summary
vyos@leaf2# show
interfaces {
bonding bond0 {
description "to C2-1"
evpn {
es-id 00:00:00:00:00:00:00:00:00:01
es-df-pref 2
}
lacp-rate fast
member {
interface eth5
}
min-links 1
mode 802.3ad
vif 100 {
}
vif 120 {
}
vif 130 {
}
}
bridge br0 {
enable-vlan
member {
interface vxlan0 {
}
}
vif 100 {
}
vif 120 {
}
vif 130 {
}
}
ethernet eth0 {
address 172.16.27.10/30
description "to RR1"
hw-id 0c:bb:04:f3:00:00
}
ethernet eth1 {
address 172.16.27.50/30
description "to RR2"
hw-id 0c:bb:04:f3:00:01
}
loopback lo {
address 172.16.32.2/32
}
vxlan vxlan0 {
parameters {
external
}
source-address 172.16.32.2
vlan-to-vni 100 {
vni 100
}
vlan-to-vni 120 {
vni 120
}
vlan-to-vni 130 {
vni 130
}
}
}
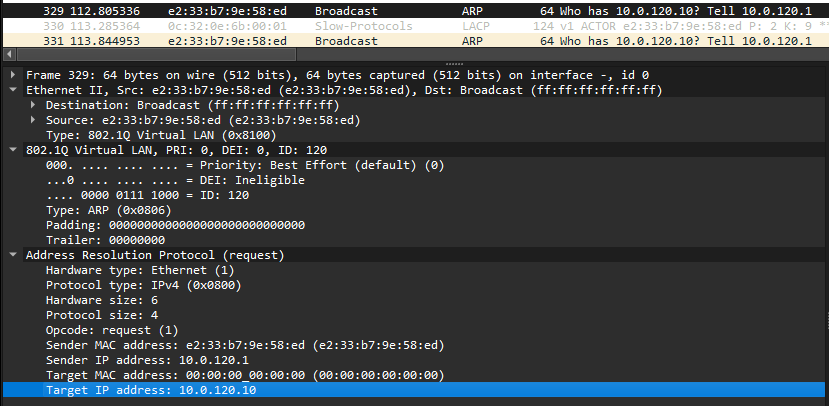
I captured the Traffic on the links CPE C2-1 ↔ leaf2 and there are arp requests in vlan120.
As expected i see the same with “monitor traffic interface bond0.120”
vyos@leaf2# run monitor traffic interface bond0.120
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on bond0.120, link-type EN10MB (Ethernet), snapshot length 262144 bytes
12:01:14.175214 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
12:01:15.057351 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
12:01:16.098426 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
12:01:17.105478 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
12:01:18.129440 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
12:01:19.169472 ARP, Request who-has 10.0.120.10 tell 10.0.120.1, length 46
a capture on interface vxlan0 says
vyos@leaf2:~$ monitor traffic interface vxlan0
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on vxlan0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
12:10:08.823539 ARP, Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:10:09.831335 ARP, Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:10:10.854735 ARP, Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:10:11.895945 ARP, Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:10:12.903106 ARP, Request who-has 10.0.120.1 tell 10.0.120.10, length 46
and a capture on the bridge Interface, wich should combine these interfaces, only receives Traffic from vlan120
vyos@leaf2:~$ monitor traffic interface br0 verbose
tcpdump: listening on br0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
12:11:23.559043 0c:2a:a4:39:00:00 > ff:ff:ff:ff:ff:ff, ethertype 802.1Q (0x8100), length 64: vlan 120, p 0, ethertype ARP (0x0806), Ethernet (len 6), IPv4 (len 4), Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:11:24.582828 0c:2a:a4:39:00:00 > ff:ff:ff:ff:ff:ff, ethertype 802.1Q (0x8100), length 64: vlan 120, p 0, ethertype ARP (0x0806), Ethernet (len 6), IPv4 (len 4), Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:11:25.623667 0c:2a:a4:39:00:00 > ff:ff:ff:ff:ff:ff, ethertype 802.1Q (0x8100), length 64: vlan 120, p 0, ethertype ARP (0x0806), Ethernet (len 6), IPv4 (len 4), Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:11:26.630752 0c:2a:a4:39:00:00 > ff:ff:ff:ff:ff:ff, ethertype 802.1Q (0x8100), length 64: vlan 120, p 0, ethertype ARP (0x0806), Ethernet (len 6), IPv4 (len 4), Request who-has 10.0.120.1 tell 10.0.120.10, length 46
12:11:27.655094 0c:2a:a4:39:00:00 > ff:ff:ff:ff:ff:ff, ethertype 802.1Q (0x8100), length 64: vlan 120, p 0, ethertype ARP (0x0806), Ethernet (len 6), IPv4 (len 4), Request who-has 10.0.120.1 tell 10.0.120.10, length 46
i tried to add in the bride member interface vxlan0 the vlans as “allowed vlan” - same result
i also tried to add bond0.vlan to the bridge instead of tagging the vlan to the bridge if - same result
show evpn access-vlan and show bridge vlan tunnel looks both like the sample output in the FRR documentation
vyos@leaf2:~$ show evpn access-vlan
VLAN SVI L2-VNI VXLAN-IF # Members
br0 .100 br0.100 0 vxlan0 0
br0 .130 br0.130 0 vxlan0 0
br0 .120 br0.120 0 vxlan0 0
vyos@leaf2:~$
vyos@leaf2:~$ show bridge vlan tunnel
Interface VLAN VNI
----------- ------ -----
vxlan0 100 100
120 120
130 130
Is there any statement missing to match Traffic from vlan to vni on leaf2?
And is there a Plan to introduce all active esi lag?
Thanks for help