Hello again all –
I keep running into things that
a) I just don’t understand well enough to get my head around
b) thing are happening that shouldn’t happen
c) a and b
My ignorance is definitely a contributing factor here, but I’m learning…
Since that’s out of the way, here’s what I’m running into today -
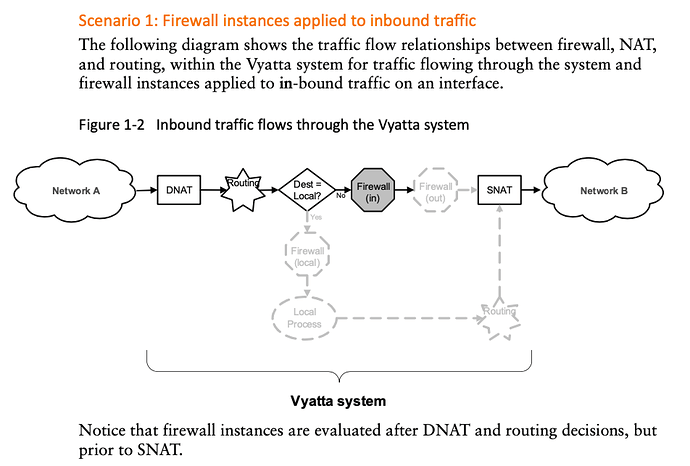
eth0 <- WAN interface with 3 public IPs
eth1(vif 18,19,20)
I made a simple firewall to apply to eth0, allowing some traffic to get to a mail server, and I’m 99% sure that the firewall config is good.
When i apply the firewall to eth0 “in”, I can no longer get to the internet from internal networks. It stopped all traffic from inside -> outside
When I assign it to “eth0 out” I’m able to access the internal mail server from outside, and ICMP is dropped as it should be.
So, firewall works when assigned to “eth0 out” as configured, assigned to “eth0 in” it stops all traffic from inside to outside. It’s completely backwards, and I’m wondering why.
I’m using the latest build from today (5/23)…
Has anyone else run into this? Am I just doing something very wrong, or do the words “in” and “out” have different meanings when it comes to vyos? 
Thanks in advance, again.
–reno