Hey,
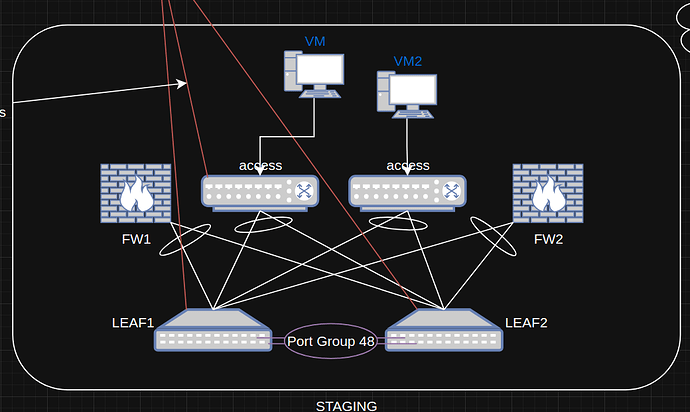
We are currently in the process of migrating from 1.3.8 LTS to 1.4.1, and also moving from a single interface to a bonded interface. Currently cannot route between vlans. In our LAB set up we have the below config.
We have a similar setup on production , but only using eth2 and vifs’ for all VLANS on a trunk port.
Goal is testadmin can reach all vlans, but not the otherway around. Internet with NAT works, DHCP works, DNS works.
VM on vlan1002:
- IP: xx.xx.2.125
Can ping gateway at xx.xx.2.254, can ping xx.xx.4.254 but cannot ping VM2
VM2 on vlan1004:
- IP: xx.xx.4.125
Can ping gateway at xx.xx.4.254, can ping xx.xx.2.254 but cannot ping VM - expected behaviour.
When doing show firewall while running a ping on VM -> VM2 and VM2 -> VM I don’t see any packets hitting Firewall name VLAN1002-LOCAL or VLAN1004-IN or VLAN1004-LOCAL
I can see the icmp echo requests reach bond0.1002 from VM and bond0.1004 from VM2
vyos@firewall-staging-1# run monitor traffic interface bond0.1002 filter icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on bond0.1002, link-type EN10MB (Ethernet), snapshot length 262144 bytes
15:10:34.961363 IP 10.42.2.125 > 10.42.4.125: ICMP echo request, id 10936, seq 7, length 64
Any help diagnosing this would be appreciated.
Thanks
Stripped config
# Firewall groups
set firewall group network-group NET-RFC1918 network 'xxx.xxx.0.0/8'
set firewall group network-group NET-RFC1918 network 'xxx.xxx.0.0/12'
set firewall group network-group NET-RFC1918 network 'xxx.xxx.0.0/16'
set firewall group network-group NET-VLAN2 network 'xxx.xxx.2.0/24'
set firewall group network-group NET-VLAN3 network 'xxx.xxx.3.0/24'
set firewall group network-group NET-VLAN1002 network 'xxx.xxx.2.0/24'
set firewall group network-group NET-VLAN1004 network 'xxx.xxx.4.0/24'
set firewall group network-group NET-VLAN1009 network 'xxx.xxx.9.0/24'
set firewall group network-group NET-VLAN1016 network 'xxx.xxx.16.0/22'
set firewall group network-group NET-VLAN1020 network 'xxx.xxx.20.0/22'
set firewall group network-group NET-VLAN1066 network 'xxx.xxx.66.0/24'
set firewall group network-group NET-VLAN4000 network 'xxx.xxx.27.224/29'
set firewall group network-group NET-VLAN4001 network 'xxx.xxx.241.224/29'
# VLAN1002 Firewall
set firewall ipv4 name VLAN1002-LOCAL default-action 'drop'
set firewall ipv4 name VLAN1002-LOCAL description 'firewall ipv4 Access for VLAN1002 (testadmin)'
set firewall ipv4 name VLAN1002-LOCAL rule 1010 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1010 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1010 log
set firewall ipv4 name VLAN1002-LOCAL rule 1010 state 'established'
set firewall ipv4 name VLAN1002-LOCAL rule 1010 state 'related'
set firewall ipv4 name VLAN1002-LOCAL rule 1011 action 'drop'
set firewall ipv4 name VLAN1002-LOCAL rule 1011 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1011 log
set firewall ipv4 name VLAN1002-LOCAL rule 1011 state 'invalid'
set firewall ipv4 name VLAN1002-LOCAL rule 1020 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1020 icmp type-name 'echo-request'
set firewall ipv4 name VLAN1002-LOCAL rule 1020 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1020 log
set firewall ipv4 name VLAN1002-LOCAL rule 1020 protocol 'icmp'
set firewall ipv4 name VLAN1002-LOCAL rule 1020 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1030 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1030 destination port '67'
set firewall ipv4 name VLAN1002-LOCAL rule 1030 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1030 log
set firewall ipv4 name VLAN1002-LOCAL rule 1030 protocol 'udp'
set firewall ipv4 name VLAN1002-LOCAL rule 1030 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1040 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1040 destination port '53'
set firewall ipv4 name VLAN1002-LOCAL rule 1040 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1040 log
set firewall ipv4 name VLAN1002-LOCAL rule 1040 protocol 'tcp_udp'
set firewall ipv4 name VLAN1002-LOCAL rule 1040 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1050 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1050 destination port '123'
set firewall ipv4 name VLAN1002-LOCAL rule 1050 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1050 log4
set firewall ipv4 name VLAN1002-LOCAL rule 1050 protocol 'udp'
set firewall ipv4 name VLAN1002-LOCAL rule 1050 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1060 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1060 destination port '1194'
set firewall ipv4 name VLAN1002-LOCAL rule 1060 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1060 log
set firewall ipv4 name VLAN1002-LOCAL rule 1060 protocol 'udp'
set firewall ipv4 name VLAN1002-LOCAL rule 1060 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 destination port '647'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 log
set firewall ipv4 name VLAN1002-LOCAL rule 1080 protocol 'tcp'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 source address 'xxx.xxx.2.253'
set firewall ipv4 name VLAN1002-LOCAL rule 1080 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 destination port '20022'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 log
set firewall ipv4 name VLAN1002-LOCAL rule 1101 protocol 'tcp'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 source group network-group 'NET-VLAN1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1101 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 destination port '20022'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 log
set firewall ipv4 name VLAN1002-LOCAL rule 1102 protocol 'tcp'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 source group network-group 'NET-VLAN3'
set firewall ipv4 name VLAN1002-LOCAL rule 1102 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 destination port '20022'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 log
set firewall ipv4 name VLAN1002-LOCAL rule 1103 protocol 'tcp'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 source address 'xxx.xxx.2.0/24'
set firewall ipv4 name VLAN1002-LOCAL rule 1103 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 destination port '20022'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 log
set firewall ipv4 name VLAN1002-LOCAL rule 1104 protocol 'tcp'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 source address 'xxx.xxx.3.0/24'
set firewall ipv4 name VLAN1002-LOCAL rule 1104 state 'new'
set firewall ipv4 name VLAN1002-LOCAL rule 1110 action 'accept'
set firewall ipv4 name VLAN1002-LOCAL rule 1110 destination port '161'
set firewall ipv4 name VLAN1002-LOCAL rule 1110 inbound-interface name 'bond0.1002'
set firewall ipv4 name VLAN1002-LOCAL rule 1110 log
set firewall ipv4 name VLAN1002-LOCAL rule 1110 protocol 'udp'
set firewall ipv4 name VLAN1002-LOCAL rule 1110 source group network-group 'NET-VLAN1002'
# VLAN1004 Firewall
set firewall ipv4 name VLAN1004-IN rule 10 action 'accept'
set firewall ipv4 name VLAN1004-IN rule 10 description 'enable established & related for VLAN 1004'
set firewall ipv4 name VLAN1004-IN rule 10 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-IN rule 10 state 'established'
set firewall ipv4 name VLAN1004-IN rule 10 state 'related'
set firewall ipv4 name VLAN1004-IN rule 11 action 'drop'
set firewall ipv4 name VLAN1004-IN rule 11 description 'drop invalid packets for VLAN 1004'
set firewall ipv4 name VLAN1004-IN rule 11 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-IN rule 11 state 'invalid'
set firewall ipv4 name VLAN1004-IN rule 9990 action 'drop'
set firewall ipv4 name VLAN1004-IN rule 9990 description 'Drop packets from VLAN1004 to rfc1918 networks'
set firewall ipv4 name VLAN1004-IN rule 9990 destination group network-group 'NET-RFC1918'
set firewall ipv4 name VLAN1004-IN rule 9990 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-IN rule 9990 state 'new'
set firewall ipv4 name VLAN1004-LOCAL default-action 'drop'
set firewall ipv4 name VLAN1004-LOCAL description 'firewall ipv4 Access for VLAN1004 (testoffice)'
set firewall ipv4 name VLAN1004-LOCAL rule 1010 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1010 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1010 log
set firewall ipv4 name VLAN1004-LOCAL rule 1010 state 'established'
set firewall ipv4 name VLAN1004-LOCAL rule 1010 state 'related'
set firewall ipv4 name VLAN1004-LOCAL rule 1011 action 'drop'
set firewall ipv4 name VLAN1004-LOCAL rule 1011 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1011 log
set firewall ipv4 name VLAN1004-LOCAL rule 1011 state 'invalid'
set firewall ipv4 name VLAN1004-LOCAL rule 1020 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1020 icmp type-name 'echo-request'
set firewall ipv4 name VLAN1004-LOCAL rule 1020 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1020 log
set firewall ipv4 name VLAN1004-LOCAL rule 1020 protocol 'icmp'
set firewall ipv4 name VLAN1004-LOCAL rule 1020 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1030 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1030 destination port '67'
set firewall ipv4 name VLAN1004-LOCAL rule 1030 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1030 log
set firewall ipv4 name VLAN1004-LOCAL rule 1030 protocol 'udp'
set firewall ipv4 name VLAN1004-LOCAL rule 1030 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1040 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1040 destination port '53'
set firewall ipv4 name VLAN1004-LOCAL rule 1040 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1040 log
set firewall ipv4 name VLAN1004-LOCAL rule 1040 protocol 'tcp_udp'
set firewall ipv4 name VLAN1004-LOCAL rule 1040 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1050 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1050 destination port '123'
set firewall ipv4 name VLAN1004-LOCAL rule 1050 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1050 log
set firewall ipv4 name VLAN1004-LOCAL rule 1050 protocol 'udp'
set firewall ipv4 name VLAN1004-LOCAL rule 1050 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1060 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1060 destination port '1194'
set firewall ipv4 name VLAN1004-LOCAL rule 1060 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1060 log
set firewall ipv4 name VLAN1004-LOCAL rule 1060 protocol 'udp'
set firewall ipv4 name VLAN1004-LOCAL rule 1060 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 destination port '647'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 log
set firewall ipv4 name VLAN1004-LOCAL rule 1080 protocol 'tcp'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 source address 'xxx.xxx.4.253'
set firewall ipv4 name VLAN1004-LOCAL rule 1080 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 destination port '20022'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 log
set firewall ipv4 name VLAN1004-LOCAL rule 1101 protocol 'tcp'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 source group network-group 'NET-VLAN1002'
set firewall ipv4 name VLAN1004-LOCAL rule 1101 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 destination port '20022'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 log
set firewall ipv4 name VLAN1004-LOCAL rule 1102 protocol 'tcp'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 source group network-group 'NET-VLAN3'
set firewall ipv4 name VLAN1004-LOCAL rule 1102 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 destination port '20022'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 log
set firewall ipv4 name VLAN1004-LOCAL rule 1103 protocol 'tcp'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 source address 'xxx.xxx.2.0/24'
set firewall ipv4 name VLAN1004-LOCAL rule 1103 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 destination port '20022'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 log
set firewall ipv4 name VLAN1004-LOCAL rule 1104 protocol 'tcp'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 source address 'xxx.xxx.3.0/24'
set firewall ipv4 name VLAN1004-LOCAL rule 1104 state 'new'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 action 'accept'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 destination port '161'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 inbound-interface name 'bond0.1004'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 log
set firewall ipv4 name VLAN1004-LOCAL rule 1110 protocol 'udp'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 source group network-group 'NET-VLAN1002'
set firewall ipv4 name VLAN1004-LOCAL rule 1110 state 'new'
# VRRP
set high-availability vrrp group bond0.1002 address xxx.xxx.2.254/24
set high-availability vrrp group bond0.1002 advertise-interval '1'
set high-availability vrrp group bond0.1002 interface 'bond0.1002'
set high-availability vrrp group bond0.1002 preempt-delay '180'
set high-availability vrrp group bond0.1002 priority '150'
set high-availability vrrp group bond0.1002 vrid '1'
set high-availability vrrp group bond0.1004 address xxx.xxx.4.254/24
set high-availability vrrp group bond0.1004 advertise-interval '1'
set high-availability vrrp group bond0.1004 interface 'bond0.1004'
set high-availability vrrp group bond0.1004 preempt-delay '180'
set high-availability vrrp group bond0.1004 priority '150'
set high-availability vrrp group bond0.1004 vrid '1'
set high-availability vrrp group bond0.4000 address xxx.xxx.27.227/29
set high-availability vrrp group bond0.4000 advertise-interval '1'
set high-availability vrrp group bond0.4000 interface 'bond0.4000'
set high-availability vrrp group bond0.4000 preempt-delay '180'
set high-availability vrrp group bond0.4000 priority '150'
set high-availability vrrp group bond0.4000 vrid '2'
set high-availability vrrp group bond0.4001 address xxx.xxx.241.227/29
set high-availability vrrp group bond0.4001 advertise-interval '1'
set high-availability vrrp group bond0.4001 interface 'bond0.4001'
set high-availability vrrp group bond0.4001 preempt-delay '180'
set high-availability vrrp group bond0.4001 priority '150'
set high-availability vrrp group bond0.4001 vrid '2'
set high-availability vrrp sync-group FIREWALL member 'bond0.4000'
set high-availability vrrp sync-group FIREWALL member 'bond0.4001'
set high-availability vrrp sync-group FIREWALL member 'bond0.1002'
set high-availability vrrp sync-group FIREWALL member 'bond0.1004'
set interfaces bonding bond0 member interface 'eth3'
set interfaces bonding bond0 member interface 'eth2'
set interfaces bonding bond0 mode '802.3ad'
set interfaces bonding bond0 vif 1002 address 'xxx.xxx.2.252/24'
set interfaces bonding bond0 vif 1002 description 'VLAN1002 (testadmin)'
set interfaces bonding bond0 vif 1004 address 'xxx.xxx.4.252/24'
set interfaces bonding bond0 vif 1004 description 'VLAN1004 (testoffice)'
set interfaces bonding bond0 vif 1009 address 'xxx.xxx.9.252/24'
set interfaces bonding bond0 vif 4000 address 'xxx.xxx.255.3/29'
set interfaces bonding bond0 vif 4000 description 'VLAN4000'
set interfaces bonding bond0 vif 4001 address 'xxx.xxx.255.19/29'
set interfaces bonding bond0 vif 4001 description 'VLAN4001'
# NAT
set nat source rule 1252 description 'VLAN1002 (testadmin) via ISP1
set nat source rule 1252 outbound-interface name 'bond0.4000'
set nat source rule 1252 source address 'xxx.xxx.2.0/24'
set nat source rule 1252 translation address 'xxx.xxx.27.227'
set nat source rule 1254 description 'VLAN1004 (testoffice) via ISP1'
set nat source rule 1254 outbound-interface name 'bond0.4000'
set nat source rule 1254 source address 'xxx.xxx.4.0/24'
set nat source rule 1254 translation address 'xxx.xxx.27.227'
set nat source rule 5252 description 'VLAN1002 (testadmin) via ISP2'
set nat source rule 5252 outbound-interface name 'bond0.4001'
set nat source rule 5252 source address 'xxx.xxx.2.0/24'
set nat source rule 5252 translation address 'xxx.xxx.241.227'
set nat source rule 5254 description 'VLAN1004 (testoffice) via ISP3'
set nat source rule 5254 outbound-interface name 'bond0.4001'
set nat source rule 5254 source address 'xxx.xxx.4.0/24'
set nat source rule 5254 translation address 'xxx.xxx.241.227'
# dhcp-server
set service dhcp-server high-availability mode 'active-active'
set service dhcp-server high-availability name 'VLAN1002'
set service dhcp-server high-availability remote 'xxx.xxx.2.253'
set service dhcp-server high-availability source-address 'xxx.xxx.2.252'
set service dhcp-server high-availability status 'primary'
set service dhcp-server shared-network-name xxxxxx authoritative
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 default-router 'xxx.xxx.2.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 domain-name xxxxxx
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 enable-failover
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 lease '86400'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 name-server 'xxx.xxx.2.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 ntp-server 'xxx.xxx.2.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 range 0 start 'xxx.xxx.2.1'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.2.0/24 range 0 stop 'xxx.xxx.2.250'
set service dhcp-server shared-network-name xxxxxx authoritative
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 default-router 'xxx.xxx.4.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 domain-name xxxxxx
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 enable-failover
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 lease '86400'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 name-server 'xxx.xxx.4.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 ntp-server 'xxx.xxx.4.254'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 range 0 start 'xxx.xxx.4.1'
set service dhcp-server shared-network-name xxxxxx subnet xxx.xxx.4.0/24 range 0 stop 'xxx.xxx.4.250'
# DNS
set service dns forwarding allow-from 'xxx.xxx.2.0/24'
set service dns forwarding allow-from 'xxx.xxx.4.0/24'
set service dns forwarding allow-from 'xxx.xxx.2.0/24'
set service dns forwarding allow-from 'xxx.xxx.4.0/24'