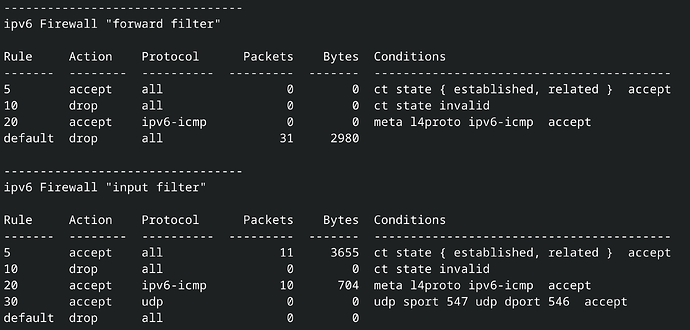
i translated the rules from this page to the new firewall syntax. But it does not work.
set firewall ipv6 forward filter default-action ‘drop’
set firewall ipv6 forward filter rule 5 action ‘accept’
set firewall ipv6 forward filter rule 5 state established
set firewall ipv6 forward filter rule 5 state related
set firewall ipv6 forward filter rule 10 action ‘drop’
set firewall ipv6 forward filter rule 10 state invalid
set firewall ipv6 forward filter rule 20 action ‘accept’
set firewall ipv6 forward filter rule 20 protocol ‘ipv6-icmp’
set firewall ipv6 input filter default-action ‘drop’
set firewall ipv6 input filter rule 5 action ‘accept’
set firewall ipv6 input filter rule 5 state established
set firewall ipv6 input filter rule 5 state related
set firewall ipv6 input filter rule 10 action ‘drop’
set firewall ipv6 input filter rule 10 state invalid
set firewall ipv6 input filter rule 20 action ‘accept’
set firewall ipv6 input filter rule 20 protocol ‘ipv6-icmp’
set firewall ipv6 input filter rule 30 action ‘accept’
set firewall ipv6 input filter rule 30 destination port ‘546’
set firewall ipv6 input filter rule 30 protocol ‘udp’
set firewall ipv6 input filter rule 30 source port ‘547’
the above basic barebones firewall will not work unless I remove
set firewall ipv6 forward filter default-action ‘drop’
can anyone please explain why? I’d like to follow best practice and use default drop.
i have a very basic two interface config:
set interfaces ethernet eth1 address ‘dhcp’
set interfaces ethernet eth1 address ‘dhcpv6’
set interfaces ethernet eth1 description ‘OUTSIDE’
set interfaces ethernet eth1 dhcpv6-options pd 0 interface eth2
set interfaces ethernet eth2 address ‘192.168.1.1/24’
set interfaces ethernet eth2 description ‘INSIDE’
everything gets dropped in the forward chain but not the input chain?