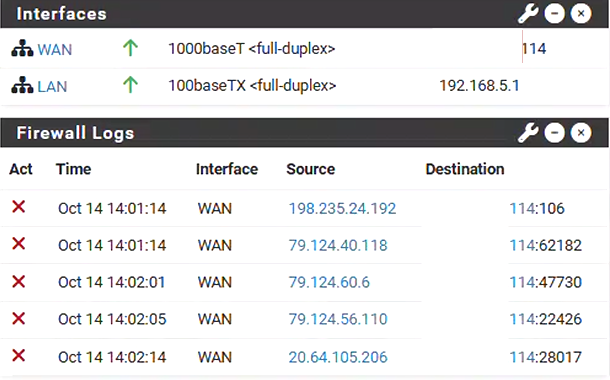
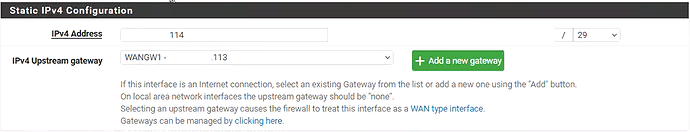
Current Lab Setup:
Right now, my lab network is configured as follows:
Starlink → UDM → Port 1 → VyOS
The VyOS router is running a WireGuard tunnel to CoreTransit, which provides a /29 subnet.
On that subnet:
vyos@vyos:~$ sudo tcpdump -ni eth2 src 134.199.56.114
tcpdump: verbose output suppressed, use -v[v]… for full protocol decode
listening on eth2, link-type EN10MB (Ethernet), snapshot length 262144 bytes
20:50:45.192883 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 212, length 9
20:50:45.725122 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 213, length 9
20:50:46.100266 IP 134.199.56.114.51820 > 134.199.56.1.10253: UDP, length 148
20:50:46.257382 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 214, length 9
20:50:46.789632 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 215, length 9
20:50:47.321895 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 216, length 9
20:50:47.854145 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 217, length 9
20:50:48.386388 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 218, length 9
20:50:48.918654 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 219, length 9
20:50:49.450878 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 220, length 9
20:50:49.968882 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 221, length 9
20:50:50.501134 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 222, length 9
20:50:51.033383 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 223, length 9
20:50:51.196542 IP 134.199.56.114.51820 > 134.199.56.1.10253: UDP, length 148
20:50:51.565641 IP 134.199.56.114 > 134.199.56.113: ICMP echo request, id 11788, seq 224, length 9
I agree I was just trying to get the basic connectivity working before adding any firewall rules or additional configurations.
I also added the static route as you suggested, and it looks like the traffic is attempting to reach the gateway. However, I’m not entirely sure if that’s having the intended effect yet.