I am experiencing some weird DHCP server behaviour. My VyOS machine has 4 private subnets in different VLANs:
$ sh int
Codes: S - State, L - Link, u - Up, D - Down, A - Admin Down
Interface IP Address S/L Description
--------- ---------- --- -----------
eth0 192.168.0.66/24 u/u WAN
eth1 192.168.1.1/24 u/u LAN
eth1.2 192.168.2.1/24 u/u untrusted
eth1.3 192.168.3.1/24 u/u WiFi_guest
eth1.99 192.168.99.1/24 u/u DMZ
ifb0 - u/u QoS aggregation
lo 127.0.0.1/8 u/u
::1/128
vtun0 172.21.36.27/23 u/u fra-a30.ipvanish.com
vtun1 172.21.32.68/23 u/u ams-a16.ipvanish.com
vtun2 172.21.32.18/23 u/u sto-a05.ipvanish.com
vtun3 172.21.33.22/23 u/u iev-c02.ipvanish.com
vtun4 172.21.34.161/23 u/u nyc-a07.ipvanish.com
On VLANs 1 (native), 2, and 3, VyOS acts as a DHCP server:
$ sh conf com | grep dhcp-server
set service dhcp-server shared-network-name LAN authoritative
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 default-router '192.168.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 lease '7200'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range LAN start '192.168.1.10'
set service dhcp-server shared-network-name LAN subnet 192.168.1.0/24 range LAN stop '192.168.1.99'
set service dhcp-server shared-network-name WiFi_guest authoritative
set service dhcp-server shared-network-name WiFi_guest subnet 192.168.3.0/24 default-router '192.168.3.1'
set service dhcp-server shared-network-name WiFi_guest subnet 192.168.3.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name WiFi_guest subnet 192.168.3.0/24 lease '7200'
set service dhcp-server shared-network-name WiFi_guest subnet 192.168.3.0/24 range WiFi_guest start '192.168.3.10'
set service dhcp-server shared-network-name WiFi_guest subnet 192.168.3.0/24 range WiFi_guest stop '192.168.3.99'
set service dhcp-server shared-network-name untrusted authoritative
set service dhcp-server shared-network-name untrusted subnet 192.168.2.0/24 default-router '192.168.2.1'
set service dhcp-server shared-network-name untrusted subnet 192.168.2.0/24 dns-server '1.1.1.1'
set service dhcp-server shared-network-name untrusted subnet 192.168.2.0/24 lease '7200'
set service dhcp-server shared-network-name untrusted subnet 192.168.2.0/24 range untrusted start '192.168.2.10'
set service dhcp-server shared-network-name untrusted subnet 192.168.2.0/24 range untrusted stop '192.168.2.99'
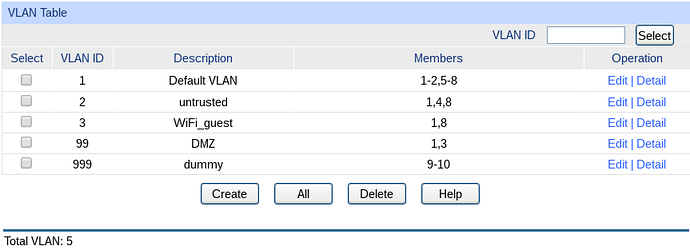
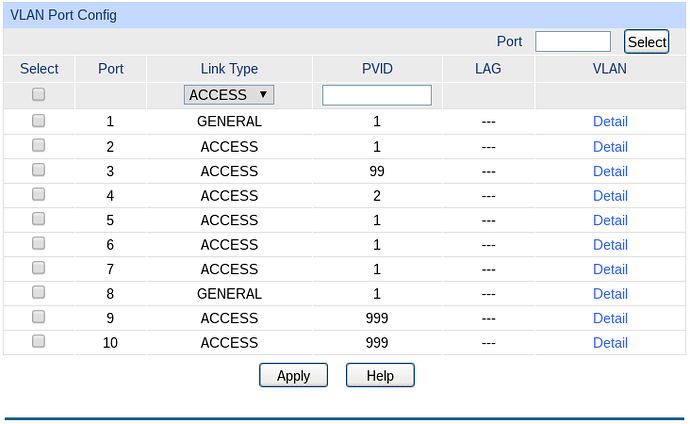
Physically, eth1 connects to port 1 on my switch. My (VLAN-aware) WiFi access point connects to the same switch on port 8. Here is the switch’s VLAN configuration:
And here are the corresponding ports:
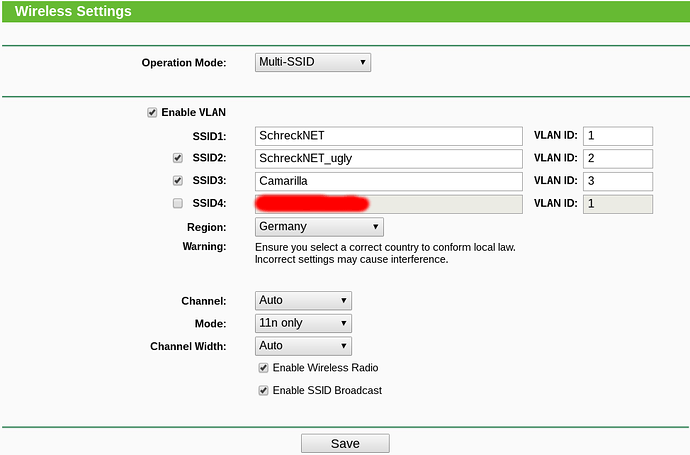
The AP (on which exactly the same setup has worked before with an OPNsense machine) is configured like this:
So, when a device connects to SSID “SchreckNET”, it should receive an IP address in the 192.168.1.0/24 network. --> This works as expected.
When a device connects to SSID “SchreckNET_ugly”, it should receive an IP address in the 192.168.2.0/24 network. --> This DOES NOT work as expected, only in some cases it does.
When a device connects to SSID “Camarilla”, it should receive an IP address in the 192.168.3.0/24 network. --> This DOES NOT work as expected. It never does.
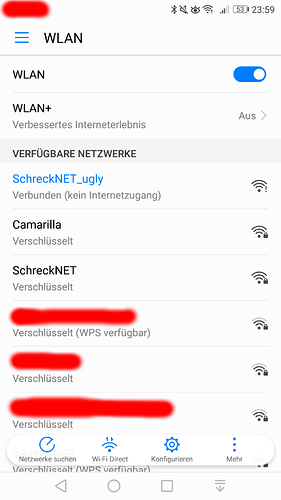
As an example, here is what happens when I connect my phone to “SchreckNET_ugly”:
$ sh dhcp se le
IP address Hardware address Lease expiration Pool Client Name
------------ ------------------ ------------------- --------- ----------------
192.168.2.10 68:54:fd:4c:98:c8 2018/11/14 00:55:07 untrusted [redacted]
192.168.1.10 74:d4:35:10:a5:72 2018/11/14 00:30:41
192.168.1.11 30:05:5c:8c:54:87 2018/11/14 00:36:14 LAN [redacted]
192.168.1.20 50:01:d9:82:06:b7 2018/11/14 00:58:31 LAN Honor_6X [<-- my phone]
Although both 192.168.1.0/24 and 192.168.2.0/24 are allowed to access the internet, a device which is given an address from the “wrong” network is unable to reach anything on the outside. This does not only happen with my phone but also with other people’s phones and laptop computers. Furthermore, whenever a device is given a wrong address, it will be in the 192.168.1.0/24 range.
There is nothing in the log that I can see:
$ sh log dhcp
Nov 13 17:50:42 mewdemstr1 dhcpd:
Nov 13 17:50:42 mewdemstr1 dhcpd: No subnet declaration for eth0 (192.168.0.66).
Nov 13 17:50:42 mewdemstr1 dhcpd: ** Ignoring requests on eth0. If this is not what
Nov 13 17:50:42 mewdemstr1 dhcpd: you want, please write a subnet declaration
Nov 13 17:50:42 mewdemstr1 dhcpd: in your dhcpd.conf file for the network segment
Nov 13 17:50:42 mewdemstr1 dhcpd: to which interface eth0 is attached. **
Nov 13 17:50:42 mewdemstr1 dhcpd:
Nov 13 17:50:42 mewdemstr1 dhcpd:
Nov 13 17:50:42 mewdemstr1 dhcpd: No subnet declaration for eth1.99 (192.168.99.1).
Nov 13 17:50:42 mewdemstr1 dhcpd: ** Ignoring requests on eth1.99. If this is not what
Nov 13 17:50:42 mewdemstr1 dhcpd: you want, please write a subnet declaration
Nov 13 17:50:42 mewdemstr1 dhcpd: in your dhcpd.conf file for the network segment
Nov 13 17:50:42 mewdemstr1 dhcpd: to which interface eth1.99 is attached. **
Nov 13 17:50:42 mewdemstr1 dhcpd:
What is going on here, what am I overlooking?