Hello, we are currently testing the following scenario to see if we can use the VyOS system in production.
For hardware reasons we decided to run VyOS on AWS, from the lab using a MikroTik I configured it as OpenVPN Client and VyOS as OpenVPN in client mode, both in TAP mode with the purpose of connecting to the MikroTik and the broadcast or DHCP request get to VyOS.
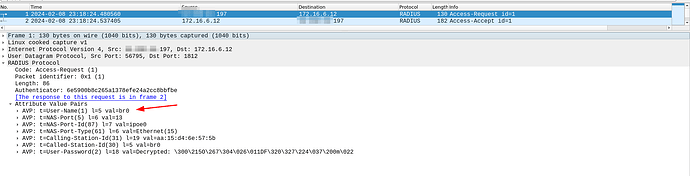
In VyOS, the requests are received and an IPoE service is configured pointing to an external Radius server, but the detail is that the username arrives with the name of the interface instead of the mac address or something different that can be configured Which is where I’m stuck.
Capture on Radius server
interfaces {
bridge br0 {
member {
interface vtun10 {
}
}
mtu 1557
}
ethernet eth0 {
address dhcp
address dhcpv6
hw-id 12:38:f3:b2:85:51
}
loopback lo {
}
openvpn vtun10 {
device-type tap
local-port 1194
mode server
persistent-tunnel
protocol udp
server {
client mikrotik1 {
ip 100.67.67.129
}
subnet 100.67.67.128/25
}
tls {
ca-certificate openvpn_vtun10_1
certificate openvpn_vtun10
dh-params openvpn_vtun10
}
}
}
pki {
ca openvpn_vtun10_1 {
certificate xxxxxxxxxxx
}
certificate openvpn_vtun10 {
certificate xxxxxxxxxxx
private {
key ****************
}
}
dh openvpn_vtun10 {
parameters xxxxxxxxx
}
}
protocols {
static {
route 100.67.67.128/25 {
interface vtun10 {
}
}
}
}
service {
ipoe-server {
authentication {
mode radius
radius {
accounting-interim-interval 120
preallocate-vif
server x.x.x.x {
key ****************
}
}
}
interface br0 {
client-subnet 100.67.67.128/25
}
name-server 8.8.8.8
name-server 8.8.4.4
}
}
Can you configure the username and the rest of the radius protocols via the command line? or is a custom script required?
And if it is a script, do you have any documentation on how to do it?
Checking the /var/log/messages file shows the following when addressing:
Feb 13 07:20:57 vyos01 accel-ipoe: ipoe0:: radius:packet: unknown attribute received (0.92)
Feb 13 07:20:57 vyos01 accel-ipoe: ipoe0:: radius:packet: vendor 26 not found
Feb 13 07:20:57 vyos01 accel-ipoe: ipoe0:br0: ipoe: no free IPv6 address
zqz@vyos01.dev:~$ show ipoe-server sessions
ifname | username | calling-sid | ip | rate-limit | type | comp | state | uptime
--------+----------+-------------------+---------------+------------+------+------+--------+----------
ipoe0 | br0 | aa:15:d4:6e:57:5b | 100.67.67.130 | | ipoe | | active | 00:17:44
zqz@vyos01.dev:~$