Keyvan
November 10, 2020, 11:17am
1
Hi community
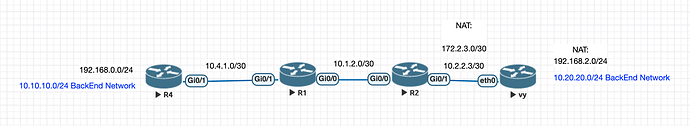
in this scenario I am trying to establish an IPSec between 192.168.2.1(vyos right side) and 10.4.1.2(cisco router in the left side)
in my scenario 192.168.2.1 is behind the nat and translated to 172.2.3.1.
I use
but its not still working
I will attach the VyOS and Cisco router configuration
cisco-router.txt (3 KB) Vy-cfg.txt (2.0 KB)
Thanks you
Is it works without NAT? One typo
eth0 10.2.2 .3 on the network map and 10.2.3 .2 in the vyos config.
1 Like
Try that configuration.
set interfaces dummy dum0 address '10.20.20.1/24'
set interfaces ethernet eth0 address '10.2.3.2/30'
set protocols static route 10.4.1.0/30 next-hop 10.2.3.1
set system host-name 'vyos'
set vpn ipsec esp-group VR02_esp compression 'disable'
set vpn ipsec esp-group VR02_esp lifetime '3600'
set vpn ipsec esp-group VR02_esp mode 'tunnel'
set vpn ipsec esp-group VR02_esp pfs 'disable'
set vpn ipsec esp-group VR02_esp proposal 1 encryption 'aes256'
set vpn ipsec esp-group VR02_esp proposal 1 hash 'sha256'
set vpn ipsec ike-group VR02_ike close-action 'none'
set vpn ipsec ike-group VR02_ike ikev2-reauth 'no'
set vpn ipsec ike-group VR02_ike key-exchange 'ikev2'
set vpn ipsec ike-group VR02_ike lifetime '86400'
set vpn ipsec ike-group VR02_ike mobike 'disable'
set vpn ipsec ike-group VR02_ike proposal 2 dh-group '14'
set vpn ipsec ike-group VR02_ike proposal 2 encryption 'aes256'
set vpn ipsec ike-group VR02_ike proposal 2 hash 'sha256'
set vpn ipsec ipsec-interfaces interface 'eth0'
set vpn ipsec site-to-site peer 10.4.1.2 authentication id '172.2.3.1'
set vpn ipsec site-to-site peer 10.4.1.2 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 10.4.1.2 authentication pre-shared-secret 'salam'
set vpn ipsec site-to-site peer 10.4.1.2 connection-type 'initiate'
set vpn ipsec site-to-site peer 10.4.1.2 force-encapsulation 'enable'
set vpn ipsec site-to-site peer 10.4.1.2 ike-group 'VR02_ike'
set vpn ipsec site-to-site peer 10.4.1.2 ikev2-reauth 'inherit'
set vpn ipsec site-to-site peer 10.4.1.2 local-address '10.2.3.2'
set vpn ipsec site-to-site peer 10.4.1.2 tunnel 0 allow-nat-networks 'disable'
set vpn ipsec site-to-site peer 10.4.1.2 tunnel 0 allow-public-networks 'disable'
set vpn ipsec site-to-site peer 10.4.1.2 tunnel 0 esp-group 'VR02_esp'
set vpn ipsec site-to-site peer 10.4.1.2 tunnel 0 local prefix '10.20.20.0/24'
set vpn ipsec site-to-site peer 10.4.1.2 tunnel 0 remote prefix '10.10.10.0/24'
VyOS host:
vyos@vyos:~$ show vpn ipsec sa
Connection State Up Bytes In/Out Remote address Remote ID Proposal
---------------------- ------- --------- -------------- ---------------- ----------- ---------------------------------------------------------
peer-10.4.1.2-tunnel-0 up 5 minutes 0B/0B 10.4.1.2 N/A AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
vyos@vyos:~$ show vpn ipsec sa verbose
Status of IKE charon daemon (strongSwan 5.7.2, Linux 4.19.142-amd64-vyos, x86_64):
uptime: 5 minutes, since Nov 10 19:32:41 2020
Listening IP addresses:
10.2.3.2
Connections:
peer-10.4.1.2-tunnel-0: 10.2.3.2...10.4.1.2 IKEv2
peer-10.4.1.2-tunnel-0: local: [172.2.3.1] uses pre-shared key authentication
peer-10.4.1.2-tunnel-0: remote: [10.4.1.2] uses pre-shared key authentication
peer-10.4.1.2-tunnel-0: child: 10.20.20.0/24 === 10.10.10.0/24 TUNNEL
Security Associations (1 up, 0 connecting):
peer-10.4.1.2-tunnel-0[1]: ESTABLISHED 5 minutes ago, 10.2.3.2[172.2.3.1]...10.4.1.2[10.4.1.2]
peer-10.4.1.2-tunnel-0[1]: IKEv2 SPIs: 54ea438aa7c7df94_i* 0b5e15548368f594_r, rekeying in 23 hours
peer-10.4.1.2-tunnel-0[1]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
peer-10.4.1.2-tunnel-0{1}: INSTALLED, TUNNEL, reqid 1, ESP in UDP SPIs: cd354e7a_i 43edd033_o
peer-10.4.1.2-tunnel-0{1}: AES_CBC_256/HMAC_SHA2_256_128, 0 bytes_i, 0 bytes_o, rekeying in 43 minutes
peer-10.4.1.2-tunnel-0{1}: 10.20.20.0/24 === 10.10.10.0/24
Cisco:
Switch#show crypto session
Crypto session current status
Interface: Ethernet0/0
Profile: site1_to_site2-profile
Session status: UP-ACTIVE
Peer: 172.2.3.1 port 4500
Session ID: 2
IKEv2 SA: local 10.4.1.2/4500 remote 172.2.3.1/4500 Active
IPSEC FLOW: permit ip 10.10.10.0/255.255.255.0 10.20.20.0/255.255.255.0
Active SAs: 2, origin: crypto map
Switch#
Switch#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 10.4.1.2/4500 172.2.3.1/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 3600/752 sec
IPv6 Crypto IKEv2 SA
Switch#
Keyvan
November 10, 2020, 8:07pm
4
the scheme was wrong the VyOS int ip was correct
In my scheme “R2” do nat 1:1 172.2.3.1 => 10.2.3.2
Keyvan
November 10, 2020, 8:24pm
6
Viacheslav:
show vpn ipsec sa
Great
Keyvan
November 10, 2020, 9:31pm
7
Thanks a lot in my real network I have floating ip and by using “authentication id” the problem has been solved
but in the lab because the ip 10.2.3.2 has been set on my interface and I doing static nat on R2 they have overlapped together and not working
system
November 12, 2020, 9:31pm
8
This topic was automatically closed 2 days after the last reply. New replies are no longer allowed.
![]()